User Provisioning
In the digital world, security is of the utmost importance, and automating Identity and Access Management (IAM) is a key component in modern technology, transforming the way we manage our data and identities.
Structured user provisioning is not only about security and control, but also about simplifying processes to make them easier to use and understand.
A well defined user provisioning process allows organizations to quickly and easily manage user access to networks, applications, and systems, significantly reducing manual overhead and enforcement costs, while ensuring users have secure access to the data and resources they need.
IAM provisioning is a critical component of IT infrastructure.
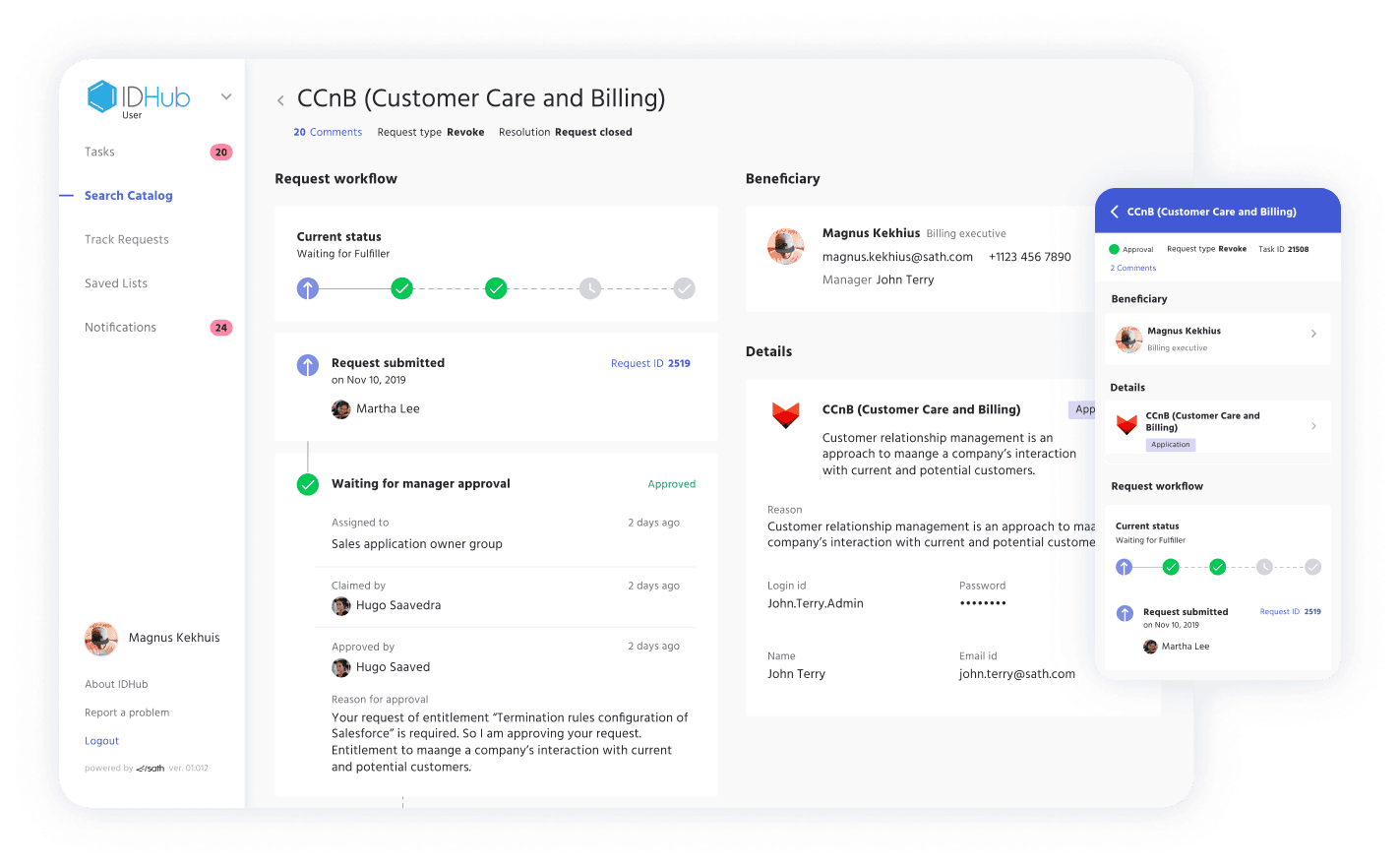
Auto Provisioning
IDHub makes automated user provisioning to cloud and on-prem applications simple and efficient by utilizing provisioning tools like the workflow engine and roles, to fully govern user access control.
IDHub's provisioning engine increases the stability of systems, while insulating the core stack from an outage, and preventing any problems from occurring on isolated systems.
It integrates with connectors using a standard-based protocol and offloads the tedious work outside the core stack.
Application Software Integration
IDHub connectors are standalone, platform-agnostic applications encapsulating all target system interactions.
IDHub core connects to the target system via application integrations called connectors, used to provision user accounts, entitlements, and other organizational cloud and on-prem resources.
