How do you know who has access to what?
Are you looking to have clear insight into who has access to what within your organization? Are you finding it difficult to meet compliance mandates and provide timely reports? Do you wish there was an easier way to remove access instantly when an employee leaves? Are you and your team spending an excessive amount of time managing user access levels manually, when you really need something automated?
Countless individuals and organizations encounter these precise challenges, leading to extensive, time-consuming efforts and resource allocation that could otherwise be directed towards more critical endeavors.
Fortunately, Identity and Access Management (IAM) solutions were created to address access challenges just like these, making it easy and efficient to control and manage digital identities and access rights.
What is IAM?
Identity and Access Management solutions help organizations manage and control individual users that have access to their digital resources, helping to bridge any security gaps. Its main purpose is to ensure the right access, for the right people, to the right systems.
Key principles of Identity Management include access management, identity provisioning and deprovisioning of digital identities and user accounts, the principle of least privilege, role-based access control, automations, access policies, access requests, and the full user lifecycle.
Access management involves controlling user permissions, user privileges and user roles, and their levels of access, while identity provisioning and deprovisioning is the process of granting and revoking access to company resources.
The principle of least privilege states that users should only have access privileges to the resources necessary for their role, while role-based access control assigns user privileges based on job functions and job roles.
Automations in IAM streamline repetitive tasks, while access policies define permissions for users, roles, or groups, ensuring secure resource interactions.
IAM access requests involve users requesting access to organizational resources and permissions, while identity lifecycle management oversees the end-to-end management of user identities within a system.
IAM systems work by providing a centralized platform for managing user identities and access permissions, allowing organizations to enforce security policies, and monitor and audit user activity to protect their digital assets.
What is the primary goal of IAM
The primary goal of Identity and Access Management (IAM) is to enhance data security, reduce security risk and cyber threats, streamline user access to resources, ensure regulatory compliance and auditing, and provide scalability with a user-friendly interface.
IAM aims to strengthen data security by controlling and monitoring user access to sensitive information and resources. By implementing strong authorization mechanisms and access controls, IAM helps prevent unauthorized access and potential data breaches.
IAM also focuses on streamlining user access by efficiently managing user identities, permissions, and role-based access, making it easier for authorized users to access the resources they need while minimizing the risk of insider threats.
Ensuring compliance and auditing are critical aspects of IAM, as it helps organizations meet regulatory requirements and internal policies. IAM provides a centralized platform for managing and documenting user access, making it easier to demonstrate compliance during audits.
Scalability is another primary goal of IAM, as organizations need a solution that can grow alongside their business and adapt to changing user access requirements.
Lastly, providing a user-friendly interface is essential for IAM to be effective. A user-friendly interface makes it easier for administrators to manage access controls and for end-users to navigate the system, leading to higher adoption rates and improved overall security.
What is an IAM example?
Identity and Access Management Solutions are designed to sync with a company's source of truth, like Microsoft Entra ID (previously Microsoft Azure Active Directory), which allows for immediate changes to user permissions, when any attributes (specific characteristics of this user) change in the user profile, like job title, department, location, status, etc. User provisioning to attribute specific permissions like Entra ID groups can be done using role-based access which allows for granular user permissions. This helps ensure. Access to company resources is controlled, and employees have the access they need in order to perform their job effectively.
In addition, IAM can provision and deprovision users automatically, instantly on-board new users, and automatically process revocations, when an employee leaves the company. This means that when job titles change, employees are onboarded, or when an employee is terminated, access to systems and resources are automatically adjusted to reflect these changes. This not only saves time and effort for IT administrators, but also significantly reduces the risk of security breaches due to outdated access permissions and unauthorized users.
Allow us to guide you on your IAM journey.
With a rich history spanning over two decades, Sath Inc. stands as a trusted industry leader, dedicated to helping businesses effectively manage access control in a secure manner. We grasp the real-world challenges that organizations face in maintaining secure access and compliance. Our extensive experience, demonstrated through successful IAM system implementations, positions Sath Inc. as a genuine and reliable service provider, ensuring that your organization receives not just a solution, but a trustworthy partner in navigating the complexities of identity and access management.
Our Plan
As an IAM service provider, we possess the proficiency and tools to address your access control challenges through our established methodologies. Here's how we plan to assist you:
- Discovery Phase:
Our experts will collaborate with your team during a comprehensive discovery phase, diligently assessing your current challenges and specific requirements.
- Tailored Solution with IDHub:
Leveraging our proprietary software solution, IDHub, we will customize and tailor it to precisely meet the unique needs and security considerations of your business. This will be validated through a proof of concept to ensure alignment with your objectives.
- Smooth Implementation and Support:
Our dedicated team will guide you through a seamless implementation of IDHub, providing robust support throughout the process. We are committed to ensuring that your experience is not just a deployment but a collaborative journey towards optimized access control.
