Describing Identity Management
Identity Access Management (IAM), also known as Identity Management (IDM), is a vital tool for managing user access within a network. It oversees the definition and administration of roles, access rights, and privileges for all network users, ensuring they have appropriate access to necessary resources for their daily tasks. It is a user access management tool. Learn key IAM phrases and terms in our IAM Glossary.
However, IAM encompasses more than just user access control. It extends to regulating access for each individual within an organization to various software applications and third-party resources or services utilized by the company. Furthermore, IDM governs the conditions under which users are granted or denied privileges to these assets through established access policies.
Should Erin have access to our WordPress site? Should she be a Standard User, an Editor, or should she have Administrative Access to WordPress, but nothing else?
Here is a quick explainer video, What is IAM?
IAM Example
Let's take a look at how an IAM Solution might look in a typical E-Commerce company with 20-100 employees.
In this example, we are only going to take a look at 6 sample employees, and we are assuming this company is only using about 6 applications. In all likelihood, they are using many more.
Each employee may or may not have access to each application, and if they do have access, they may have a different set of rights/permissions, or entitlements within that application.
Additionally, this company is utilizing four Roles which can be used to auto-assign users specific applications based on that job role, also known as Role-Based Access Control.
This kind of control and visibility, allows the IT team to limit the number of elevated accounts that could potentially be compromised, see who has what access to applications, and what level of access, at all times.
IAM Solution
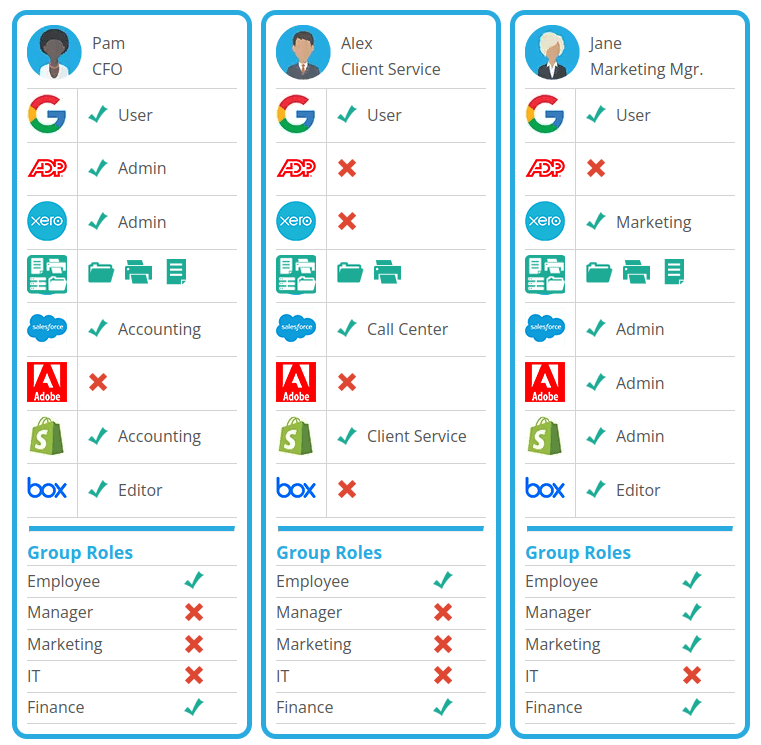
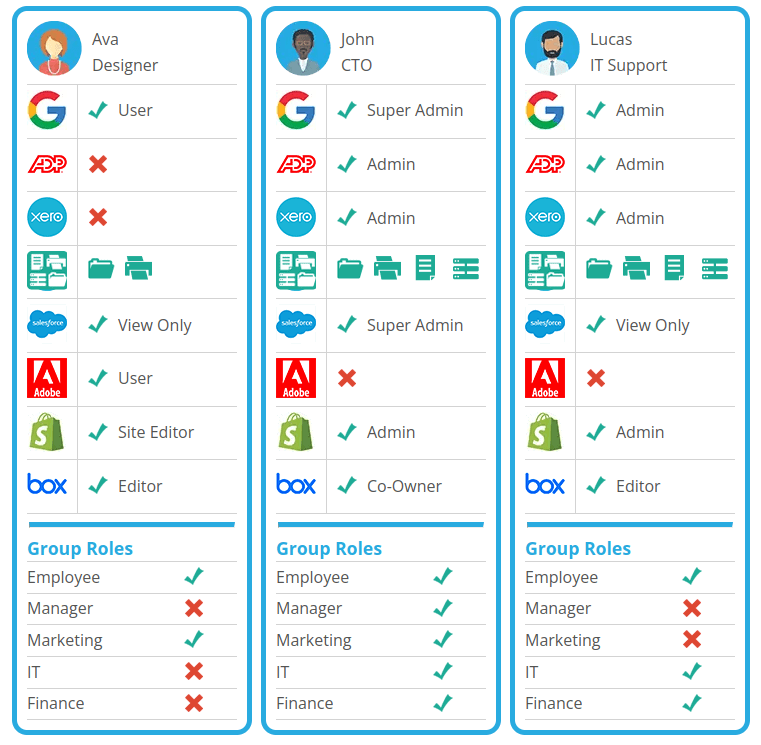
This process is somewhat easy to manage with a handful of applications, and a handful of Users.
However, according to the 2020 Blissfully Annual Report, small businesses today use over 100 different applications, with large companies using more than 200 on average!
To complicate things, each of these applications may have 2-20 different privileged role levels.
When you consider the number of applications businesses use today, multiplied by 20, 200, or 2000 employees, consultants, and partners, managing who has access to what becomes an overwhelming task.
As your team grows, so do your applications, risks, and requirements.
Everyone wants to grow smoothly, but in reality there are always added security risks, increased IT workload, and the lack of a holistic view of your organization.
The User Management Solution For More Industries
