Visualize Security, Simplify Compliance
Identity Analytics
Move from heavy identity data to clear, actionable insights in minutes. With IDHub you can integrate with your analytics platform and trailblaze your access audits, enabling an entire organization to ask better questions on their access decisions faster.
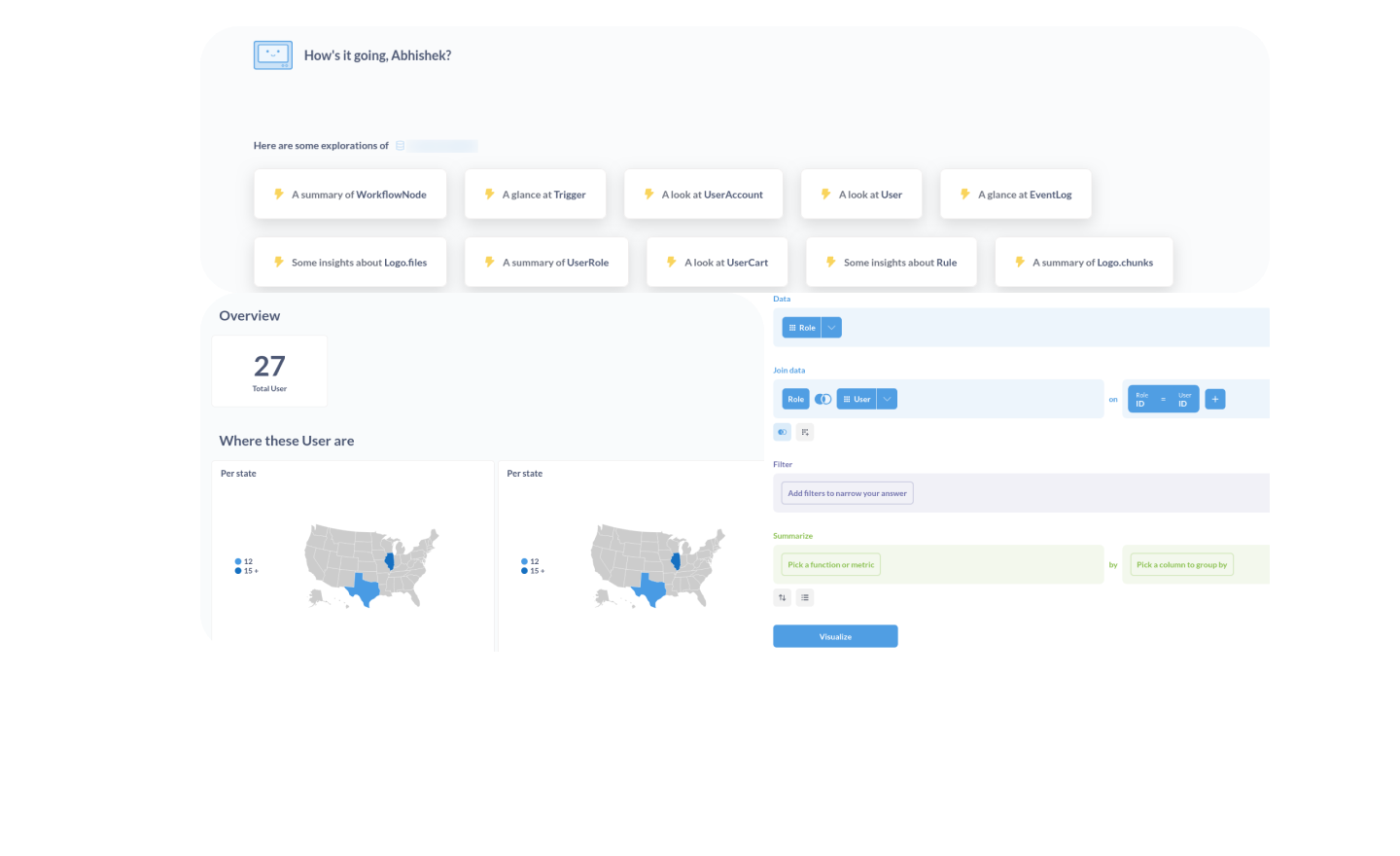
Trailblaze your access audits with IDHub Analytics.
Integrate With Your Analytics Platform

Elasticsearch
Integrate IDHub with Elastic which indexes identity events instantly for real-time monitoring and tracking.

Metabase
Integrate IDHub with Metabase which enables non-technical teams to create customized dashboards and reports with visual query builder.

Jaspersoft
Integrate IDHub with JasperReports to get detailed reports for your IDHub tenant data, enabling compliance and audit reporting.

