Access Review
IAM (Identity and Access Management) user access reviews are an important part of ensuring that your organization’s security measures are up to date and effective.
These reviews help identify any potential security vulnerabilities or areas of non-compliance, enabling you to make necessary changes before they become a risk.
By identifying any potential issues and vulnerabilities in your system, you can take the necessary steps to address them and ensure that your organization remains secure.
Access Certification
IDHub user access reviews are called Access Certifications, and can be created and managed by IDHub System Administrators, who can define the parameters for each Certification.
System admins can perform the following actions while using the Certification tool:
- Create new access certifications
- Modify existing certifications
- Run IAM certifications in real-time
- Schedule certifications to run on a later date and time
- Create certification campaigns that run continuously on a scheduler
- Archive certifications that are no longer in use
- Assign user access certification tasks to appropriate users, job titles, or managers
User Access Reviews vs Resource Access Reviews
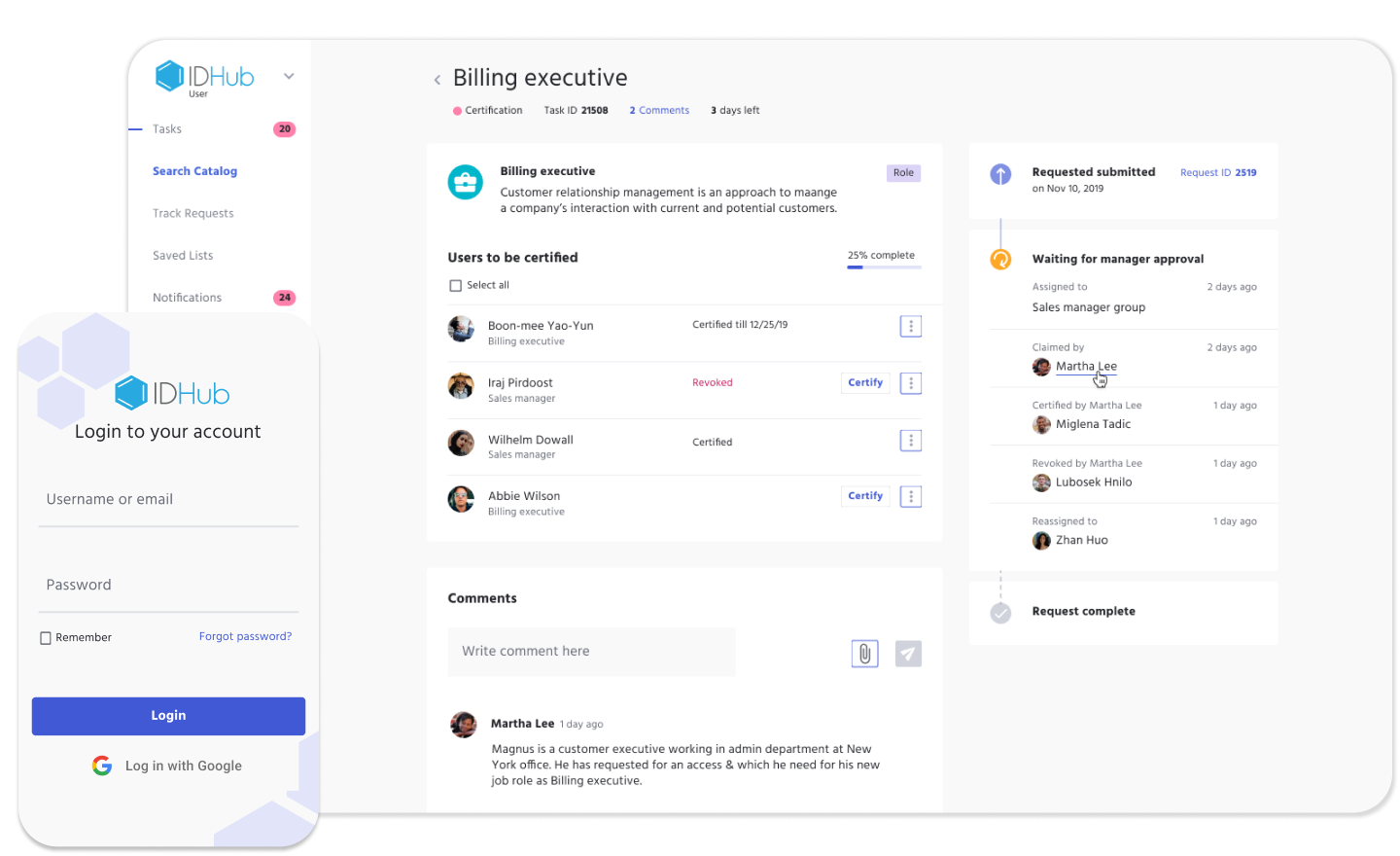
IDHub user access certifications can be created to audit a user, or a group of users, as well as a resource, or a group of resources.
