A Brief History Of AD
For those of us who may have been living under a proverbial IT rock for the last 20 years, you may have just been exposed to the ever-expanding world of Active Directory (AD).
Active Directory Services have come a long way in 20 plus years. Microsoft originally released their network asset management solution as a single product with Windows Server in 2000. However…
For the trivia buffs, AD actually made its debut when Microsoft previewed AD for the first time all the way back in the 20th century, 1999 to be precise.
The Active Directory Family of Services Today
Today, Active Directory is much more than its original offering. In modern conversations, Active Directory is often thought of as an umbrella term for a suite of proprietary offerings from Microsoft.
A “directory” in AD, refers to a location used to store information about “objects” on a network in a hierarchical structure. (Think: users, applications, printers, shared folders, or computers).
Originally, Active Directory was used expressly as a way to manage domains on a network.
And still today, Active Directory Domain Services (AD DS) remains one of the most popular services within the AD space.
Today's List Of Active Directory Services:
Active Directory Domain Services
Active Directory Federated Services (ADFS)
Azure Active Directory (AAD)
Lightweight Directory Services (AD LDS)
Lightweight Directory Access Protocol (LDAP)
Active Directory Rights Management Services (AD RMS)
Active Directory Certificate Services (AD CS)
So What Exactly Does Active Directory Do?
Active Directory can be very versatile, enabling administrators to manage access to a large variety of network resources across a Microsoft network.
Resources can include things like; lists, certificates, servers, folders, domains, printers, user identities, and even computer-controlled accounts.
Beyond internal networks, AD DS can connect to cloud applications when combined with other Active Directory services.
Overall, the management capabilities of Active Directory Services combined with their authentication protocol standards, have become a vital part of modern cybersecurity and proficient working environments for many organizations.
With the advent of many competitors to AD, AD is now considered one of many Directory Management Systems (DMS).
DMS allow administrators to control user access, authorization of users, and application access privileges, across a variety of networks.
This type of control allows Administrators to monitor as well as verify things like software updates, compatibility issues, and reconcile third-party application licenses.
Want to know how we launch IAM systems in days instead of months?
Schedule a demo with us and see IDHub for yourself!
The first Major Update – Active Directory Federation Services (ADFS)

In 2003, Microsoft took a significant leap in capabilities by adding Federated Services to Active Directory.
So what are federated services? The short answer is, federated services relate to multiple systems sharing authentication information.
ADFS added the capability to pass secure user credentials from AD to compatible or partner companies.
This update allows internal users to logon to external services without needing to login with a username and password. Pretty cool right?
The Next Big Leap – Azure Active Directory (AAD)

In December 2016, the release of Azure Active Directory Connect (AAD) was another considerable jump.
AAD joins an on-premises Active Directory System, to enable Single Sign-On (SSO) for Microsoft’s cloud services, such as Office 365 and other third-party applications.
Additionally, Azure AD provides Multi-Factor Authentication Security Principals to the network resources, where required.
So, what is the difference between ADFS and Azure AD?

