IAM Automation
Identity and access management (IAM) automation refers to the use of automated processes, tools, and technologies to manage and control user identities within an organization's IT environment.
The goal of identity automation is to streamline and simplify IAM tasks, making it more efficient, secure, and scalable.
By leveraging identity automation, organizations can reduce the risk of human errors, enhance security, and achieve greater operational efficiency in managing user identities and access.
IAM workflow automation can cover a variety of tasks, including:
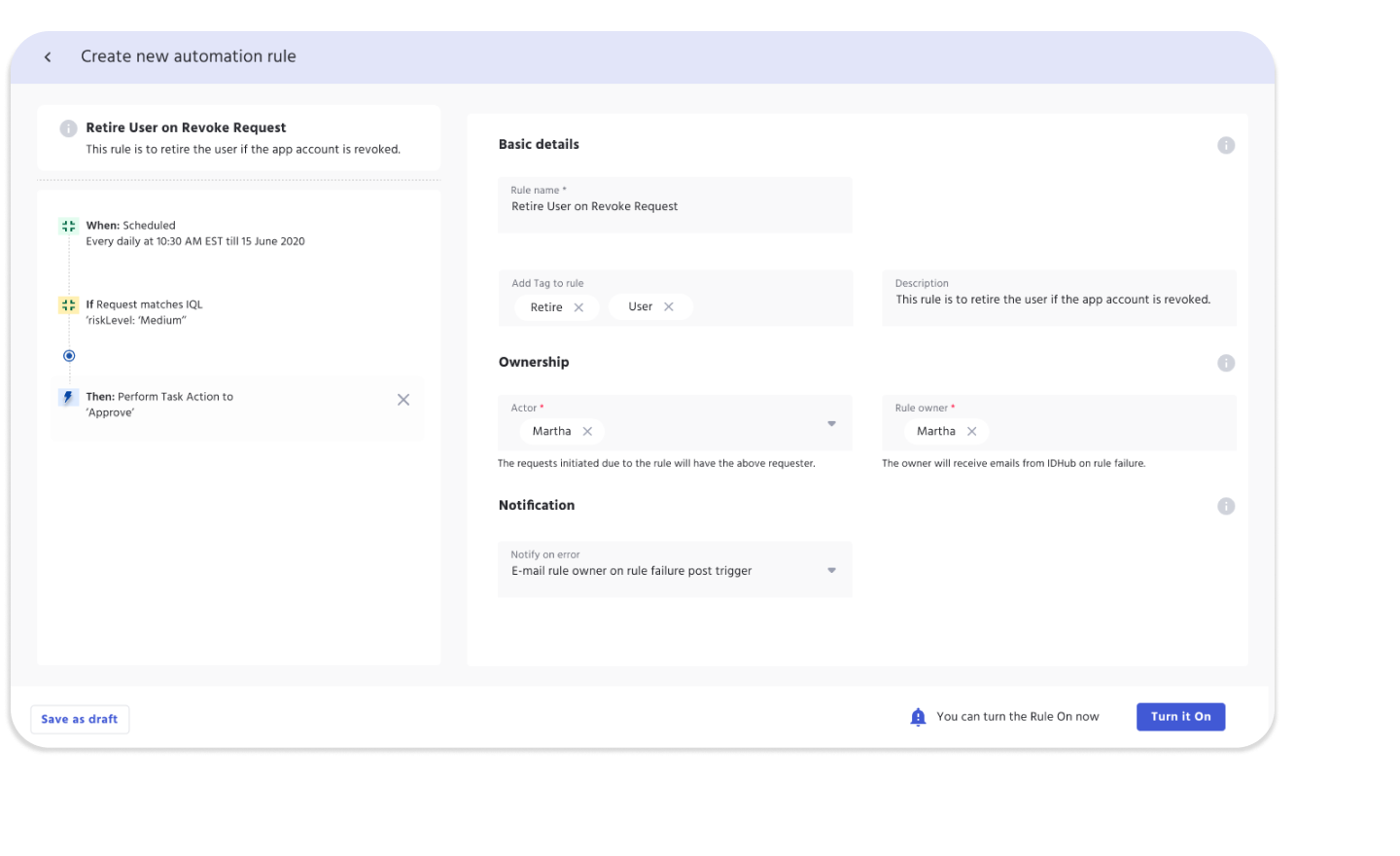
Workflow Automation
Triggers
Triggers are events that occur in IDHub. First Step is to pick an event within your Identity Security that you wish to automate. Some of the possible events may include:
- Field Value Changed
- Create Request
- Create Task
- Modify Request
- Delete Request
- Expire Task
- Task Action Performed
- Comments on Request
- Incoming Webhook
Apart from event based, a trigger can be on a schedule as well.
