Setup User Logins
Creating users via Service Request will provide default passwords for users to use and login to IDHub. However, password management is an important feature in any Identity management application and is very specific to every organization. 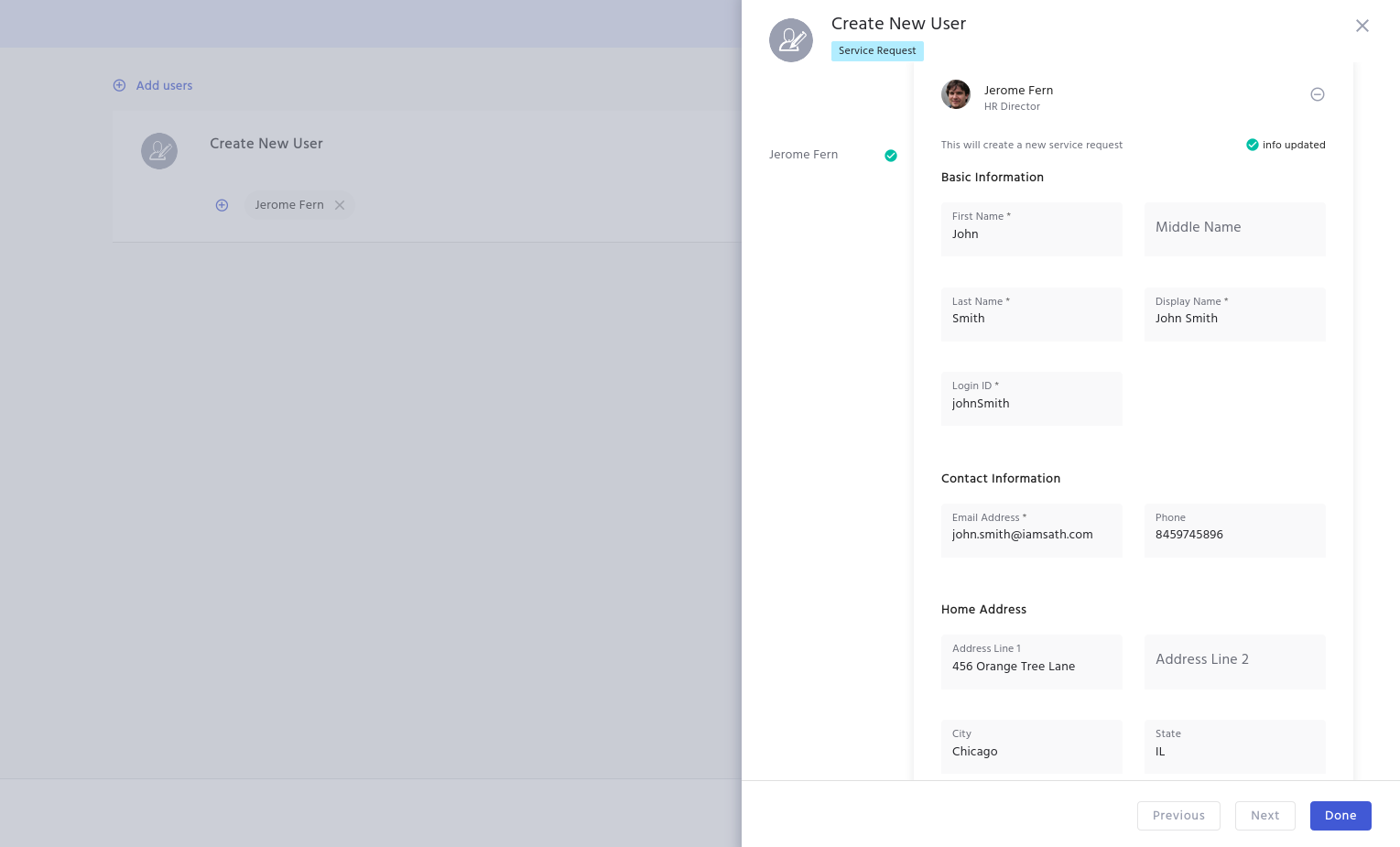
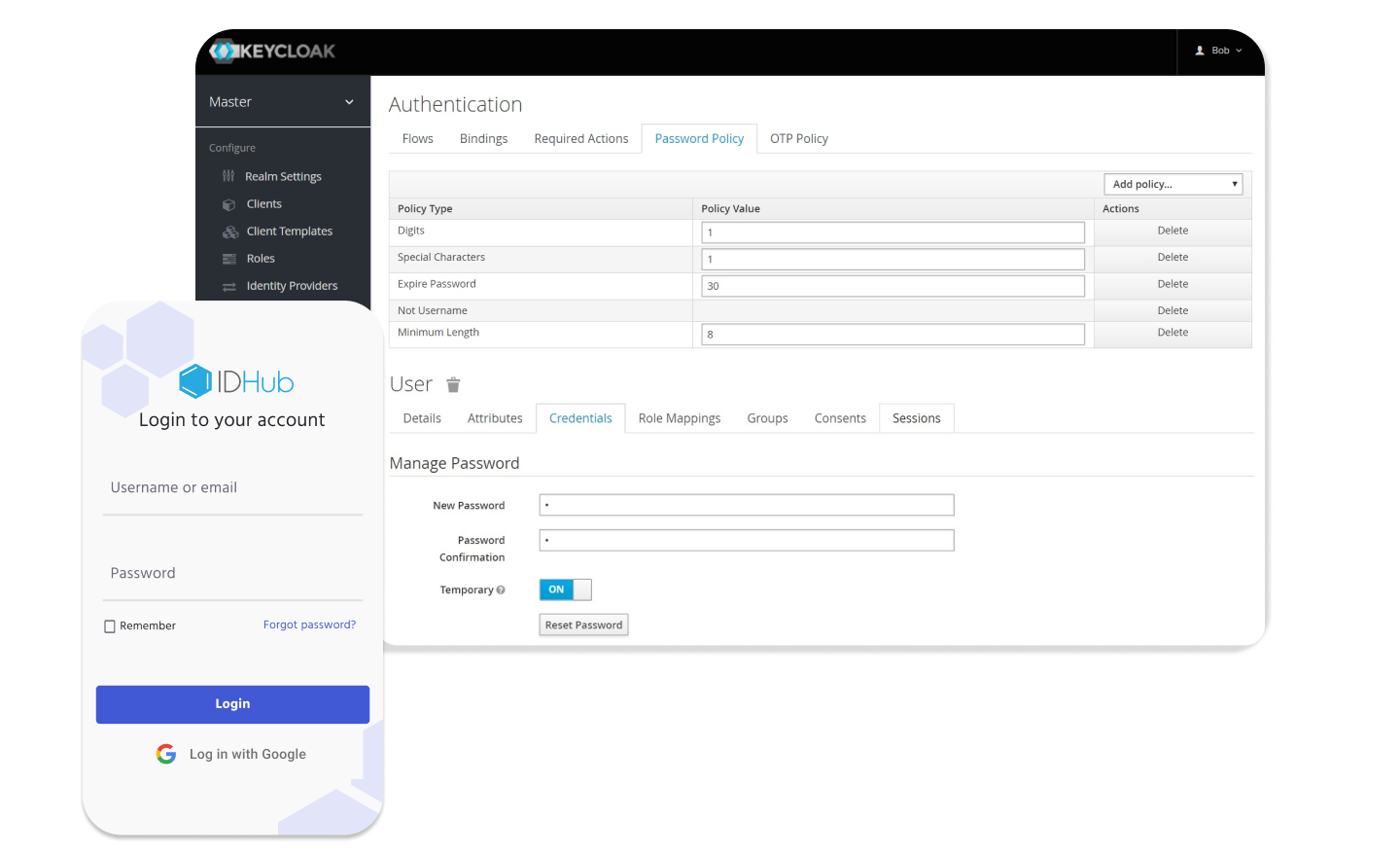
Keycloak Password Manager