In the images below, you can see the two types of Certification Tasks
- Certifying all user access to the resource Xero
- Certifying the user Steve Clark's access
IAM Certification Custom Queries
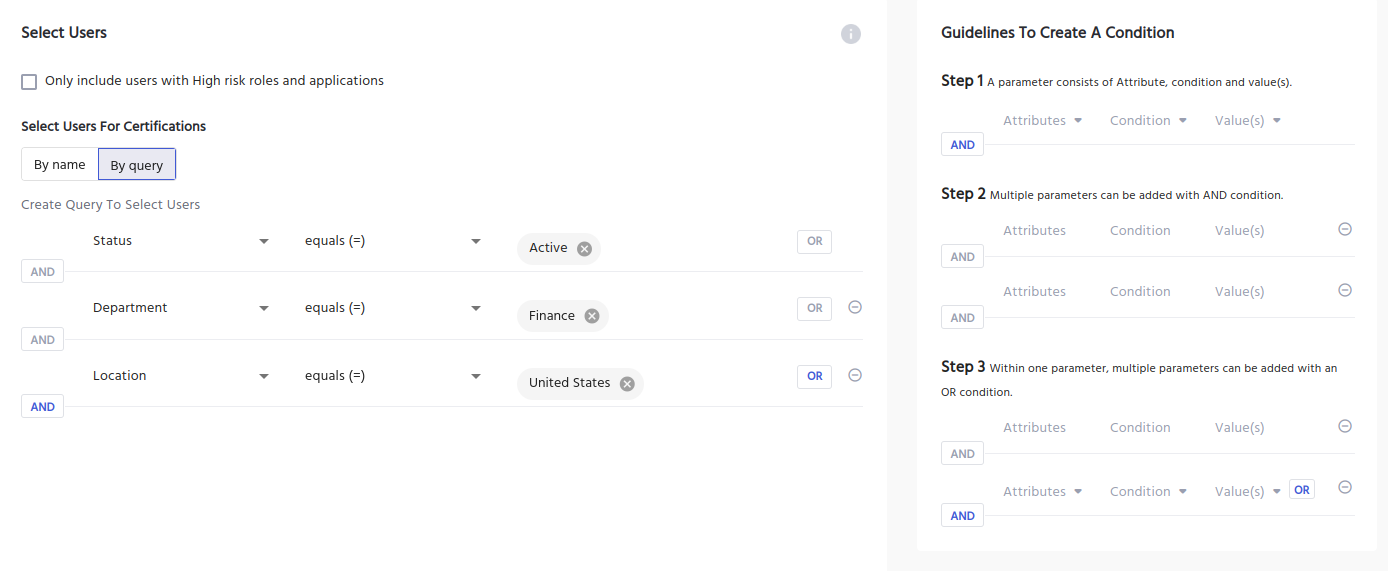
IDHub makes it easy to fine-tune specific data sets when configuring Certifications.
The advanced filtering allows admins to choose what and who to certify, by targeting user attributes or custom queries.
Admins can quickly set-up granular data sets to audit specific users of an application or permission.
Automate User Access Reviews
IDHub Access Certifications can be configured to auto trigger an audit, based on certain predetermined events.
Out of the box Certification triggers include:
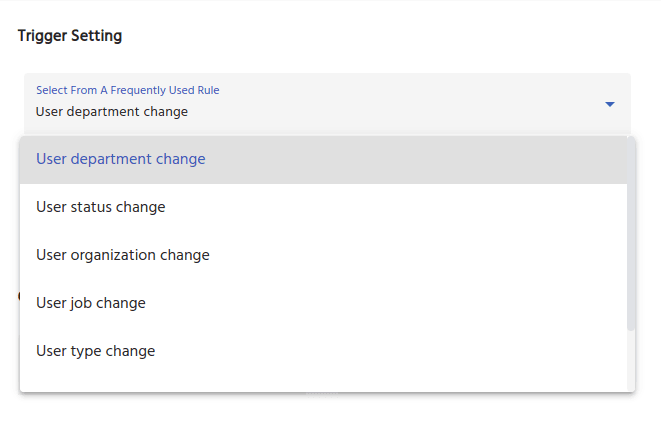
- User department changes
- User status changes (active to disabled or LOA)
- User job title change
- User location change
Like most features of IDHub, identity access management certification triggers can be configured to do exactly what you need, as they are based off IDHub Workflows and Automations.