Redash
Integrate IDHub with Redash for ad-hoc queries and shareable visualizations, enabling interactive analysis of IDHub event and datasets.
Connect with Your Analytics Platform
IDHub Analytics
IDHub supports integrating with your external analytics solution for example, Elasticsearch or Metabase in order to index, visualize, and report your identity data, to deliver deep security intelligence and easy-of-use. These are standalone tools however IDHub allows you to integrate with either, or both platforms, depending on your analytics architecture and governance.
Elasticsearch: The Identity Data Engine, in Real-Time
IDHub enables you to integrate with Elasticsearch to index and analyse identity events from across the organisation, as they happen. From login events and access requests to permission changes and policy enforcement, there’s a wealth of insight available in Elasticsearch to search petabytes worth of data and recognize important security signals on the fly. Its search, analytics, and AI prowess means that no detail is missed, making it the high-fidelity data foundation for all security and compliance activities.
Metabase: The Intuitive Window to Insights
IDHub enables you to integrate with Metabase, that allows users to query the data warehouse in natural language, create beautiful interactive dashboard with a drag-and-drop tool, and easily sharing insights securely with stakeholders. This democratization of data analysis allows team members to create reports and explore data without having to learn SQL or come from a data science background.
Build Dashboards, Not Dependencies.
Metabase
IDHub can now integrate with Metabase - open-source Business Intelligence (BI) and analytics software. By connecting IDHub with Metabase, you can turn even non-technical users into pros at effortlessly building custom reports. Key features of Metabase for IDHub analytics include:
Dashboards
Interactive, Self-Service Dashboards
Enterprises are no longer constrained by static and canned reports. It enables application owners, and business managers to build, customize, and explore their own dashboards. Users can map data on the fly to discover the “why” behind any data – turning a stagnant asset that sits there on its hands – into an active research and decision-making tool.
Query Builder
The Visual Query Builder
When a query on user access comes up, the response is literally ready in seconds. The visual query builder enables users to choose data sources, apply filters and summarize data using an intuitive, point-and-click interface.
Reports & Automated Alerts
Scheduled Reports & Automated Alerts
All stakeholders are kept updated through the platform automatically. You can also schedule key reports ( e.g weekly access review) to be sent directly to stakeholders’ email In addition, you can set up alerts to be automatically notified when critical values pass certain limits.
See Everything. Miss Nothing
Elasticsearch
You can integrate Elasticsearch with IDHub, which provides insights and reporting capabilities related to user identities, access management, and overall system performance. Some possible use cases for integrating with Elasticsearch are:
Monitor
User Activity Monitoring
IDHub Elastic Search allows organizations to track and monitor user activity within the identity management system. It provides visibility into user login patterns, access requests, authentication attempts, and other user-related events. This helps in identifying abnormal or suspicious user behavior and detecting potential security threats.
Unauthorized Access
Access and Permission Analysis
IDHub Elastic Search can provide insights into user access rights and permissions across the organization's systems and applications. It enables administrators to analyze access patterns, identify access anomalies, and ensure compliance with security policies and regulations.
Risk assessment
User Behavior Analytics
Elastic Search based analytics in IDHub analyzes user behavior and access patterns to detect anomalies or deviations from normal behavior. It employs machine learning algorithms and behavioral analytics to identify unusual access patterns, potential insider threats, or compromised user accounts. This helps in proactively detecting and mitigating security risks.
Bottlenecks
Performance Monitoring System
IDHub Elastic Search provide insights into the performance and health of the identity management system. It tracks metrics such as system uptime, response times, resource utilization, and user activity trends. This information helps administrators optimize system performance, plan capacity, and address any bottlenecks or performance issues.
Provisioning Analytics
User Provisioning and Deprovisioning
IDHub also offer insights into user provisioning and deprovisioning processes. It helps administrators analyze the efficiency of user onboarding and offboarding, identify process bottlenecks, and optimize user lifecycle management workflows.
Auditing
Compliance Reporting
IDHub Elastic Search assists organizations in generating compliance reports related to user access, permissions, and system usage. It provides predefined or customizable reports that align with industry regulations and compliance frameworks. These reports help organizations demonstrate compliance and facilitate security audits.
Identity Data Insights with Metabase
Real-time Monitoring with Elasticsearch
Target Audience
Users of IDHub Analytics
IDHub supports integrations with external analytics platforms. Customers may forward IDHub data to a search/ingestion engine such as Elasticsearch for high-throughput indexing, and/or to a BI layer such as Metabase for self-service visualization. Either integration or both used in parallel enables technical analysts and business users to extract insight from identity and access datasets.
- Businesses and Enterprises: Businesses and enterprises likes to do big picture analysis of the structured and unstructured access log data when used in conjunction with Elasticsearch. These indexed or exported datasets can be exposed in a BI layer like Metabase to provide executive dashboards and reports for non-technical people..
- IT Operations and DevOps Teams: By integrating IDHub with Elasticsearch, IT and DevOps can index logs, drill down into infrastructure and system activity to identify issues or investigate incidents. When combined with metabase, teams are able to create real-time dashboards for monitoring system health and identifying outages..
- Security and Compliance Teams: Security team can export IDHub identities data to Elasticsearch, for log analysis, continuous threat monitoring and access surveillance. Additionally, BI tools such as Metabase allow teams to develop compliance reports and visual dashboards that auditors and executives can share.
- Developers and Application Architects: Developers use Elasticsearch through REST API to provide search based features with in their application. Metabase offers embedding APIs, and has published methods for exposing interactive dashboards and reports in customer applications.
Organizations that need high performance search/ingest as well as self-service vis commonly follow an integration strategy combining a search engine (Elasticsearch or similar) with a BI layer (Metabase and so on). IDHub can forward identity and access data to the platforms (or combination of both) according to customer need.
Data-Driven IAM Strategy
IDHub can forward event and attribute data to analytics platforms of choice by the customer. Elasticsearch is what customers typically use for real-time indexing and log analytics; Metabase is commonly used for business reporting, executives’ dashboards. IDHub connectors and recommended mapping help standardize quality of the datasets that are being made accessible to your analytics stack.
Get the most out of your IAM strategy by integrating IDHub to your analytics application.
Compliance Tools for Cyber Security
Cyber Security Tools

Access Control Policy Template for Organizations
Utilize our free Access Control Policy Template to help establish a healthy framework for your access control. Easy to customize and share with your team.

Application Onboarding Checklist
Learn about Application Onboarding essentials, and grab a copy of our free Google form, 36 question, application onboarding questionnaire to customize!
Cybersecurity Assessment Template
Discover why cybersecurity assessments are vital for regulated industries—plus a free template to strengthen security, manage risk, and stay compliant.