Condition
Conditions are based on IDHub Query Language. You can have any condition added and it will be an additional check on top of existing trigger to start an action.
IDHub uses GraphQL to search across IDHub and cross-collections to get desired results.
A condition can be anything from Location based search to User Account or User based attribute logics. You can also have conditions based on provisioned date range to pick a targeted time period in which events will be tracked and on an event, actions will be performed
Some examples of conditions are:
“location=Illinois AND department=IT” - This will only perform actions on event for IT Department folks in Illinois in your organisation
Action
Final Step of Automation is to perform some functions that you desire in IDHub. We can do diverse actions like:
- Assign Task
- Withdraw Task
- Comment on Request
- Send Email
- Send Web Request
- Create ticket in Jira Service Desk
- Create ticket in Zendesk
- Connect to external system
Actions are not limited to above and there can be custom actions built to automate within IDHub

Workflow Automation Tools
IDHub is a customizable solution, allowing you to create the exact flows needed for your business. IDHub's workflow automation tool collectively contributes to a more secure, efficient, and compliant identity and access management environment for your organization.
- Create flexible workflow automations to perform actions based on if/then logic
- Use web-hooks to receive data from any service or send requests to any URL
- Use out-of-the-box rules, or build the exact rules you need
- Do all this without writing code or running servers
Compliance Tools for Cyber Security
Cyber Security Tools
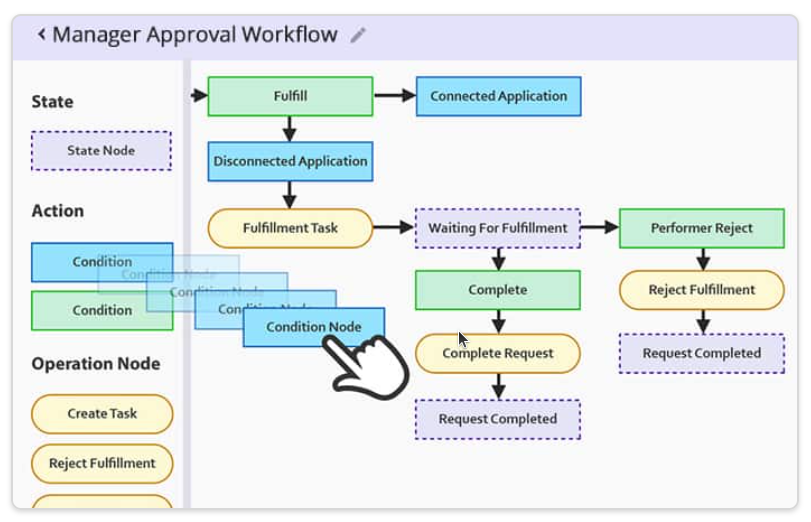
Customizable Approval Workflow Templates
Download our most common Workflow Templates, including editable versions in Visio, SVG, and PDF formats. Completely free to you.
Cybersecurity Assessment Template
Discover why cybersecurity assessments are vital for regulated industries—plus a free template to strengthen security, manage risk, and stay compliant.

Access Control Policy Template for Organizations
Utilize our free Access Control Policy Template to help establish a healthy framework for your access control. Easy to customize and share with your team.