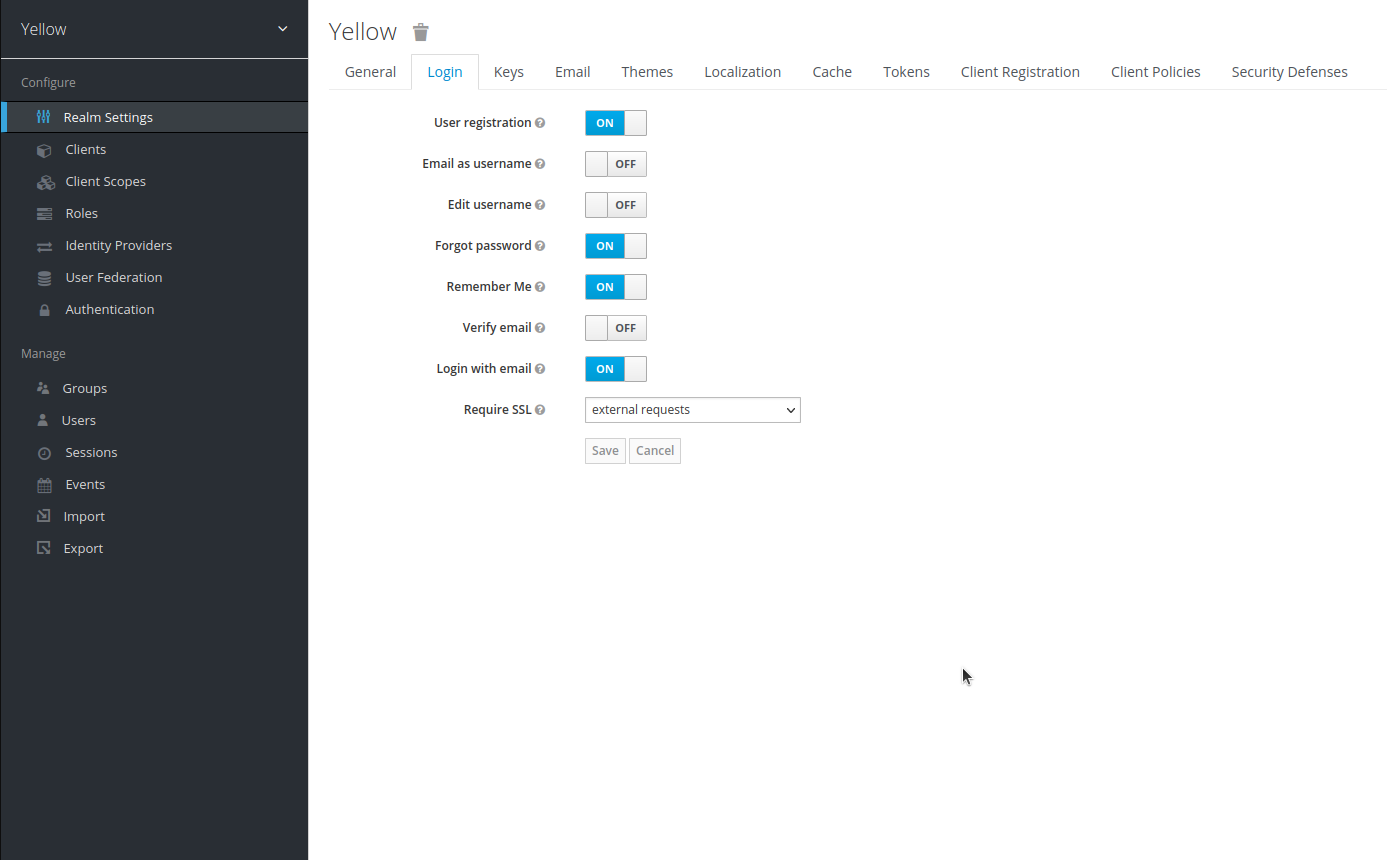
IDHub uses Keycloak to manage its password and SSO capabilities. Listed below are the different ways passwords can be managed.
