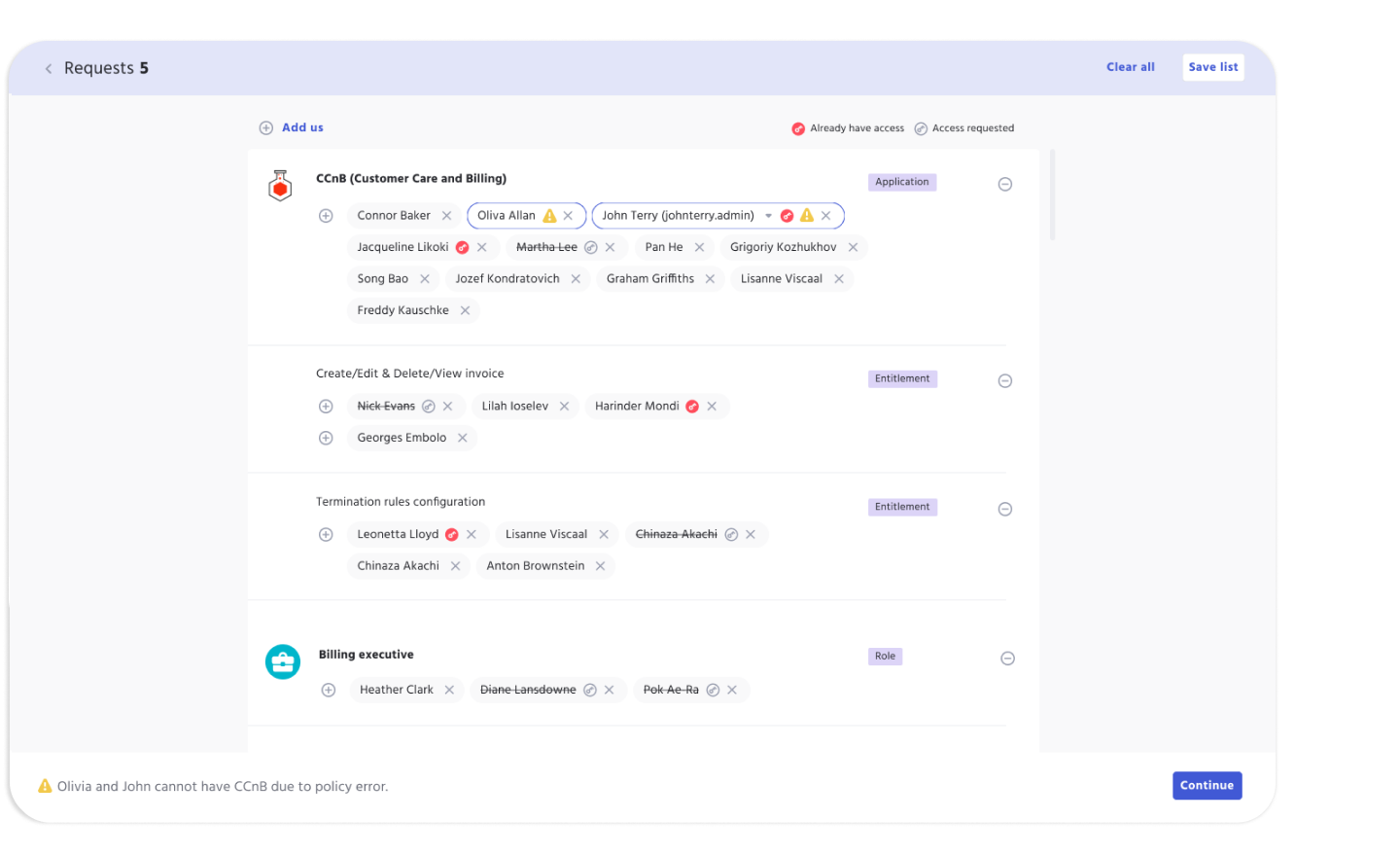
Access Policy
An access policy in IDHub is a set of rules and permissions that govern the level of access granted to users or entities for specific resources within an organization's infrastructure or systems.
- Purpose: Our Access policies ensure that access to resources is granted appropriately and securely, based on the principle of least privilege. They define what actions or operations users can perform on specific resources.
- Scope: Access policies focus on defining and enforcing permissions and access control rules at a granular level, specifying who can access what resources and what actions they can perform.
- Implementation: Our Access policy involves policy languages, such as JSON-based policies in AWS IAM or policy definition language (PDL) in Entra ID (Formerly Azure Active Directory) RBAC, to define and manage access rules.
Access Policy in IDHub
Access Policy is performed in IDHub in multiple ways. IDHub clearly defines policies for organizations at API level and perform validations so no breach of policy is made if access grant is not permitted by the organization policies. Below is the brief overview of features involved in Access policy.
Control Access
Role-Based Access Control (RBAC)
IDHub RBAC associates permissions with roles and assigns roles to users or groups. Access policies in IDHub includes RBAC capabilities out of the box, allowing administrators to define roles and assign appropriate permissions to those roles.
