Identity Management Proxy Users
Improve workflow continuity and security with Identity Management Proxy Users. Automatically delegate tasks when key users or managers are unavailable, so access requests, approvals, and reviews stay on track. Reduce delays, maintain compliance, and keep your identity management processes running smoothly.
IAM Proxy Users
In Identity and Access Management (IAM), critical workflows often rely on specific users to approve access requests, perform reviews, or complete key tasks. But when those individuals are unavailable, the entire process can stall, putting security, compliance, and efficiency at risk.
Proxy User Access solves this by allowing designated users to act on behalf of others, keeping IAM processes running smoothly. Whether it's for approvals, escalations, or task completion, proxy access ensures business continuity and minimizes delays in identity security workflows.
Maintain Workflow Continuity
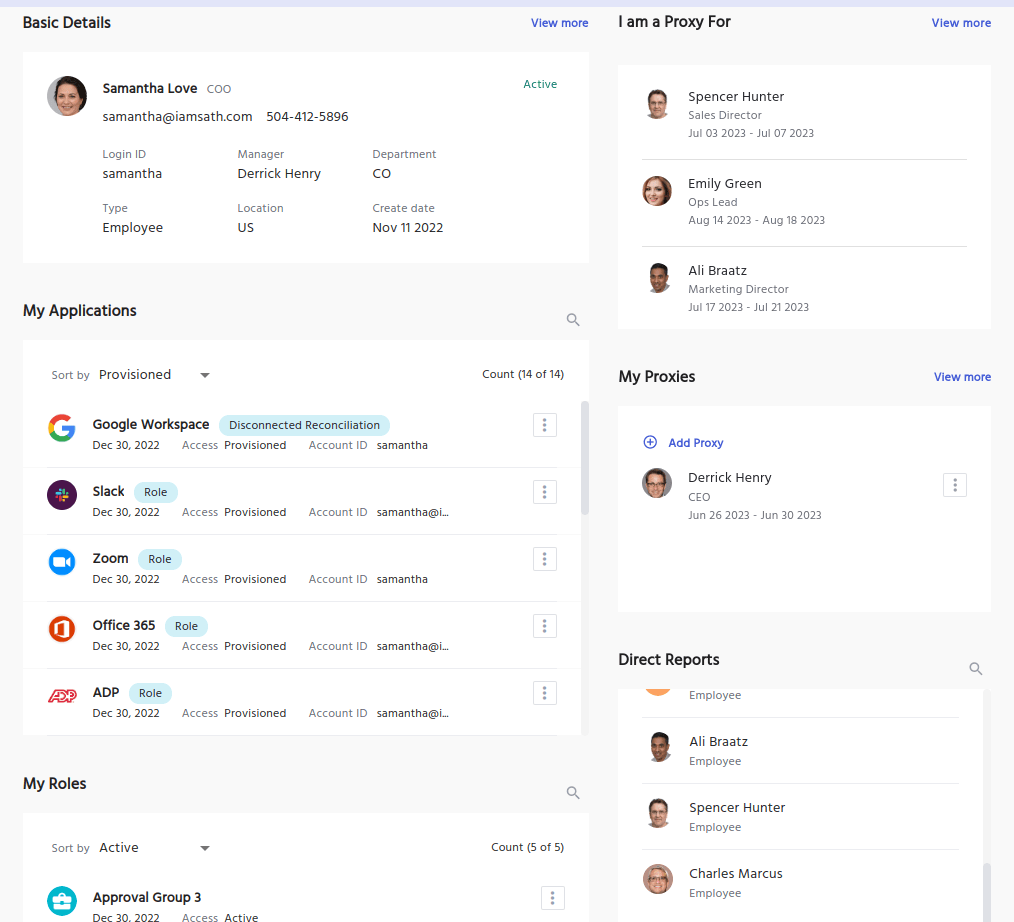
Proxy Users in IDHub
In IDHub, a Proxy User is an active user account designated to act on behalf of another specific user when they're unavailable, whether temporarily or permanently. This feature is essential for keeping Identity and Access Management (IAM) processes uninterrupted.
IDHub users are often responsible for critical tasks like approving or fulfilling access requests, performing access reviews, or completing steps within custom workflows tied to their role. When these tasks are delayed due to user absence, it can create compliance gaps or stall key operations.
With Proxy Users, preassigned accounts can seamlessly take over these responsibilities. Proxy access ensures all assigned tasks, approvals, reviews, and workflow actions, are completed on time, preserving both security and operational efficiency.
Proxy User Rights
Proxy users' rights are not elevated from their standard user rights. There is not a specific Proxy Authentication process, Proxy User password, or even a temporary password for accessing the system.
Proxy User accounts will function exactly as they did when not assigned as a proxy.
We suggest if you are in a position where you're required to complete tasks requiring elevated access, users should choose either a manager, supervisor, or someone with matching access levels.
Proxy User Actions
There are no specific Proxy user Permissions so they are limited to the ability to accomplish any task that would have otherwise been assigned to the original Destination User they are standing for.
They will utilize the regular client connections and basic login procedures to access their non-proxy accounts as normal.
There is not a specific proxy login process or proxy passwords, so users will be able to use their basic direct logins.
The most common scenarios for using a proxy would be for things like approving access for someone or carrying out a service request task which would have been required by the original user such as, updating a physical document, gathering physical equipment, modifying a user, or fulfilling a step in the provisioning process.
Learn more about Manager Level Access Control and how gives managers the flexibility they need.
Why to Assign a Proxy
One of the additional features of assigning a proxy is that you can change it at any time, and set it to only be active for a specific range of time.
Having the flexibility to choose who and when you would like someone to act as your proxy makes them the perfect solution for things like vacations, offsite meetings, or any other scheduling conflict.
In addition, when not designated for a specific event, they are perfect to have a built-in contingency plan in the event of a sudden departure from employment with the company for any reason.
Assigning Proxy Users in IDHub
IDHub out-of-the box does not default Proxy Users, however you can configure it that way. If a default Proxy has not been configured, you will need to choose one, and potentially change it to default at a later time.
Steps to assign a Proxy
Assigning a Proxy User in IDHub can be done from the User Profile, and is quite simple.
- Click on “Add Proxy”
- Select the Proxy date(s)
- Select the user you'd like to assign as Proxy, or select your Manager
- Accept and Assign
Compliance Tools for Cyber Security
Cyber Security Tools

Access Control Policy Template for Organizations
Utilize our free Access Control Policy Template to help establish a healthy framework for your access control. Easy to customize and share with your team.
Cybersecurity Assessment Template
Discover why cybersecurity assessments are vital for regulated industries—plus a free template to strengthen security, manage risk, and stay compliant.