- Use default passwords, set by Keycloak, when creating a new user via IDHub Service Requests
- Enter a password for each user in Keycloak manually
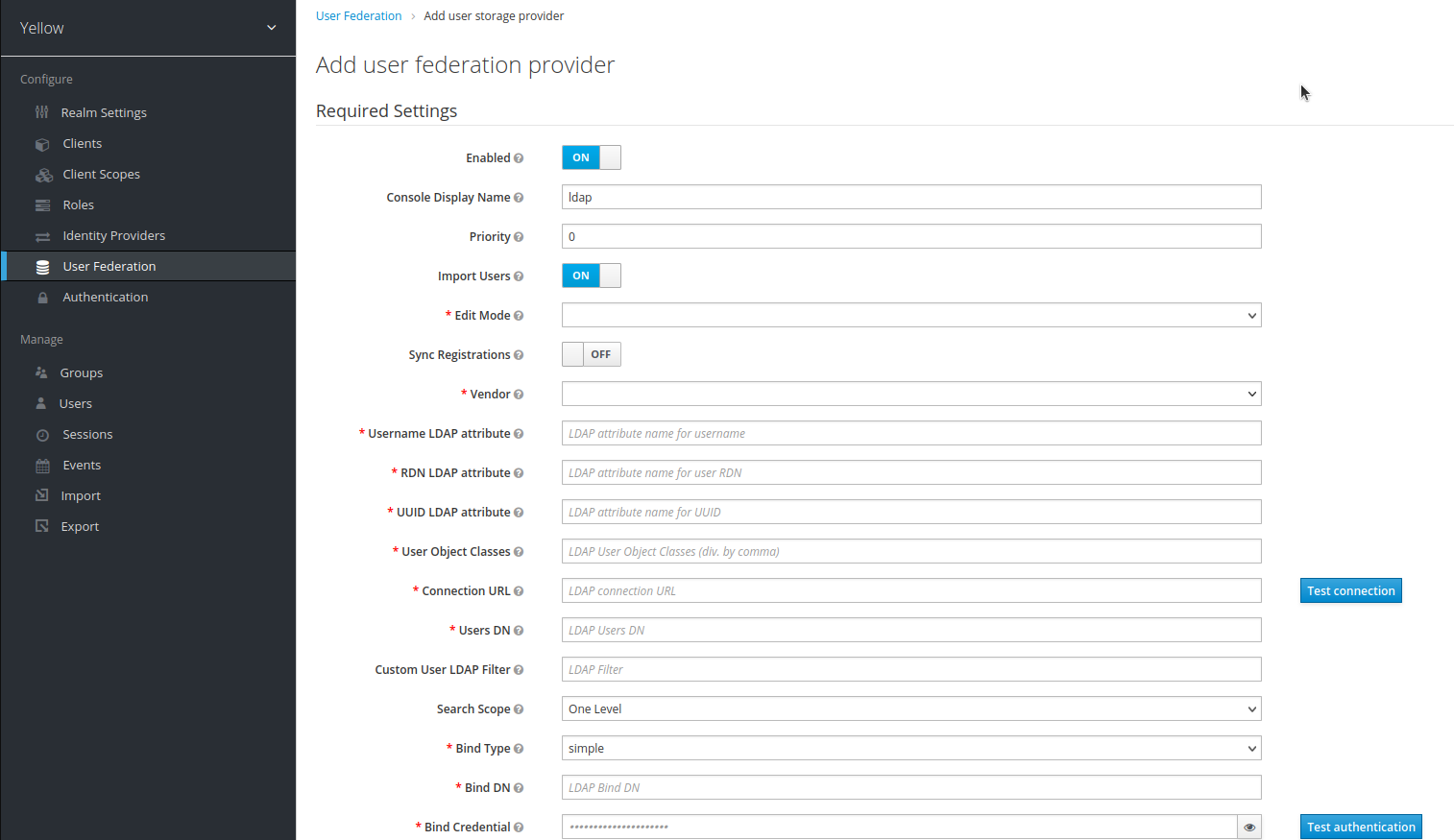
User Federation
User Federation is a process by which user information is pulled from a target application into IDHub Keycloak, and uses passwords that are present in the application the users are federated from. From the Keycloak Administration tool of IDHub you have the ability to configure user federation.