Fair question. There are a lot of similarities between ADFS and AAD.
True, both services work as a secure token service, which provides ways to identify users or applications on a network for authorization.
However, the primary difference is that ADFS is built for on-premises control and functionality. AAD is built primarily for the cloud.
As an internal piece, ADFS requires that you control the infrastructure, where AADs cloud environment would not have the requirement.
Additionally, ADFS provides controlling local systems, file servers, internal applications, or networks.
On the other hand, as a Identity Management Cloud Service Azure Active Directory provides user management abilities to authorize and provision users in the cloud, but does not focus on the on-prem IT infrastructure.
AAD requires additional paid services, usually ADFS, to work together to create a solution that fills more gaps.
The Azure Active Directory Service is usually added on top of ADFS.
This design has allowed other Identity Management organizations to build on this architecture.
New Solutions and talented software companies offer more robust third-party applications, which are usable as an Azure AD Alternative, like IDHub.
What Does The Active Directory Structure Look Like?
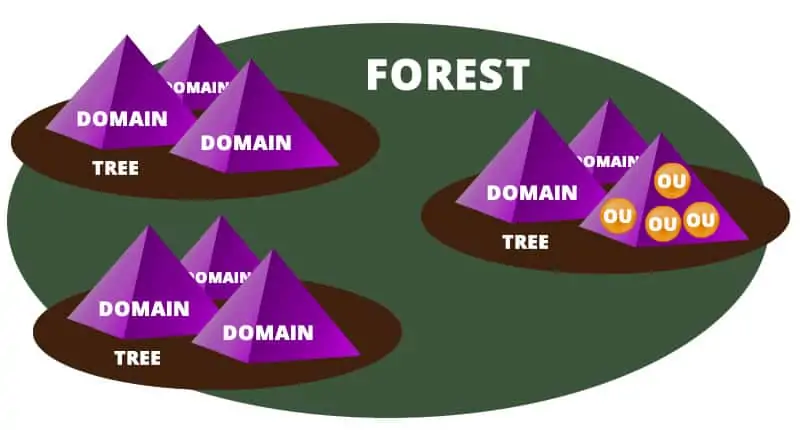
The Active Directory structure is configured in a traditional hierarchical logical structure containing several types of directory objects and elements.
The three top-level main components of AD are forests, trees, and domains.
The tree will arrange domains logically using a contiguous namespace. Domains within the tree have implicit trust with other domains inside of the tree.
Within the domains are additional objects. Domains use a DNS Structure (domain name system) and contain objects which can include organizational units, groups, devices, or users.
We will get into each of these in a bit. In the meantime, this graphic should help to visualize the high-level hierarchical structure.
What are Active Directory objects?
An Active Directory Object is a single element or resource within the network, with access to it, controlled by AD.
Objects are either resources or security principles.
Security objects will require a unique Security Identifier (SID). Active Directory allocates SIDs where appropriate.
SIDs provide the validation to grant or deny access to an object.
SID required objects will typically be things like folders, groups, permissions, user accounts, or passwords.
Resources, on the other hand, refer to physical devices such as printers or computers.
What are trees and forests in Active Directory?
A tree in Active Directory lingo is one or more domains grouped with hierarchical trust relationships, and you guessed it, a forest is a collection of trees.
The forest will contain additional information about it’s structure including additional schemas, application or domain configurations, and shared catalogs.
What is a two-way trust?
A two-way trust is when there are two domains within a tree, and each domain enables access to users of the other domain.
What is Forest trust?
As you’ve probably guessed already, a forest trust applies to domains within the entire forest and can be one-way trust, two-way, or transitive.
What is a Security Boundary?
Within a Windows network, domain administrator rights and permissions extend only to that domain, unless expressly granted by another domain. This built-in security feature is considered the Security Boundary.
What is Active Directory Replication Service?
As changes occur within a single domain, the changes are replicated and pushed to other controllers via Update Sequence Numbers (USN).
Try IDHub for FREE for 30 Days, no payment information necessary.
Try out our full working version of IDHub Cloud or Teams and explore right now!
What is an Organizational Unit (OU)?
OUs are containers built to consolidate a set of objects within a specific grouping to make life easier in AD.
OUs, within the AD structure, are always within a single domain.
However, they are capable of being nested within each other as well.
Examples of OU’s could be things like departments or physical locations of devices.
OUs typically group similar objects to allow for easier management.
What is the difference between Organizational Units and Groups?
OUs are only used to “organize” objects. They do not contain any inherent security protocols.
OUs can’t be placed on a control list, or into an actual group.
However, they do provide great value by creating a way to segment and distinguish collections of related objects together.
Examples of Organizational Units could be something like the Chicago Office or the Marketing Department.
What is Active Directory Schema (AD Schema)?
Active Directory Schema contains the formally accepted definitions of every type of object that can exist within an AD Forest.
Also, every attribute that can be created within an AD object has its definition outlined within the AD default Schema.
What Are Domain Controllers?
When Active Directory is installed on a Windows Server Operating System, the server role is created as a domain controller.
Domain controllers store the partition information for the Active Directory implementation including the Schema, Forrests, and information about the domains.
What are Requests for Comments (RFC)s?
RFCs are an industry term for memos created to establish technical specifications, policies, and protocols related to most aspects of computer networking.
RFCs are created by one of three private organizations or by independent individuals.
All RFCs are searchable and housed within the RFC Editor.
Browse RFCs by creator
Internet Engineering Task Force (IETF)
Internet Research Task Force (IRTF)
Internet Architecture Board (IAB)
asdf
RFCs Used by Active Directory
Active Directory uses standards from several RFCs. We’ve put this Active Directory RFC List together for your reference if you’re looking for some exciting reading material.
Upgrades for Active Directory
Adding Azure AD (AAD) to Active Directory, allows you to add additional capabilities.
Controlling your web applications has always been the primary purpose of AD.
AAD is still a wise choice for some people. However, the competition for cloud-based Active Directory add-ons has expanded significantly.
Now, several third-party services such as IDHub, offer advanced features that go beyond the native functionality of Azure AD, and greatly enhance the capabilities of Identity Management Systems entirely.
Users can get the most out of ADFS, while maintaining the architecture they’ve worked hard to create with their existing Active Directory install.
“Services such as IDHub, offer advanced features that go beyond the native functionality of Azure AD”
Services such as IDHub, offer advanced features that go beyond the native functionality of Azure AD
With IDHub, your System Administrators can delegate many of the frequent tasks to users who are better positioned to create custom workflows that suit their particular use.
Additionally, a user facing IAM solution like IDHub, changes the entire user provisioning process.
The customizable front-end allows individual users the ability to request new access on their own.
Managers can create custom request requirements and signup forms.
In addition, managers can create customized process and approval workflows for different applications or services.
Finally, the appropriate management can complete the approval process without ever involving the IT team at all.
The time saved by your IT experts will allow them to focus on more critical elements of your organization’s security and high-priority projects.
Want to know how we launch IAM systems in days instead of months?
Schedule a demo with us and see IDHub for yourself!
Final Thoughts
Active Directory has grown over the years to create a mix of expanded services, as needs increased.
AD is still a critical part of many organizations. However, AD has experienced growing pains, as AD technology struggles to keep up with superior alternative Access Directory Solutions.
Constant progress in networking and related superior third-party services has changed the industry’s trajectory.
The Future of Identity Management seems to be evolving and expanding at breakneck speeds, and with it, Azure ADs latest competition.
If you’re considering a solution like Azure AD Connect, or are looking to move away from Active Directory we have good news.
Jump on a call with us and we’ll give you a quick demo of how IDHub can replace or drastically improve your current Azure AD implementation.
Want to try IDHub for yourself? Download a FREE MONTH to try it out for yourself!