
Introduction
Insider threats continue to rise in the financial industry, creating significant challenges for institutions protecting sensitive data. According to the 2023 Insider Threat Report, 74% of organizations feel moderately to extremely vulnerable to insider attacks, and 60% have experienced at least one insider attack in the last year. These threats are particularly difficult to detect, as they often involve individuals with legitimate access to systems and data. The report also highlights that insider attacks are growing more frequent, with compromised credentials and negligent employees being key factors driving these risks.
What is an Insider Threat?
An insider threat occurs when someone within the organization—whether an employee, contractor, or partner—misuses their authorized access to data, systems, or processes. These threats can be intentional, like stealing customer data or manipulating financial transactions for personal gain, or unintentional, like mistakenly sharing sensitive information or failing to follow security protocols.
Insider threats are particularly concerning in the financial sector because they often target critical information like customer records, transaction details, or internal financial reports. Addressing these risks is important because they can lead to significant financial loss, compliance issues, and damage to an institution's reputation—understanding who has access to what and monitoring that access are important steps in effectively managing these risks.
How Financial IAM Protects Against Insider Threats
Access Control and Least Privilege Principles
In financial institutions, where sensitive customer data, account information, and transaction records are constantly handled, limiting who has access to what information is crucial to preventing insider threats.
The principle of least privilege means that employees are only given access to the data and systems they need to perform their jobs. For example, a loan officer should only have access to loan applications and financial records relevant to their role rather than full access to all customer accounts or broader financial systems.
Identity and Access Management (IAM) solutions help financial institutions apply this principle by managing and controlling user permissions in real time. For instance, if a teller is promoted to a management position, IAM systems can automatically adjust their access rights to reflect the new role while removing any permissions tied to their previous position. This limits opportunities for intentional or otherwise misuse and prevents individuals from retaining access to systems or data no longer relevant to their responsibilities.
Get a free copy of our mitigating insider threats info-graphic!
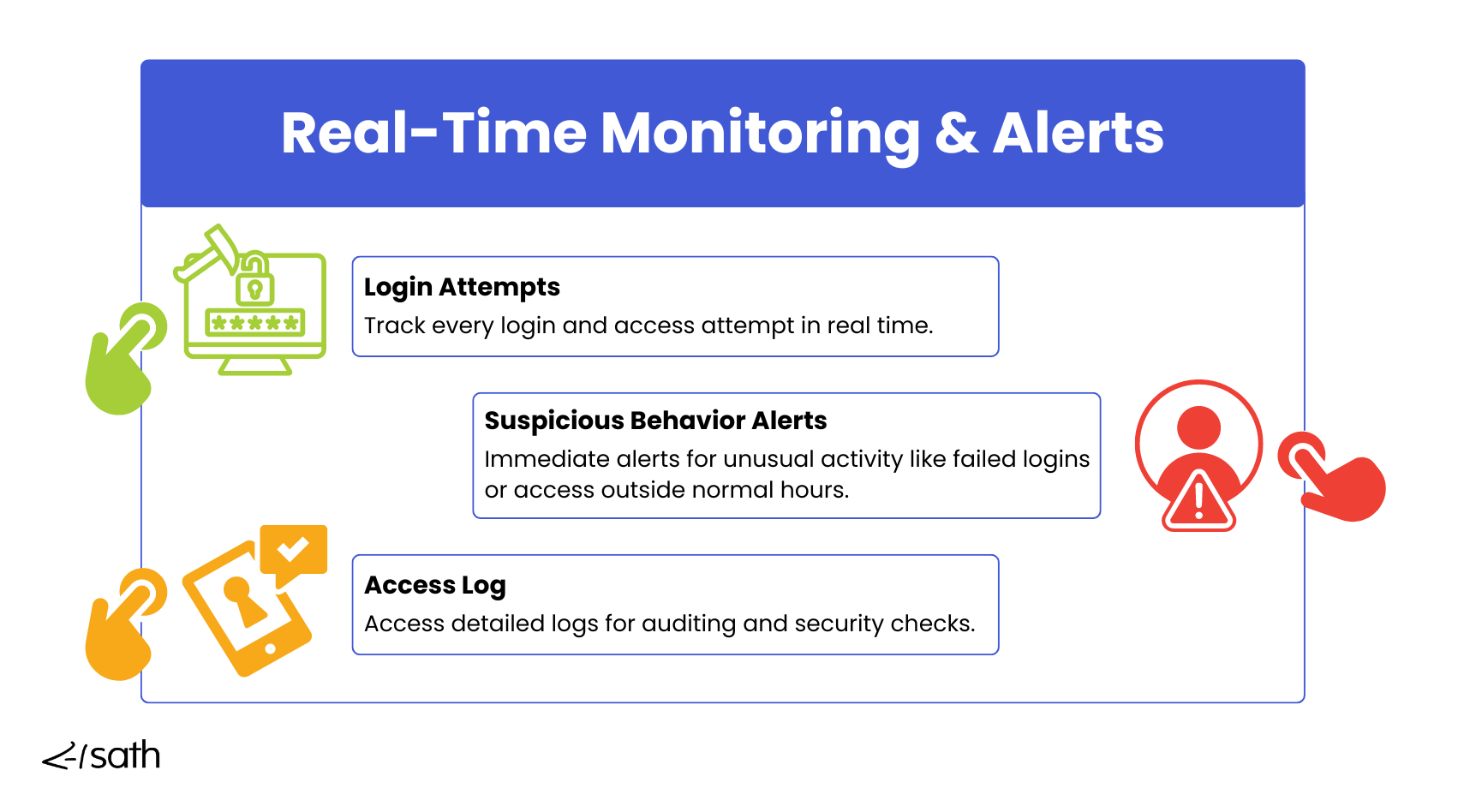
Monitoring and Auditing
Identity and Access Management systems are essential for tracking and monitoring access activities across the organization, which is especially important in the financial sector, where regulatory compliance and insider threats are serious concerns.
For instance, if an employee tries to access high-value customer accounts outside their assigned responsibilities, IAM solutions can detect this unusual behavior and flag it for further investigation.
