What is API-first?
API-first is a general development philosophy that refers to an approach in software development where the design and creation of APIs (Application Programming Interface) take precedence before building other components of an application.
This methodology ensures that a well-defined and stable API serves as the foundation for seamless communication between different software modules, promoting modularization and reusability.
IAM API
IAM API-first applies the API-first approach to Identity and Access Management (IAM) systems, ensuring that the IAM system is built with a strong and flexible API foundation for managing user identities and access controls.
IAM API-first tailors the API-first approach to the unique requirements and challenges of Identity and Access Management systems. It signifies the importance of prioritizing APIs in the design and implementation of IAM solutions to create a secure, flexible, and well-integrated identity management framework.
Triggers, APIs and Webhooks
API-first Strategy
Event Based Triggers in IAM specifically refers to utilizing these APIs to automatically initiate actions or processes in response to predefined events, such as user authentication, authorization requests, or alterations in access permissions.
It represents a targeted implementation within the broader IAM API-first strategy, enhancing the system's dynamic and automated capabilities by leveraging APIs to respond intelligently to specific events in real-time.
Examples of IAM Event based triggers include user login events, role modifications, and access request approvals, which can be programmatically handled to enforce security policies and maintain compliance.
API Access Control
IDHub allows you to monitor and respond to specific events or actions related to API usage within our product. These triggers enable you to implement additional security measures and automate certain actions based on the occurrence of predefined events.
Our IAM solution is slightly different that other IAM solutions in API security. We provide additional flexibility to change user data based on individual needs without compromising the security protocols.
Below are some common capabilities associated with Event triggers.
Observational
Event Monitoring
API triggers enable you to monitor various events and actions related to API usage, such as authentication attempts, access requests, data modifications, and other security-relevant activities.
API Rules
Rule-Based Actions
You can define rules or conditions that, when met, trigger specific actions or responses. For example, you might set up a rule that triggers an alert when a user attempts multiple failed login attempts within a certain time-frame.
Attacks
Threat Detection and Prevention
API triggers can be used to detect and prevent potential threats or suspicious activities. By monitoring API events, you can identify patterns indicative of unauthorized access attempts, brute force attacks, or other malicious behavior.
Emails and SMS
Real-Time Alerts and Notifications
When an API trigger event occurs, you can configure the system to generate real-time alerts or notifications. These alerts can be delivered via email, SMS, or integrated with incident response systems to ensure timely action.
Revoke Access
Access Control and Authorization
API triggers can be leveraged to enforce access control and authorization policies. For example, you can define triggers that automatically revoke API access for a user or application if certain conditions are met, such as a security breach or violation of usage policies.
Node-Based Workflows
Workflow Orchestration
API triggers can be used to automate workflows and execute predefined actions based on specific events. For instance, you might configure a trigger that initiates a workflow to revoke access privileges for a user who has been inactive for a specified period.
API Auth
User Authentication API
API Keys
API keys are unique identifiers assigned to users or applications to authenticate their access to the API. The API key is included in the API request as a parameter or header.
OAuth 2.0
IDHub uses OAuth 2.0 for authentication and authorization. It enables users or applications to obtain access tokens from an authorization server by presenting their credentials.
OpenID Connect (OIDC)
IDHub Keycloak and HashiCorp's OIDC capability in its authentication layer which is built on top of OAuth 2.0. OIDC enables the API to receive an ID token containing user claims.
JSON Web Tokens (JWT)
IDHub also uses JWT self contained access tokens in API Authentication. The tokens are digitally signed, allowing the API to verify their authenticity and integrity.
REST APIs
How to construct your API
Below are the key details of IDHub APIs:
- The IDHub API based on REST. Our API has predictable resource-oriented URLs, accepts JSON request bodies, returns JSON responses, and uses standard HTTP response codes, authentication, and verbs.
- The IDHub API uses OIDC auth keys to authenticate requests. You can view and manage your API keys in IDHub Developer Guide
- Your API keys carry many privileges, so be sure to keep them secure! Do not share your secret API keys in publicly accessible areas such as GitHub, client-side code, and so forth.
- All API requests must be made over HTTPS. Calls made over plain HTTP will fail. API requests without authentication will also fail.
- You can also set a per-request key with an option. This is often useful for Connected Applications that use multiple API keys during the lifetime of a process.
Compliance Tools for Cyber Security
Cyber Security Tools
Cybersecurity Assessment Template
Discover why cybersecurity assessments are vital for regulated industries—plus a free template to strengthen security, manage risk, and stay compliant.

Access Control Policy Template for Organizations
Utilize our free Access Control Policy Template to help establish a healthy framework for your access control. Easy to customize and share with your team.
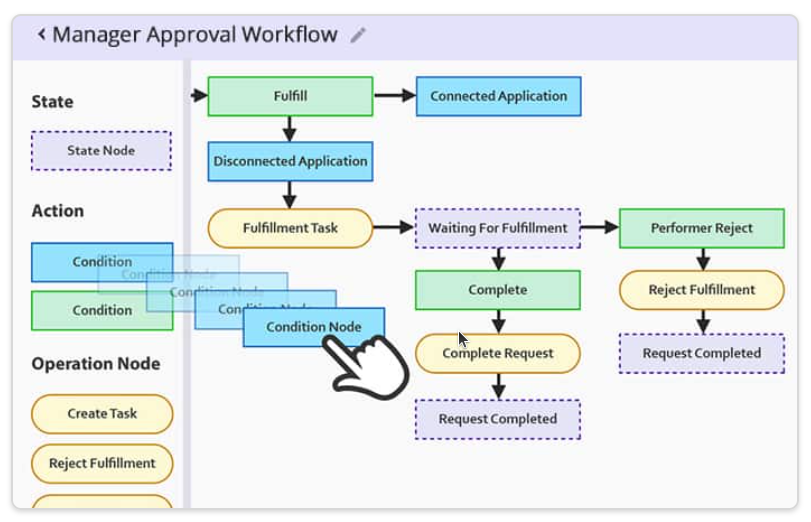
Customizable Approval Workflow Templates
Download our most common Workflow Templates, including editable versions in Visio, SVG, and PDF formats. Completely free to you.