Identity and Access Management (IAM)
Access Request Management System
IDHub is a modern Identity and Access Management (IAM) system built to simplify and secure the way organizations handle user access. It streamlines the entire process—from request to approval—allowing both internal and external users to gain access to critical resources in minutes, not days.
With IDHub, requesters can easily submit access requests through a clean, intuitive interface. Approvers can review, approve, or deny requests instantly with a single click, eliminating delays and manual workflows.
Requesting Access
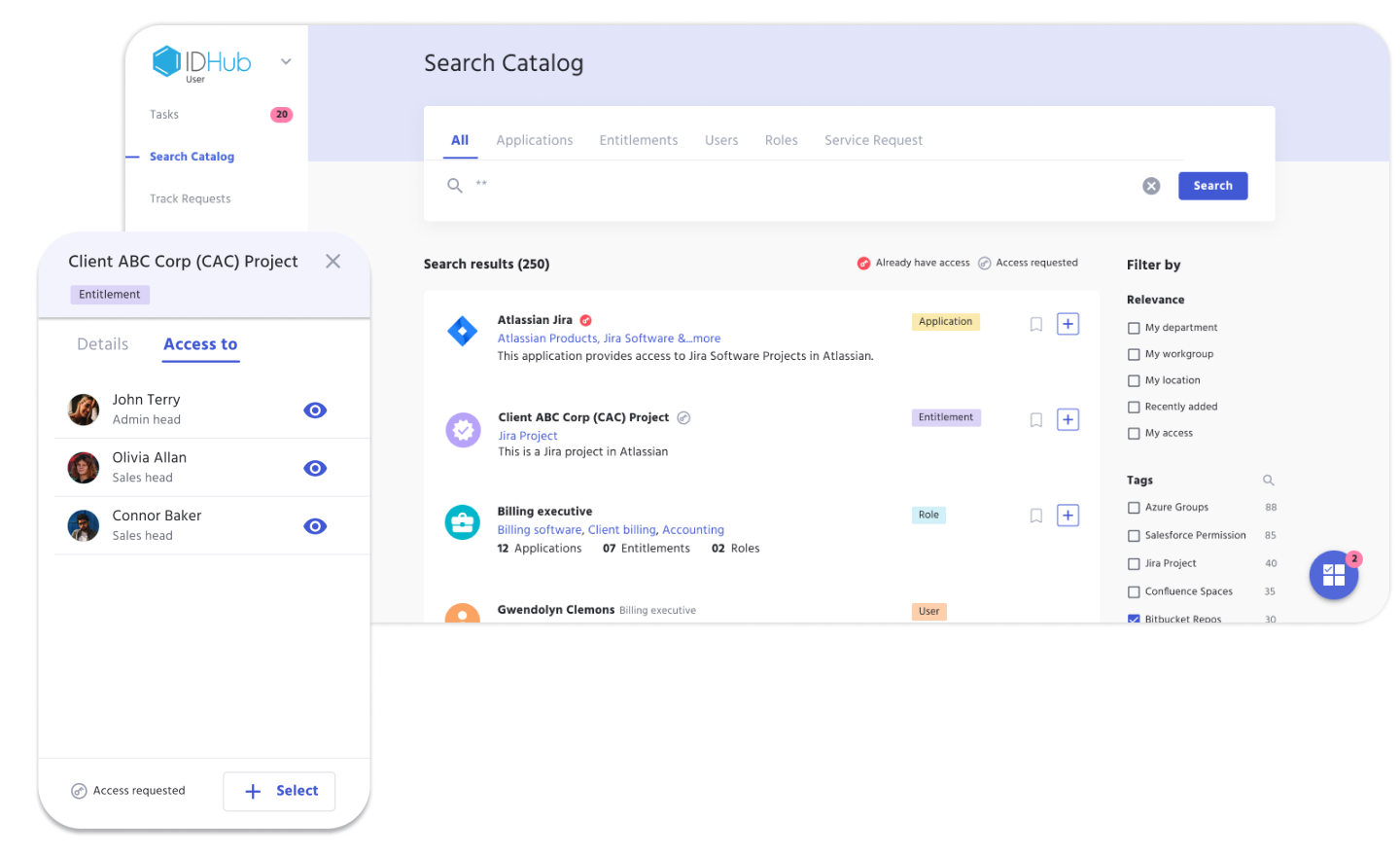
Requesting for resources is simple and transparent for the end-user, making it easy to understand what stage their request is in, and what the current approval status is, at any point in the access request process.
IDHub houses all resources, Applications, Entitlements, Roles, and Service Requests, on a centrally located Search Catalog page, providing users the ability to request access for themselves, or on behalf of another user, with their privileged credentials.
Users have the ability to view the complete trail for every request submitted, from their Track Requests page.
Access Request for Entitlements
Every application has corresponding permissions, or Entitlements, ready to request within the app.
Entitlement Management assists organizations with fully controlling permissions within applications, allowing for efficient user access requests, ensuring requests are made for the correct permissions within an application.
Entitlements can be configured to follow approval workflows different from the workflows assigned to the app itself.
Just In Time Access
Time-Based Access adds another layer of control, allowing admins or users to define specific time-frames for temporary access.
Access Request for Roles
For complex environments managing multiple applications and user types, IDHub uses Roles to ensure users get only the access they need—nothing more, nothing less.
Roles can also be requested from the same centrally located, Search Catalog page.