Beyond detecting anomalies, IAM systems maintain detailed audit logs of every access request, login attempt, and system change. These logs are invaluable during both regular audits and in the event of an insider threat investigation.
If a former employee still has access to systems they shouldn't, or if a current employee is attempting to access confidential financial data they don't need, the IAM audit trails provide a clear record of when, how, and by whom access was attempted.
This level of visibility helps identify potential risks and supports compliance with financial regulations like SOX or GDPR, which mandate strict controls over sensitive data handling.
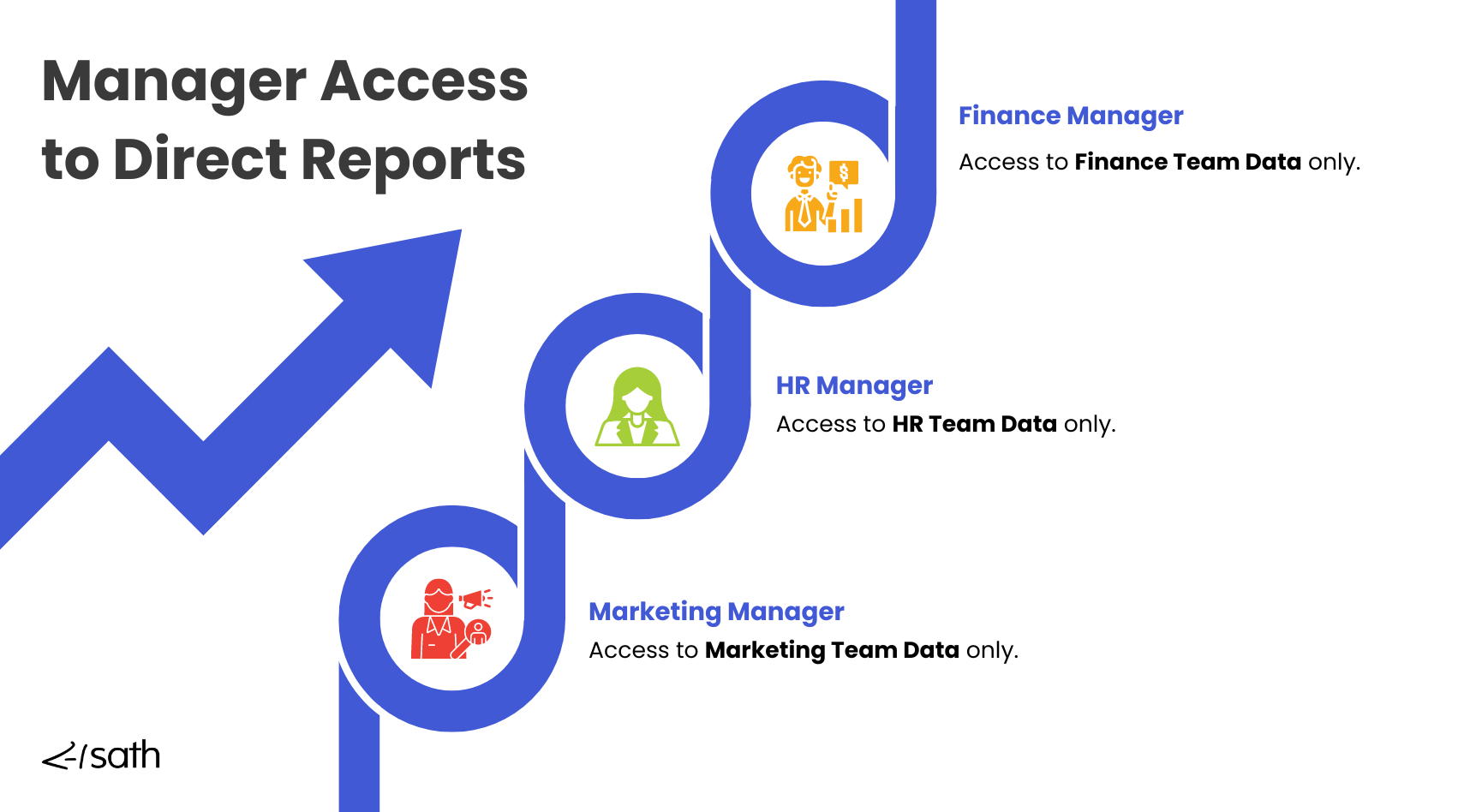
The Role of IAM in Managing Access to Direct Reports
Revoke Unnecessary Access to Direct Reports
Controlling access to employee information is necessary to protect sensitive data. Employees should only have access to information about their direct reports, limiting the risk of unnecessary exposure.
For example, a manager in the marketing department shouldn't be able to access employees' personal or performance data in the IT department. This helps safeguard internal data and prevents the potential misuse of information.
Identity and Access Management systems make it simple to revoke access when someone leaves the organization or switches roles. For instance, when a supervisor moves to a non-managerial position, access to their former team's data is immediately removed. This automation eliminates manual adjustments and helps ensure that access rights are always up-to-date, minimizing security gaps caused by outdated permissions.
