What Is Single Sign On (SSO)?
SSO, or "Single Sign-on," refers to a process of signing into a single account, which then validates your identity to other connected and trusted applications.
Users will log in to an Identity Management system(IDM) through the SSO and will not need to use any additional logins or passwords for any other applications or websites that have been added to the IDM.
The IDM will act as a User Authentication Service and will verify and store your authenticated identity and communicate this to other websites or applications that you would typically need to log into separately.
The IDM program takes on the responsibility of verifying who a User is. Any endpoints (sites or services) the User is trying to connect to will trust the IDM when it says the User is good.
When the User attempts to access an SSO-connected endpoint with an established trusted relationship, the SSO will essentially vouch for the User via an authorized token. In other words, guarantee the User is who they say they are.
The SSO tells the endpoint the User is Authenticated. The endpoint trusts that no additional information, credentials, or password is needed.
This solution not only eliminates the need to log in with a multitude of passwords, but it also eliminates the need for you to keep track of them, reset them, and most importantly lose them, or have them compromised.
How Does Single Sign-On (SSO) Work?
The SSO process consists of few parts. The User, The Single Sign-on Screen, the Identity Management System (IDM), an external service or website (endpoint), a validation token, and finally, the communication process between the IDM and the external service.
The process of SSO Authentication starts with a central Identity Management System, which houses a database of users and their credentials.
This centralized Identity Management System provides an interface for administrators to control all of their User's access and rights for all of their connected applications from one location or a "single pane of glass."
User Rights (entitlements) usually consist of roles like; Administrator, Editor, or User.
User Rights could also be proprietary roles with specific access provided by particular applications or Service Providers.
The IDM will have established partnerships or trust relationships with external applications and endpoints that would typically require login credentials.
When SSO validated Users attempt to access an external application, the application will agree to trust the IDM.
When a user logs into a Single Sign-On login page, they log in to the IDM system itself.
The IDM will handle the validation of your identity to confirm and relay who the User is.
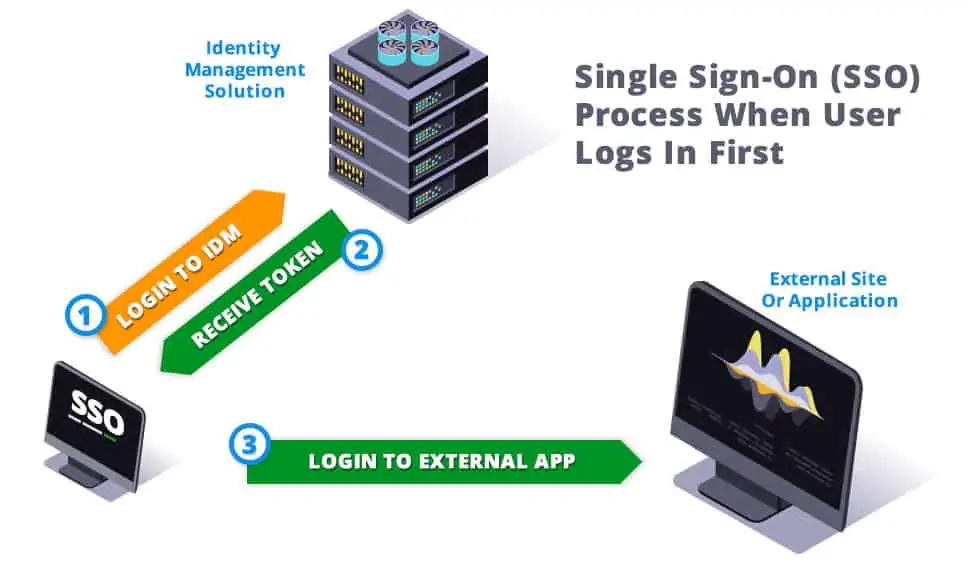
The IDM will store a validated token for the verified User for the current session.
Authentication tokens are digitally signed pieces of structured data that other applications can verify is authentic.
When the User tries to connect to a site or service, the service will connect to the IDM's SSO Authentication Process, verify that the token is valid, and provide the user access.
Additionally, the IDM will relay the appropriate Rights for that User account without any additional information needed.