Traditionally Identity Management products have been a crucial part of large Enterprise IT environments. However, they were typically restricted to the largest businesses, that is, until now.
As cybersecurity concerns continue to escalate and technology becomes more affordable (as well as critical), IAM is becoming a vital part of every organization's security foundation regardless of size.
The overarching goal of Identity Management is to create an easy to use, centralized solution that grants secure access to systems across all corporate networks. That's an idea even a business with two people needs to have a solution for.
By creating traceable and auditable identities for every user, companies of any size can maintain compliance with outside regulators. Once that digital identity has been created, it must be maintained, modified, and monitored throughout the user lifecycle, this process can be laborious with only a few users, without centralized management.
What Are The Steps Of Identity Management?
The IAM process begins with onboarding a new user to your network and providing the appropriate access to company resources.
After onboarding, users can create access requests for additional resources. Access requests from users may be processed or declined.
These changes to a user's rights for applications and network resources will change throughout their lifetime in the network/company, also known as the user lifecycle.
Reviewing access throughout the user lifecycle is critical, and reporting can also be used in regulated industries to meet compliance.
Finally, when a user leaves the network, the offboarding of that user is needed in a timely fashion.
What Do Identity Management Products And Services Do?
IAM systems provide administrators the tools and technologies needed to change a user's role, track user activities, create reports on those activities, and enforce organizational policies on an ongoing basis.
IAM is designed to provide a way of administering user access across an entire organization.
Additionally, IAM is often used to ensure compliance with corporate policies and government regulations.
What Do Identity Management Systems Include?
Identity and management technologies include, but aren't limited to:
- Access Request Capabilities
- Automation
- Password-Management Tools
- Single Sign-On Tools
- Multi-Factor Authentication
- Provisioning Software
- Access Control Policy Enforcement Applications
- Reporting and Monitoring Applications
- Access Review Processes
- Workflow Builders for Approval Flows
- Identity Repositories.
Identity Management Systems are available in on-premises systems, as well as cloud-based systems.
Build Identity
Accounts
Manage Identity
Remediation
Attributes
Secure Identity
Rules Based Access
Security Transformation
Org Structure
Security Uplift
Change Management