Our Solution
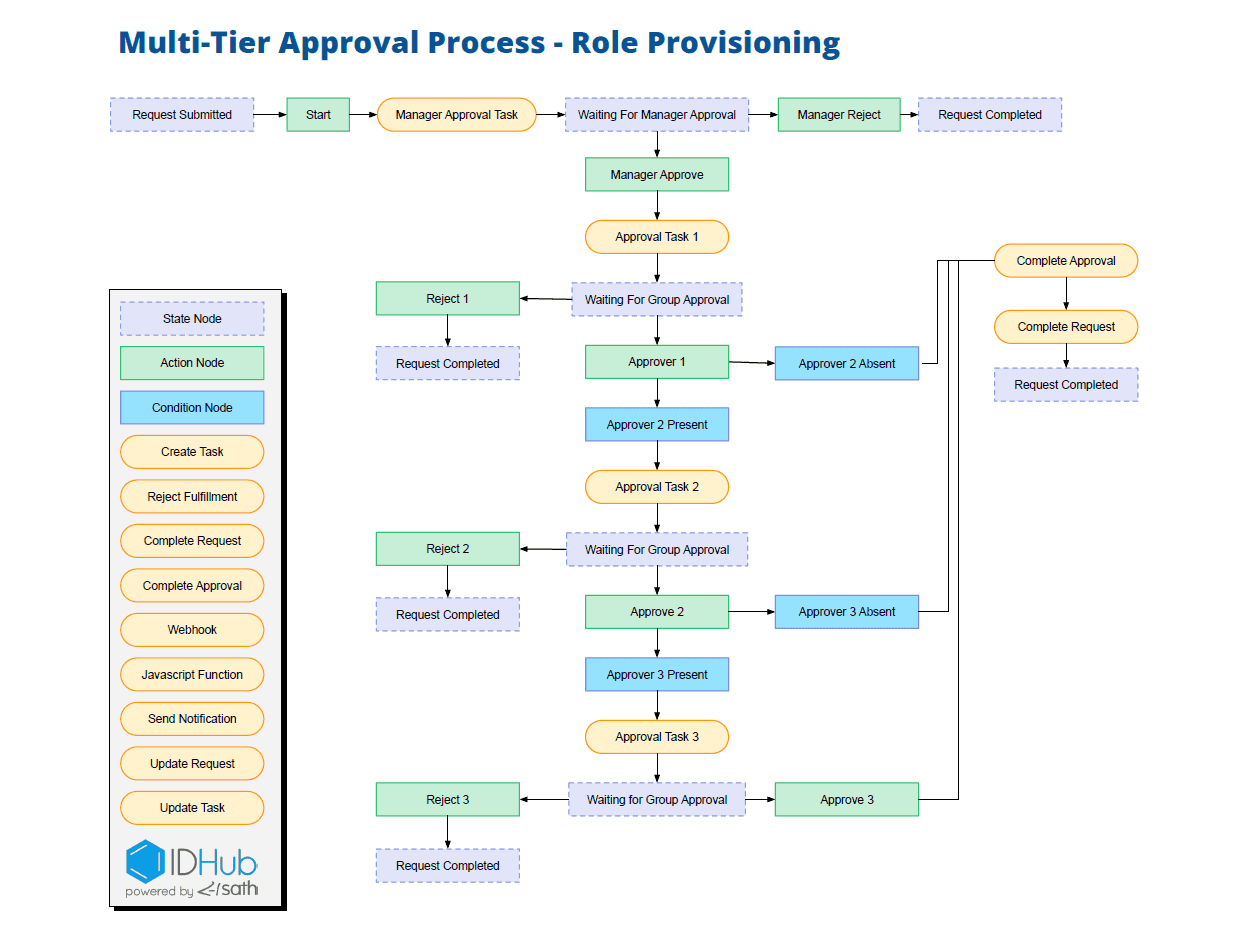
After years of managing various IAM platforms, we built an advanced IAM solution, IDHub.
IDHub is a simple identity and access management tool and ready to use, without the need for extensive technical experience. Additionally, the platform is easily tailored to the specific needs of an organization.
This means organizations can quickly customize IDHub to fit their unique requirements, providing a personalized IAM solution that aligns with their specific security and access management needs.
IDHub connects seamlessly with many cloud-based applications, allowing for a more efficient and secure process of granting and revoking access to these applications, while also ensuring regulatory compliance.
Ready to take control of your security?
Don't let another day pass with potential security gaps, exposing your organization to vulnerabilities. By adopting IDHub, you can confidently assure stakeholders that your organization is safeguarded.
Take the first step – initiate a call.
Schedule yours now via the button below.
Learn more about the expense of IAM in this post: Why is Identity Management so expensive?