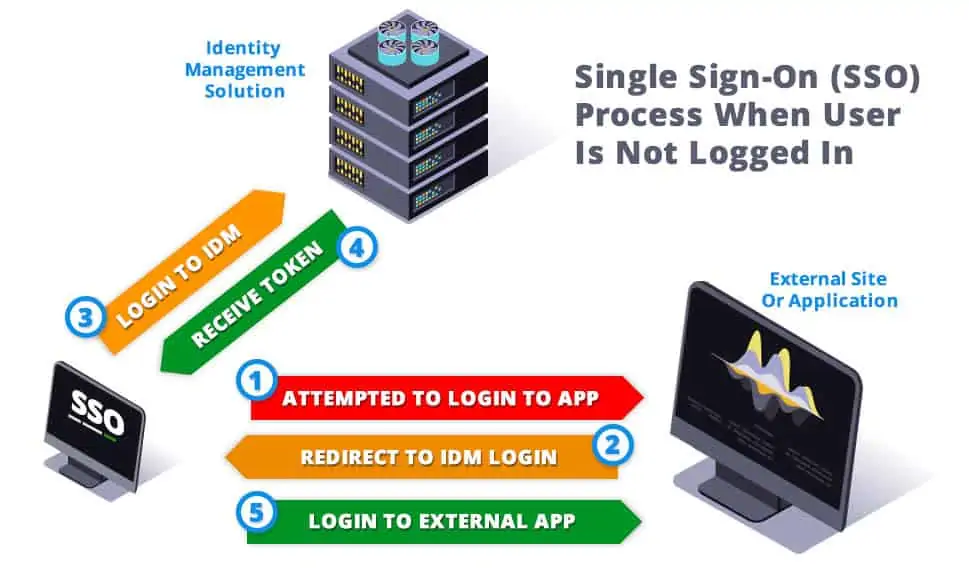
How Do Users Access Applications If They Are Not Logged Into The SSO?
If a User is not currently logged into their IDM system and attempts to log in to an application directly, the application will check the User's browser for validation.
This request will trigger the User to be re-directed to their SSO login page to access the IDM and get a token first.
What Are The Benefits Of SSO?
SSO inherently increases productivity and time management.
Time is money, and the time savings includes both the time it takes to log in and the time required to search for, find or recover passwords.
A study by beckershospitalreview.com examined implementing an SSO service across 19 hospitals and nearly 13,000 users.
The results were overwhelming, with the average weekly time savings from SSO totaling 943.4 hours.
The additional benefit is the extra time your IT staff will have to focus on other issues.
According to Gartner, somewhere between 20%-50% of Support desk calls are due to Password resets and account unlocks.
Removing the need for your IT department to spend up to half their time managing passwords can result in significant increased productivity, allowing them to focus on other issues.
What Is The Security Benefit To Using SSO?
Password phishing is the single largest cause of data breaches and cybersecurity attacks, and it's not even close.
Managing a multitude of passwords has long been the lowest hanging fruit for hackers to attack.
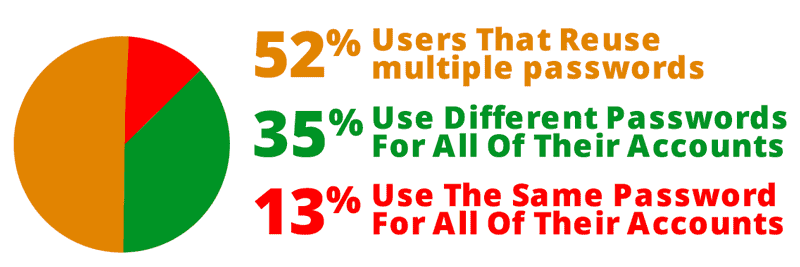
Despite the best efforts of security teams to train users about the importance of secure passwords, according to a Google 2019 report, 65% of users still re-use their passwords across a multitude of accounts.
Similarly, studies have shown that over 50% of corporate passwords are currently using weak passwords, typically due to the need to remember multiple passwords.
The 2021 Data Breach Investigations Report by Verizon reported that "85% of breaches involved the human element."
Hackers frequently target unimportant websites without any valuable information due to their low security.
When unsecured websites are hacked, the passwords they harvest are shared globally inside of a public password Database.
Hackers are well aware that up to 65% of people re-use their passwords on other websites.
Once a compromised username and password are exposed globally, they are used to attempt logins on thousands of other highly protected sites and networks.
When exposed password lists from simple blogs or fan sites contain 1000's of usernames and passwords, there is an arguably 100% certainty that hackers will discover re-used credentials on valuable networks or services.
Malicious actors frequently use this method to gain access to highly restricted information or even administrative access.
Managing a Single password with SSO allows you to have one highly secure password.
Since users only have to use one password, SSO makes it easier for them to create a complex password, providing better protection.
Do I Need SSO If I Use A Password Manager?
Password Managers are a massive step in the right direction and allow you to create strong passwords that are not easy to hack or gain access to through a brute force attack.
Password managers such as Keeper and Dashlane are a much better option than keeping spreadsheets of passwords, or worse yet, re-using passwords across multiple sites or services.
Password managers have a severe downfall though.
As we've seen above, hackers do not bother trying to crack passwords.
There is no reason to try and defeat a highly sophisticated and encrypted password manager when the weakest link in the security chain is still the human User.
Passwords like %HDPd72bq!nle@w3$9v$ lose all their security value when they are copied and pasted into a fake website via a phishing attack.
As we've seen above, the most effective method of acquiring stolen passwords is phishing emails which have an alarming efficacy today.
According to reports from springeropen Even after providing phishing training to employees, the effectiveness of phishing attacks on employees is somewhere in the 10%-20% range, down from 25%-30% with no training.
However, even if you managed to get your effectiveness at spotting and preventing phishing attempts to 5%, an employer with 20 employees is likely to have at least one employee provide privileged access to a malicious hacker.