When viewing a role, users can see all the resources that correspond to that specific role.
Each individual resource within the role is granted to the user who requested access, automatically, upon approval.
Approval Workflows
Every Application, Entitlement, and Role, follows a specific approval request process, known as the Approval Workflow.
Approval Workflows can be simple, like automatic access once requested, or complicated for high-risk resources, requiring multiple approvals and Access Reviews before access is granted.
Custom Workflows
IDHub allows admins to design Custom Workflows, low-code and easily created with our drag-and-drop functionality.
Custom workflows are tailored to the organization needs, fully managing any level of access control to all users.
Custom workflows provide a layer of protection that help ensure organizational compliance mandates, regulatory requirements, privacy regulations, and prevent access by users with malicious intent, fully controlling access request management.
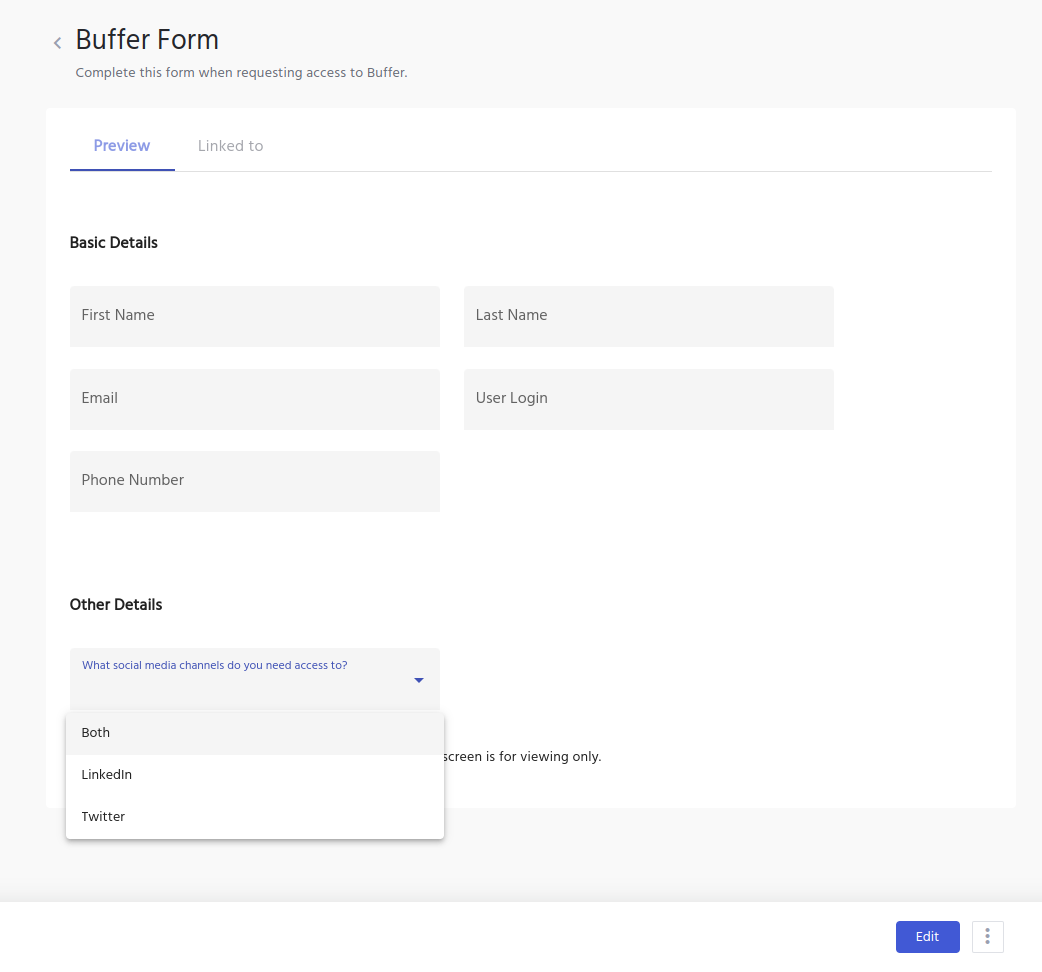
System Access Request Forms
A system access request form is a key part of identity and access management (IAM), ensuring access is granted based on verified user data and policy rules.
IDHub enhances this with customs forms—fully customizable access request forms that collect all necessary user attributes, business details, and application-specific data for accurate and secure provisioning.
This approach not only speeds up access approvals, but also strengthens compliance and reduces errors in account creation.
Access Request Management
The goal of an IAM access request management system is to efficiently and securely manage user access, minimize the risk of unauthorized access, and ensure compliance with organizational policies and regulatory requirements.
Requesting access in IDHub helps organizations maintain a balance between granting users the access they need to perform their job functions, while mitigating the risk of security breaches.
Take control of your user access requests with IDHub. Take a peek at IDHub, Tour it yourself with no obligations.
Compliance Tools for Cyber Security
Cyber Security Tools

Access Control Policy Template for Organizations
Utilize our free Access Control Policy Template to help establish a healthy framework for your access control. Easy to customize and share with your team.
Cybersecurity Assessment Template
Discover why cybersecurity assessments are vital for regulated industries—plus a free template to strengthen security, manage risk, and stay compliant.

Application Onboarding Checklist
Learn about Application Onboarding essentials, and grab a copy of our free Google form, 36 question, application onboarding questionnaire to customize!