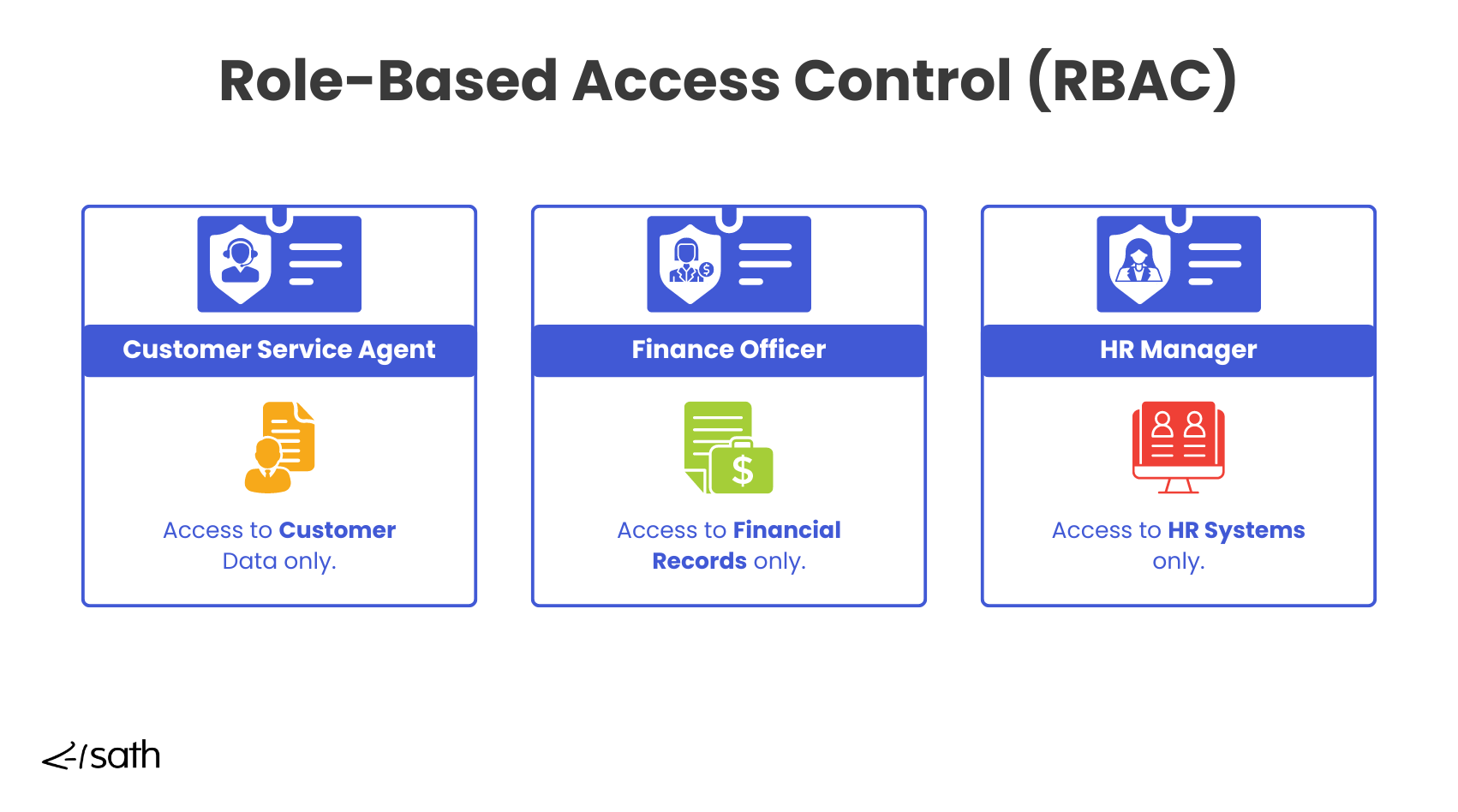
Identity Management systems accommodate immediate revocation of access when a change takes place in the user account through the use of Role-Based Access Control (RBAC) and/or Access Reviews.
Limit Manager Access to Only Their Team
Maintaining clear boundaries between teams and managers is important for securing data in financial institutions. If access permissions are misaligned, sensitive information could be exposed to the wrong people. For example, a manager in the customer service team should be able to view employee data outside the HR department. This helps avoid potential conflicts and protects employee privacy.
IAM systems strictly control access based on the company's organizational structure. Managers are only allowed access to the employees they directly oversee, preventing cross-team access. This setup helps to prevent unauthorized access to sensitive employee information, maintaining security and accountability throughout the organization.
Get a free copy of our mitigating insider threats info-graphic!