The safest way to prevent credentials from being stolen is to eliminate them as much as possible.
If a user does not have a password to steal, they can't divulge it by mistake.
Do I Need MFA With A Single Sign-On Login?
Multi-Factor Authentication (MFA) is an excellent addition to SSO sign-on. Having a single SSO is much better than multiple passwords, however, it is still a potential point of a data breach. If an individual could gain access to your SSO password, they would be able to get access to all of your accounts. Adding a Multi-Factor tool such as Google Authenticator or LastPass Authenticator is a great way to add another layer of protection against the only access point left through your employees.
Examples Of Single Sign-On That You Use Every Day.
This article's focus is primarily on how your organization can utilize SSO internally to improve your cybersecurity, so most of the instances of SSO are not public, they are within an organization.
However, you don't have to look far for semi-public examples of SSO that you likely use every day.
Google's Workspace services utilize Single Sign-On to give you access to their entire suite of tools.
If you use Gmail, Google Docs, Calendar, Chat, Keep, or any other services, you can access any of these additional services after logging in to your Google Account without logging back in.
Another example is Microsoft. If you happen to have a OneDrive account, you may have noticed you can open the Microsoft store or remote office apps without needing to log in again.
Can I Use SSO For All My Applications?
Sites or applications will typically need to be compatible with Security Assertion Mark-up Language (SAML) or OpenID Connect (OIDC) to be part of your SSO and IDM landscape.
The best way to manage Generic websites and applications that do not have SAML or OIDC connections would be to utilize a secure password manager.
Don't forget to use Multi-Factor Authentication to access your password manager as well.
Can I Use A Bio-metric Login With SSO?
The short answer, absolutely yes.
Much like adding in SSO, creating your initial login to be used in part or wholly by a bio-metric system will eliminate your last password.
If you use it in conjunction with a password, it will strengthen it significantly by providing a verification method that is not easily lost, stolen, or duplicated.
What is a Bio-metric login?
If you have a phone that uses your fingerprint, retinas, or facial ID to open applications, congratulations, you are currently using bio-metric logins.
Did you know other bio-metric verification methods include signature recognition, hand geometry, Ear shape, walking movement, or even deoxyribonucleic acid (DNA) to verify against your genetic material!
How Do I Start Using SSO?
Several Identity Providers are available to manage your company's user identities and implement Single Sign-On technology.
However, It has traditionally been a costly investment, usually reserved for businesses with tens of thousands of employees.
Sath has built IDHub from the ground up. As a result, IDHub provides a comprehensive SSO solution and IDM features not available in other solutions.
IDHub removes the need to have a dedicated IT team to manage your IDM.
Instead, we've created an easy-to-use interface designed to be accessed and managed by Administrators, Managers, and Regular Users.
We designed our software to go beyond the current market offerings while significantly reducing the cost of maintenance.
We incorporated the management of IDHub into a front-end GUI to allow everyday users to do all traditional tasks and create advanced workflows, complex rules, and functionality not available on more expensive products.
Start securing your critical assets today. Schedule a Chat with one of our advisors to quickly get your system up and running and drastically reduce your risk of being compromised by malicious threats.
Common SSO Protocols: SAML, OAuth, and OpenID Connect
SSO implementations rely on standardized protocols to securely authenticate users across multiple applications. The most prevalent protocols include:
SAML (Security Assertion Markup Language):
Widely used in enterprise environments, SAML facilitates the exchange of authentication and authorization data between identity providers and service providers.
OAuth 2.0
Commonly employed for granting third-party applications limited access to user resources without exposing credentials. It's prevalent in mobile and web applications.
OpenID Connect
An identity layer built on top of OAuth 2.0, OpenID Connect allows clients to verify user identities and obtain basic profile information.
Understanding these protocols is crucial for selecting the appropriate SSO solution that aligns with your organization's security requirements and technical infrastructure.
Best Practices for Implementing SSO Securely
While SSO enhances convenience and security, improper implementation can introduce vulnerabilities. To ensure a robust SSO deployment:
Enforce Multi-Factor Authentication (MFA)
Adding an extra layer of verification significantly reduces the risk of unauthorized access.
Adopt the Principle of Least Privilege
Ensure users have access only to the resources necessary for their roles, minimizing potential damage from compromised accounts by adopting the Principle of Least Privilege.
Regularly Audit and Monitor Access Logs
Continuous monitoring helps detect suspicious activities and respond promptly to potential threats.
Implement Session Timeouts
Automatically logging users out after periods of inactivity mitigates the risk of unauthorized access from unattended devices.
Adhering to these best practices fortifies your SSO implementation, balancing user convenience with stringent security measures.
Final Thoughts On Single Sign-On
With new data breaches and Ransomware threats increasing daily, it's essential to act now.
If you're currently allowing your Users to use multiple passwords or allowing your Users to manage their passwords, your company is a prime target.
If your organization hasn't experienced a catastrophic attack yet, consider yourself lucky, but don't wait until the attack happens to develop your prevention strategy. Contact IDHub today.