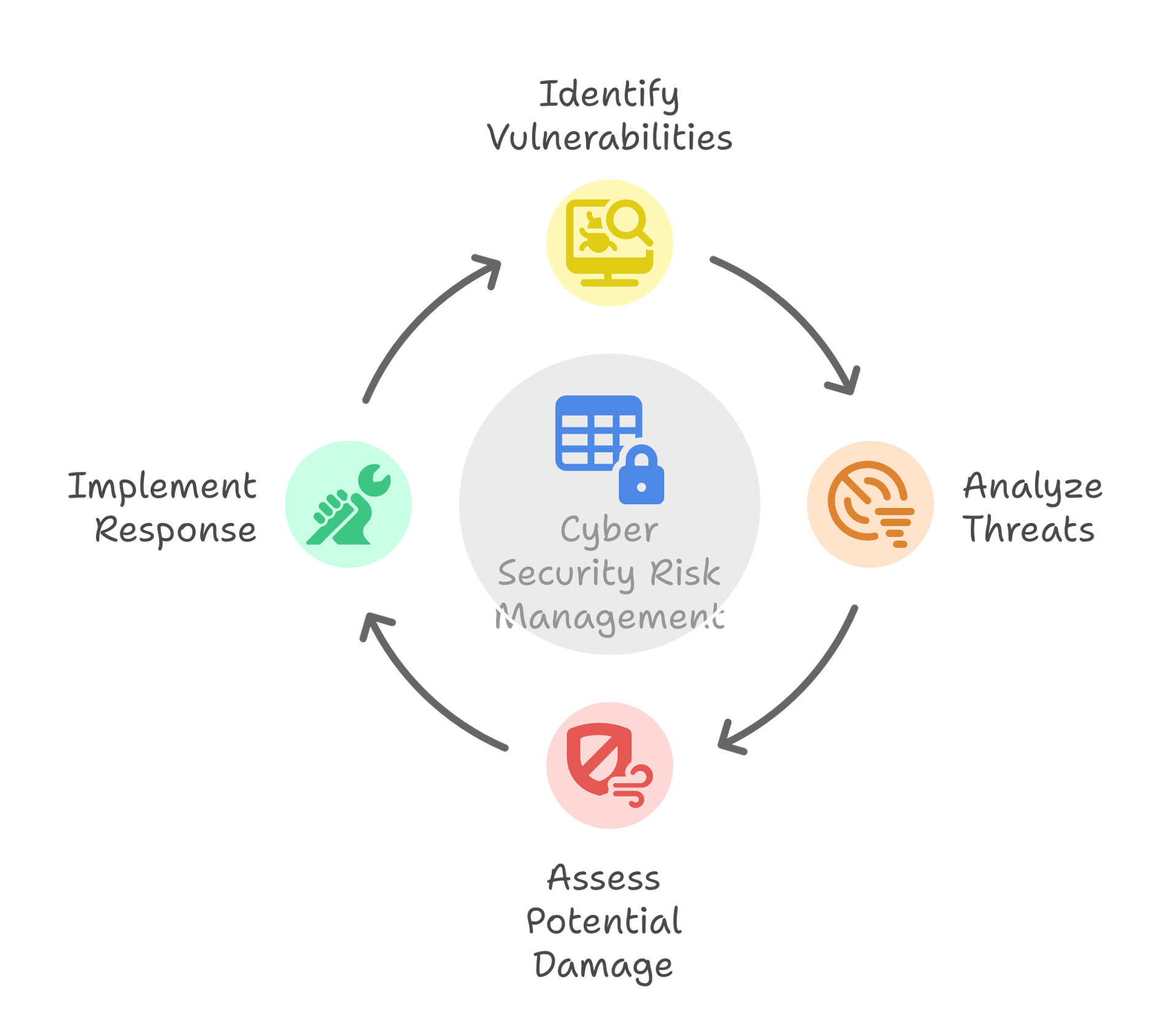
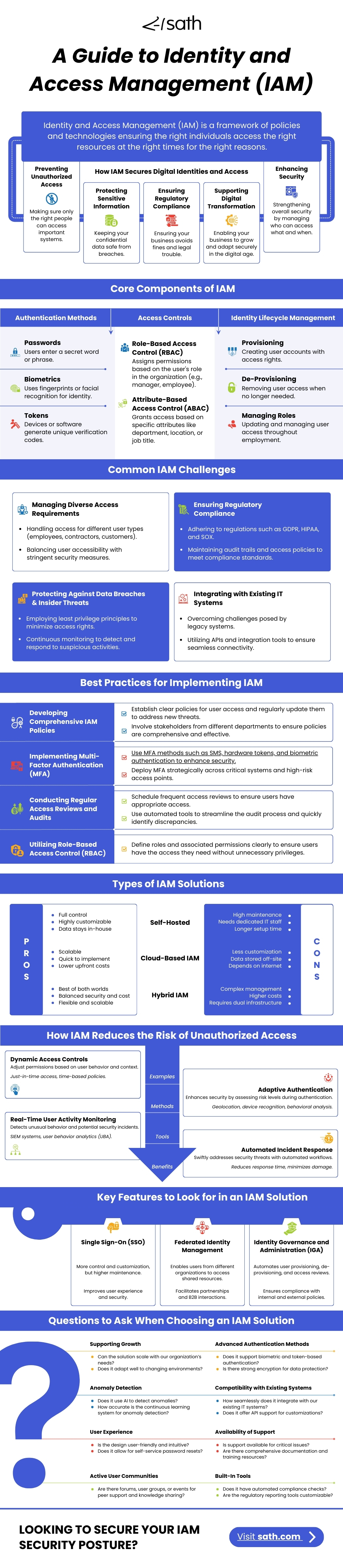
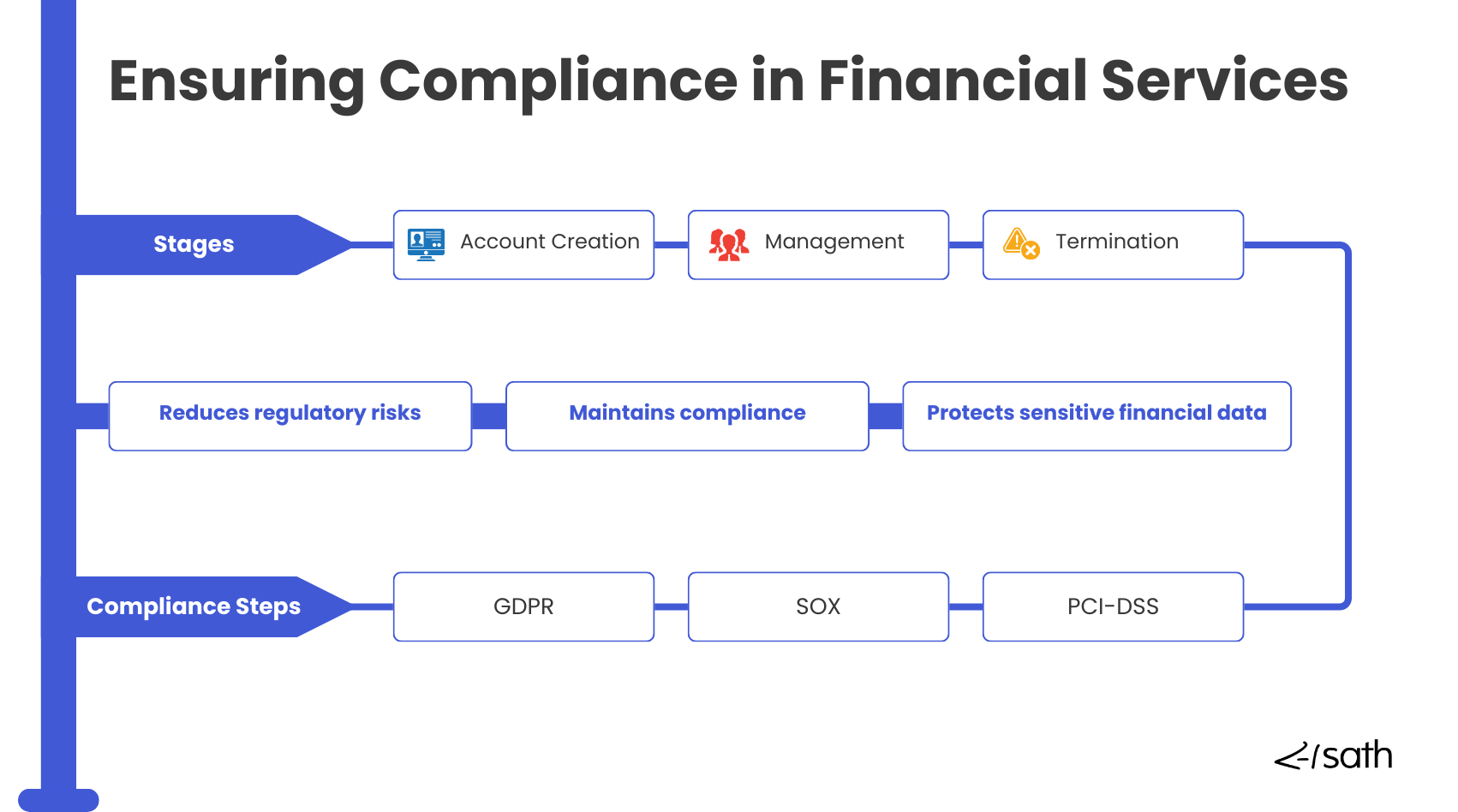
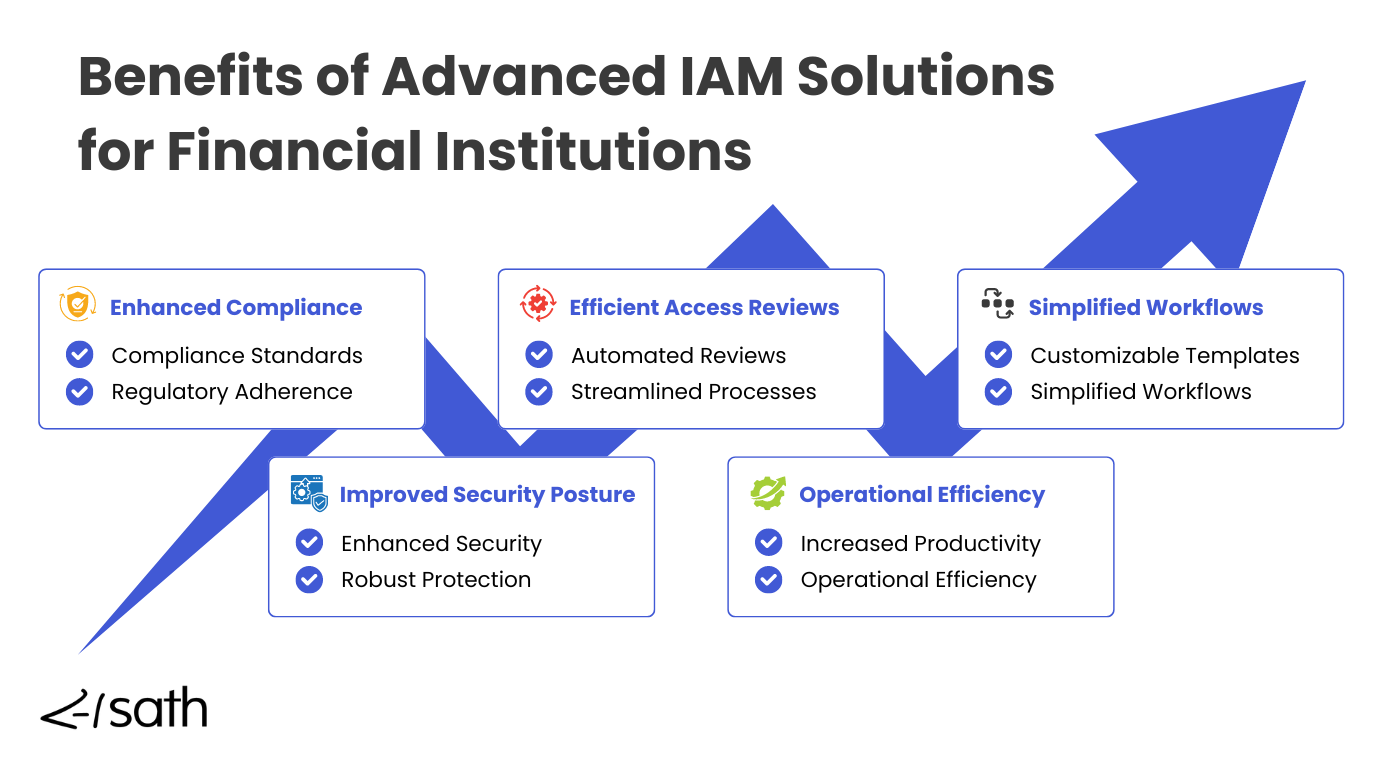
Industry
Check out these blog posts that are related to Sath Inc news, as well as news about IDHub, and Identity and Access Management solution.
“As you have large breaches, consumers say, why would I entrust this organization with my sensitive, confidential information. If you lose less than 1% of the total customers as a result of your data breach, that could translate into tens of millions of dollars of loss.” ~ Dr. Larry Ponemon, Founder and Chairman of the Ponemon Institute.