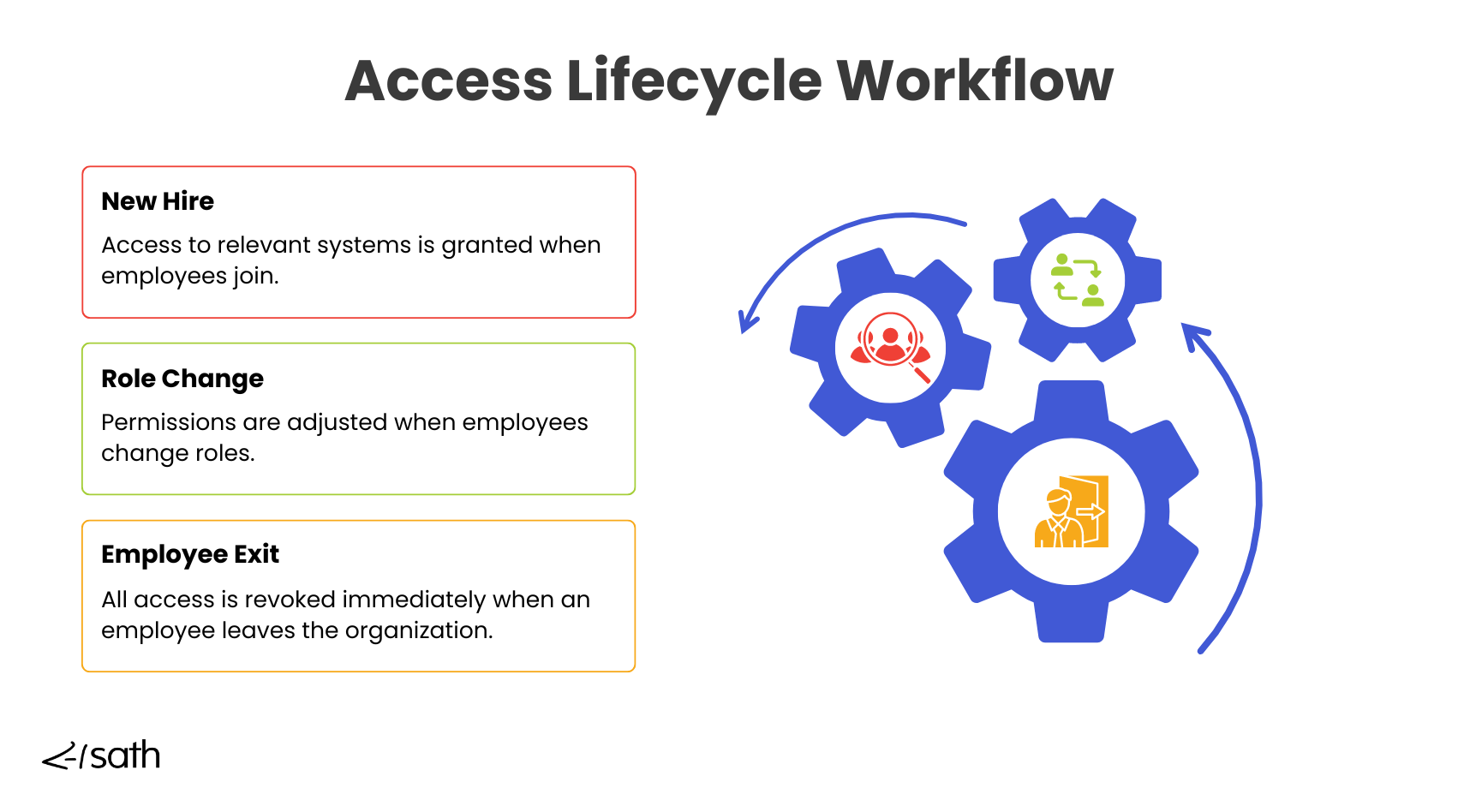
Ensure Managers Only Access Their Own Direct Reports
IAM’s Role in Assigning Direct Access
IAM solutions play a significant role in limiting access to sensitive information within an organization. These systems are designed to restrict access so that only direct managers can view or manage the data of their immediate team members.