IDHub allows for custom no-code workflows, using all events, triggers, attributes, and processes, as parameters for your access review needs.
Access Review Process
Below we explain the Access Review Process in IDHub.
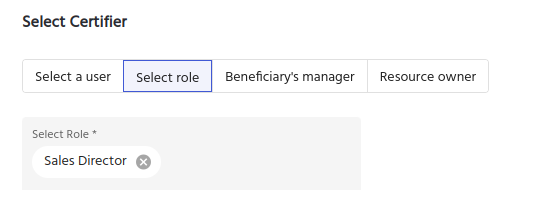
When a new Access Certification is created by an admin, a certifier is selected during configuration. The certifier is the user that will receive the task to review access.
IDHub is flexible, allowing admins to choose exactly who they want to perform the access review.
- A Named User
- A Role or Job Title
- The Beneficiary's Manager
- The Resource Owner
Access Review Tasks
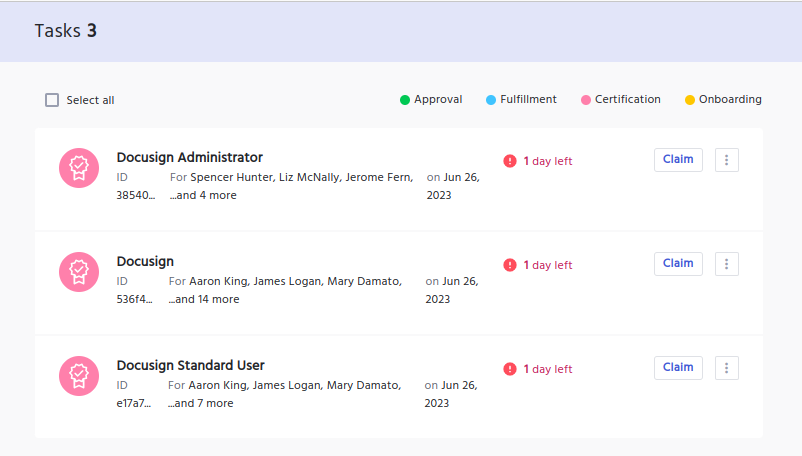
Each access review task will indicate exactly what the certifier needs to review.
In this example, we can see the certifier received 3 tasks:
- Certify Access to Docusign
- Certify Access to Docusign Admins
- Certify Access to Docusign Standard Users
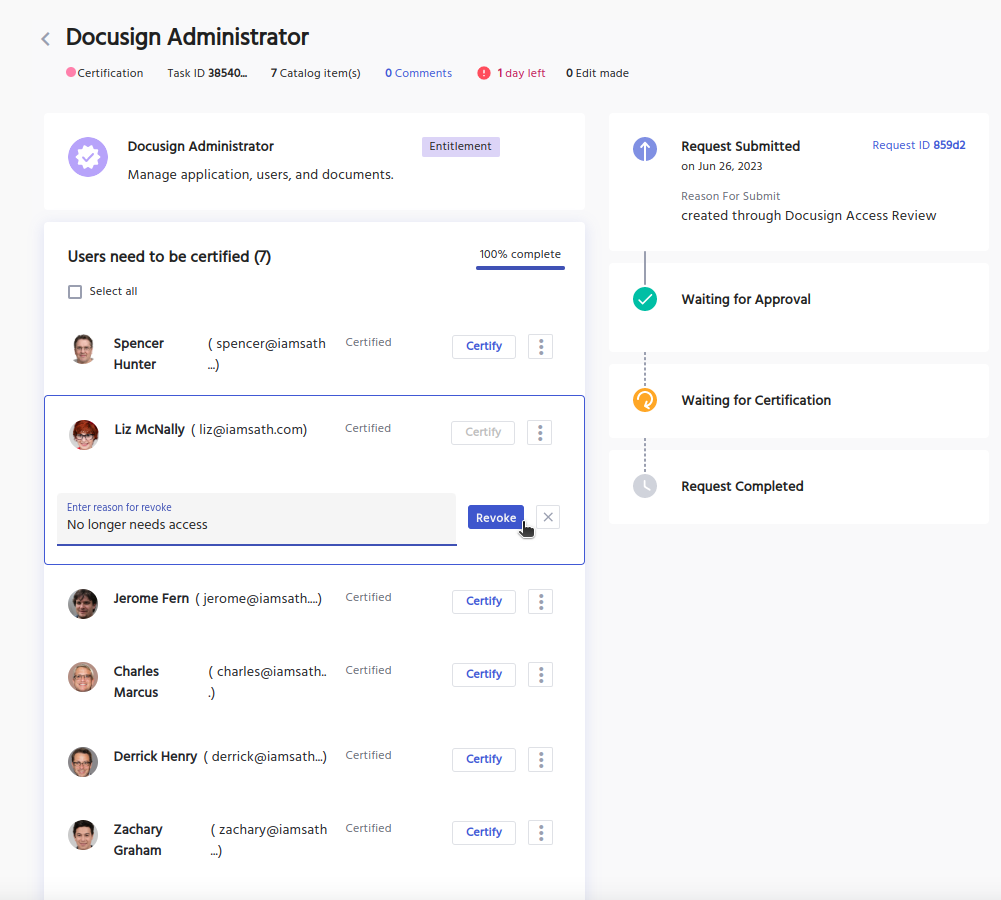
Certify and Revoke Access
Within the task, certifiers can perform the following actions:
- Certify Access
- Revoke Access
- Escalate the task if they are unsure on how to proceed
In this example, the certifier will revoke Liz's access to Docusign Admin permissions, or we call entitlements.