SCIM Integration
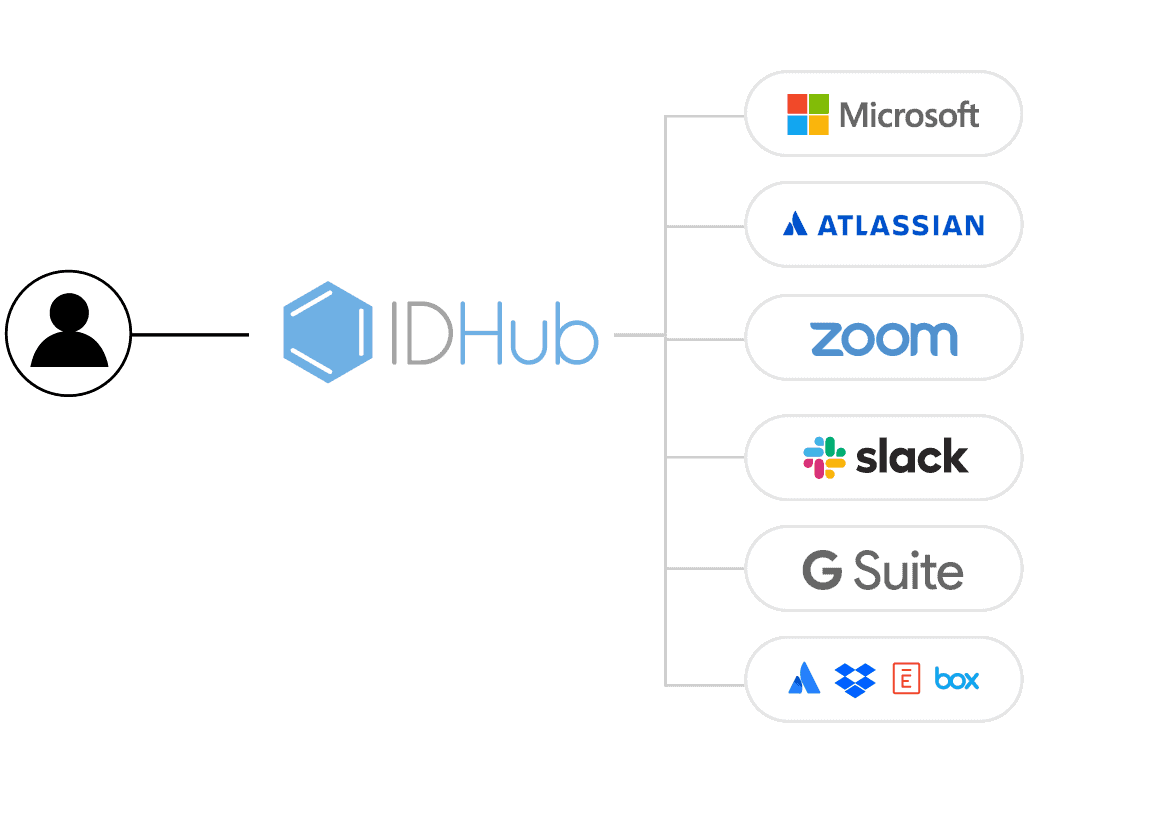
IDHub connectors consist of SCIM and other REST endpoints used to perform operations on a target system.
The connectors are developed and maintained independently by the mainline, IDHub.
They are self-contained processes running on a server/platform, directly connected to target systems.
In some cases, connectors can also run on the Target System Servers.
Every application is connected over SCIM connectors. All provisioning actions are REST API calls to a SCIM bridge, that is written in a language native to the target system.
Automated Onboarding
Automated onboarding is a streamlined and technology-driven process that efficiently handles the provisioning of user accounts, access permissions, and necessary resources for new employees, enhancing the overall onboarding experience.
IDHub connects to your source of truth, and takes the manual work out of on-boarding and off-boarding new employees.
This video gives a quick overview of new user onboarding, and auto cloud provisioning using IDHub Roles to Microsoft Entra ID (previously known as Azure AD).
This newly onboarded user gets automated provisioning to a Group when using the connector.
Just In Time Access
IDHub has the capability of limiting user access to specific resources, for a predefined period of time. This is especially useful for organizations who have temporary employees or 3rd party contractors who need access to company resources for a limited amount of time.
Just-in-time access, or time-based access, is generally initiated using Access Requests, where expiration dates and times are selected during the request process. However, time-based access provisioning can also be assigned to IDHub Roles, which are a collection of resources.
Once the request is approved, the user will have access until the expiration date/time has been fulfilled, triggering a revocation event to begin the deprovisioning process of that resource.
Compliance Tools for Cyber Security
Cyber Security Tools

Access Control Policy Template for Organizations
Utilize our free Access Control Policy Template to help establish a healthy framework for your access control. Easy to customize and share with your team.
Customizable Approval Workflow Templates
Download our most common Workflow Templates, including editable versions in Visio, SVG, and PDF formats. Completely free to you.
Cybersecurity Assessment Template
Discover why cybersecurity assessments are vital for regulated industries—plus a free template to strengthen security, manage risk, and stay compliant.