For instance, a department head can see the performance reviews or payroll details of their staff but not those of employees from other teams or departments. This level of control helps maintain privacy and security across the organization.
IAM systems also streamline access adjustments when employees switch roles and departments or leave the company. For instance, when someone is promoted or transferred to a different department, IAM automatically updates their access rights to match the new role. It does this using Role-Based Access Control, RBAC. If they leave the organization, all their access is revoked right away. This automated workflow reduces the risk of lingering access permissions and helps keep internal data secure.
Real-Time Adjustments for Role Changes
When employees experience a change in their role, such as a promotion or a lateral move to another department, IAM systems automatically update their access privileges in real time. This is important because it allows for gaps where employees might retain access to information from their previous roles.
To illustrate, suppose a team member is promoted from an analyst to a manager. In that case, their access rights are updated instantly to reflect their new responsibilities without giving them unnecessary access to unrelated data.
Real-time updates also apply when employees leave the company or change teams. If someone resigns, IAM will immediately revoke their access to all internal systems, preventing any unauthorized activity.
Similarly, when an employee is reassigned to a new team, IAM will adjust their permissions to match their new team, ensuring they only have access to relevant information moving forward. These automated updates help financial institutions maintain tight control over sensitive data.
Benefits of IAM in the Financial Sector
Reducing the Risk of Insider Threats
Financial institutions deal with sensitive data, such as customer accounts, transactions, and investment details, which makes insider threats a significant concern. IAM helps manage these risks by restricting access to only what each employee needs for their role.
For example, a financial advisor should only access their clients' portfolios rather than general customer data across the organization. By limiting access, IAM helps prevent misuse or unauthorized access that could lead to breaches or financial fraud.
Financial organizations can also ensure access policies align with industry regulations and IAM. When employees leave or change roles, IAM systems automatically adjust their access rights, preventing any risk from leftover permissions. This tightens internal security, directly protecting sensitive data from potential insider threats.
Compliance and Regulatory Requirements
Meeting compliance standards is a top priority for financial institutions. Regulations like GDPR, SOX, and PCI-DSS demand strict data control. IAM systems are essential for helping financial institutions meet these requirements by tracking and logging every access event. This tracking makes it easy to prove compliance during audits and reduces the chance of fines for non-compliance.
IAM solutions also simplify the process of staying compliant. For example, GDPR requires careful handling of personal customer information, and any unauthorized access must be reported. IAM can automate this tracking, allowing financial institutions to quickly identify and report access issues. This makes regulatory compliance smoother and reduces the workload on internal teams.
Identity Management systems should also include a detailed Access Review module that allows for timely access reviews to ensure access creep isn't a problem and every user has only the access they need, well before audits take place. Second to access reviews, IAM should entail robust reporting, allowing admins to run any data requirements needed for the audits.
Improved Operational Efficiency
IAM brings significant efficiency gains to financial institutions by automating how access is managed across large teams; instead of manually updating user permissions when an employee is promoted or changes departments, IAM systems automatically adjust access based on job roles. For instance, when a branch manager moves to a regional role, their system access is updated without manual input.
This automation reduces potential errors and saves IT and management teams time. Instead of dealing with repetitive access control tasks, they can focus on more important responsibilities. Overall, IAM simplifies operations, cuts down on administrative work, and helps financial institutions run more smoothly while keeping their systems secure.
Conclusion
Identity and Access Management is a crucial solution for financial institutions looking to protect themselves from insider threats, meet regulatory standards, and improve operational efficiency. IAM keeps sensitive data secure by managing access rights and automating updates as roles change. If you want to strengthen your organization’s defenses, book a consultation with us today to explore how our IDHub can support your financial institution.
Continue Part 5 of this finance series: How IAM Prevents Financial Fraud in Banking