Attribute Sync
Attribute-Based Control (ABAC)
IDHub ABAC considers attributes of users, resources, and environmental factors to make access control decisions. IDHub support ABAC policies, enabling administrators to define complex access rules based on user attributes, resource attributes, and other contextual information.
Authorization
Fine-Grained Permissions
Access policies in IDHub allow administrators to define fine-grained permissions that specify what actions or operations a user or application can perform on specific resources. These permissions are defined at the API level and at data object level.
Construct
Policy Definition
IDHub provides an option to define organizations access policies. Policies can be based on various factors, such as user roles, attributes, group membership, resource types, and environmental context
Time Based Control
Conditional Policies
IDHub Access policies support conditional logic, allowing administrators to define access rules based on specific conditions or triggers. For example, policies can be set to allow access only during specific time periods, based on IP addresses, or in response to certain events.
Integrations
Policy Evaluation and Enforcement
IDHub has mechanisms to evaluate and enforce access policies during runtime. The enforcement mechanisms includes integration with authentication mechanisms, API gateways, or other security enforcement points.
Segregation of Duties
Segregation of Duties in IDHub refers to the practice of separating incompatible or conflicting tasks or responsibilities among different individuals or roles within an organization.
- Purpose: SoD aims to prevent conflicts of interest, reduce the risk of fraud, and ensure proper checks and balances by ensuring that no single user or role has too much control or authority over critical processes or systems.
- Scope: SoD focuses on defining and enforcing organizational policies and controls to prevent the assignment of conflicting duties to a single user or role. It involves separating key tasks or functions that should be performed by different individuals to maintain accountability and prevent abuse of privileges.
- Implementation: SoD is implemented through a combination of organizational policies, role-based access controls, and workflow processes. It involves defining and assigning roles and responsibilities in a way that ensures segregation and prevents conflicts.
A common example is when accountants are handling money and they have separate departments that procure funds from vendors and a different department that distributes funds to vendors. These are two different set of permissions for two different department or teams. By making the distinction in IDHub Workflow across these two different teams, organizations can avoid a single party committing fraud and thus minimizing the risk of a crime.
Segregation of Duties in IDHub
Segregation of Duties is performed in IDHub in multiple ways. IDHub not only defines policies on a high as well as granular level, but also allows to perform validations so no two permissions can be assigned to an identity if it is not permitted by the organization policies. Below is the brief overview of features involved in SoD in IDHub.
Workflows
Rule-Based Policies
The IDHub Workflow Condition Node allows administrators to define rule-based policies that specify which duties or roles should be segregated. These policies can be customized based on the organization's specific requirements and compliance standards.
Predefined Flows
OOTB Templates
IDHub offers predefined Workflow templates based on common industry best practices or regulatory requirements that has common SoD rules. These templates provide a starting point for organizations to implement segregation of duties policies effectively.
Role Assignments
Conflict Detection
The IDHub SoD feature actively scans the access assignments and permissions across different roles and users to identify potential conflicts. It detects instances where a user's assigned roles or permissions may result in conflicting duties.
SoD Violations
Exploitation of user access by an individual or a set of individuals which are not allowed by company policy and government regulations is a breach of policy and is considered an SoD violation. However, violations can be accidental as well as gradual. Violations can happen when a user gains access to certain stage of access by a workflow that they should not have access to. This in turn, enhances user ability to perform actions that the organization has deliberately prohibited.
Some of the things that a user can exploit with this unwanted access are:
- To steal funds from the employer by entering vendor invoices, vendor payment approvals, product ordering and accounting inventory manipulations
- To take part in corporate espionage to transfer trade secrets to competitors
- Deliberately harm peers due to something that happened in the past
- Falsify records and earning forecasts like Enron scandal
SoD, when applied correctly, uses our robust workflow capability to internally control and prevent these conflicts of interest and improve security and compliance for your organization.
Why SoD is important?
Separation-of-duties inherently improves compliance for organization as it removes the possibility of single-source of truth and control. It also encourages internal process evaluation. By controlling each user’s access to provide only what is required, organizations can better manage their risk.
Of course, this ordeal can quickly become complicated, especially with an ever growing complexities in the business, so organizations should create a set of standard rules for each type of activity (e.g., accounting, management, etc.) which is a limited set and not exhaustive. SoD will allow you to detect and auto-address violations that occur upon user request early—in adherence to specific compliance regulations, like SOX or GDPR—to avoid more bigger issues moving forward.
Finally, practicing continual audit is crucial for an effective cybersecurity implementation. With the proper software tools and processes such as IDHub's Workflow based SoD risk analysis and detailed audit controls, organizations can anticipate all possible violations and identify and correct unseen violations quickly and efficiently.
Compliance Tools for Cyber Security
Cyber Security Tools

Access Control Policy Template for Organizations
Utilize our free Access Control Policy Template to help establish a healthy framework for your access control. Easy to customize and share with your team.
Cybersecurity Assessment Template
Discover why cybersecurity assessments are vital for regulated industries—plus a free template to strengthen security, manage risk, and stay compliant.

The Price of Identity Access Management
Why is IAM so expensive? Learn how the benefits outweigh the initial price tag of IAM in our blog post.