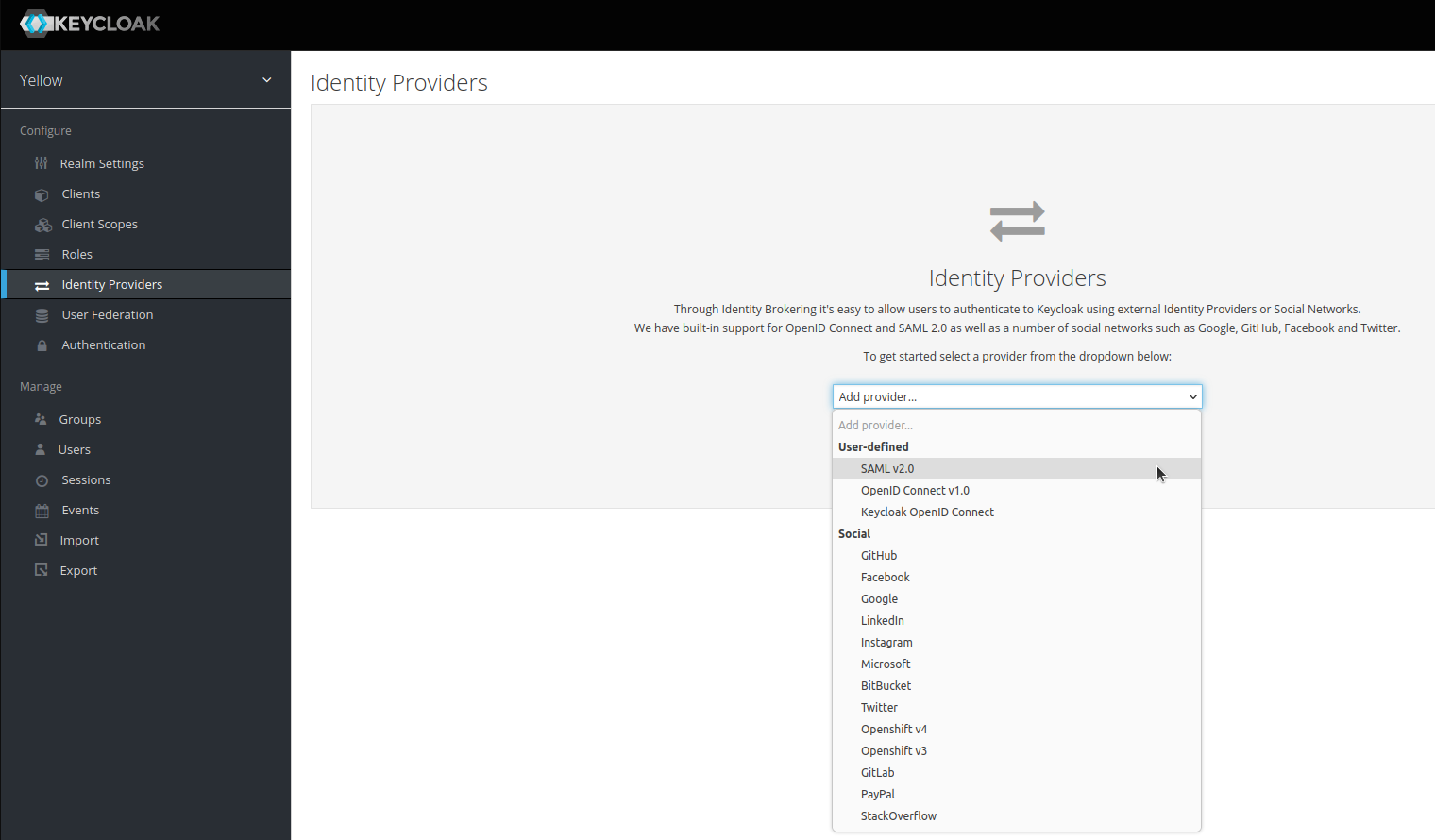
SSO/SAML
SSO/SAML setup is a process by which passwords are avoided completely, and users are allowed to login with an authentication system of another application, to keep a centralized login to all their applications. IDHub inbuilt Keycloak provides administrators an easy way to manage and setup SSO for user logins.
Centralized Login
You can configure the SSO/SAML capabilities using Keycloak, so users are allowed to login with an authentication system of another application, enabling a centralized login to all their applications.
Password Management Benefits
- Default login passwords via IDHub Service Requests
- IDHub includes Keycloak
- User Federation capabilities
- SSO/SML capabilities
Video Tutorial
Microsoft Entra ID (Formerly Microsoft Azure AD) SSO Integration
Compliance Tools for Cyber Security
Cyber Security Tools

Application Onboarding Checklist
Learn about Application Onboarding essentials, and grab a copy of our free Google form, 36 question, application onboarding questionnaire to customize!

Access Control Policy Template for Organizations
Utilize our free Access Control Policy Template to help establish a healthy framework for your access control. Easy to customize and share with your team.
Cybersecurity Assessment Template
Discover why cybersecurity assessments are vital for regulated industries—plus a free template to strengthen security, manage risk, and stay compliant.