IAM Access Reviews
User Access Review Video
Learn how to create a new Access Review in IDHub, as well as certify and revoke access directly from the certifier tasks.
Compliance Audit
Compliance audits and requirements can be stringent, and maintaining the precise schedule for them can be tricky.
Some security policies require access reviews to be completed on an annual, quarterly, monthly, or even weekly basis.
IDHub access certifications can be configured to automatically initiate on a predetermined schedule. If the schedule changes, admins can easily modify the certification scheduler with a few simple clicks.
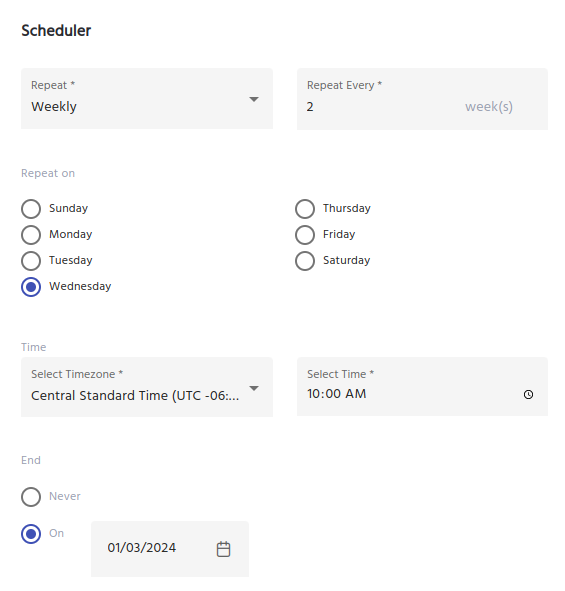
Easily Meet Regulatory Compliance
Access Reviews and Reporting Video
Check out the video below to see IDHub in action and learn how Access Reviews and Reporting collaborate to ensure users have only the access required for their specific roles. Seamlessly deliver the essential reports auditors need for regulatory compliance, all right at your fingertips.
Approval Workflow
Access certification approval workflows determine what happens before and after the certifier completes the task.
IAM approval workflows can accommodate any process needed for access reviews. For instance, sending notifications to the appropriate users, generating additional tasks to specific users, or any flow, at any time in the review process.
A few examples:
- Before any tasks to review access are sent to certifiers, a safe-guard task is initiated and sent to the user in charge of deciding if the audit can take place.
- If the user has been certified, they keep their access and nothing changes.
- If a revocation is initiated, IDHub immediately deprovisions access to that resource, for that user.
- A notification is sent to managers, informing them that access was certified or revoked to a user on their team.
Any flow needed for your organization can be accommodated with IDHub Workflows.
Take a peek at IDHub, Tour it yourself with no obligations.
Compliance Tools for Cyber Security
Cyber Security Tools

Access Control Policy Template for Organizations
Utilize our free Access Control Policy Template to help establish a healthy framework for your access control. Easy to customize and share with your team.
Cybersecurity Assessment Template
Discover why cybersecurity assessments are vital for regulated industries—plus a free template to strengthen security, manage risk, and stay compliant.

Application Onboarding Checklist
Learn about Application Onboarding essentials, and grab a copy of our free Google form, 36 question, application onboarding questionnaire to customize!