Okta Guide
The purpose of this guide is to provide detailed information regarding the Okta connector. There are a number of things you can learn about this connector here, including information about its configuration and deployment.
About Okta Connector
In IDHub, you can create and onboard Okta applications using the Okta connector.
Connector Version
Okta connector is currently at Version 1.0. More Okta operations and other capabilities will be supported in upcoming updates and releases of the Okta connector.
| Component | Version |
|---|---|
| Okta Connector | Ver 1.0 |
| Target System | Okta |
Connector Operations
| Operation | Supported |
|---|---|
| User Management | |
| Create user | Yes |
| Update user | Yes |
| Enable user | Yes |
| Disable user | Yes |
| Delete user | Yes |
| Group Management | |
| Add and Remove Okta Groups | Yes |
Connector Components
The components of the connector include Connector Application, Connector Application Configuration, Connector Service Provider Interface, Splice, and Splice configuration.
These connection components contain precise connectivity and setup information for your target system. The connector takes information from these files to allow you to quickly and efficiently onboard your applications using a single, streamlined UI.
Connector Architecture
The connector's architecture is constructed in accordance with the diagram below:
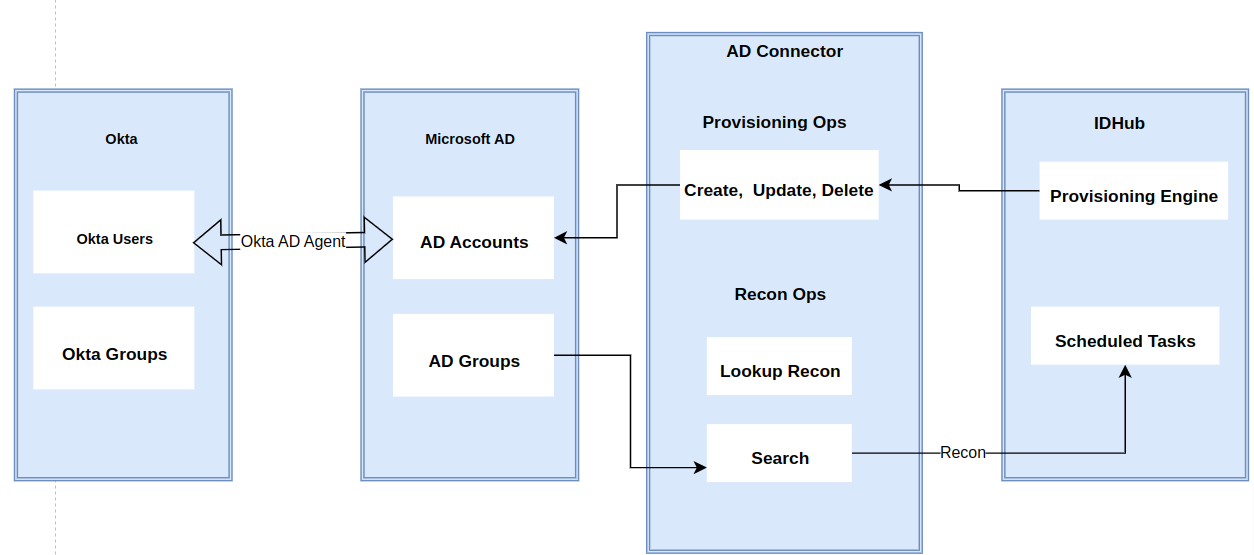 The connector architecture primarily consists of a connector application and a target system component, as seen in the screenshot up above. The native communication with the target system is handled by the target system by leveraging the SPI implementation of the Okta Specific connection. This architecture is implemented because it allows for rapid and straightforward connector deployment as well as precise versioning capabilities.
The connector architecture primarily consists of a connector application and a target system component, as seen in the screenshot up above. The native communication with the target system is handled by the target system by leveraging the SPI implementation of the Okta Specific connection. This architecture is implemented because it allows for rapid and straightforward connector deployment as well as precise versioning capabilities.
Use cases for the connector
Okta Account Management
IDHub leverages your organization's existing Active Directory structure to efficiently retrieve Okta user account information. This streamlined process utilizes Distinguished Names (DNs) to pinpoint specific users or user groups within your Active Directory.
The data retrieved through this secure integration encompasses a comprehensive range of user attributes, including:
- Unique identifiers (samAccountName)
- Full Name (Common Name)
- First Name
- Last Name
- Display Name
- Telephone Number(s)
- Email Address(es)
- Department Affiliation
- Job Title
- Employee Type
Additionally, IDHub offers the flexibility to accommodate your specific data requirements. You can extend the retrieved attributes beyond this standard list to ensure a complete user profile within IDHub. Leveraging IDHub's Attribute based Access Control (ABAC), you can decide which information will be used on new user creation and which ones on user modification.
Okta Entitlements
While IDHub utilizes the LDAP connector to synchronize user account information, it currently focuses on a specific entitlement type for provisioning and de-provisioning purposes: Directory Groups. This approach leverages the existing group structure within your Active Directory. Your organization's employees can request the synchronization of specific Okta Groups that correspond to their Active Directory Group counterparts. This streamlined method ensures efficient user access management based on group memberships.
It's important to note that IDHub's capabilities are constantly evolving. Future enhancements may include the ability to synchronize additional entitlement types for a more granular provisioning and de-provisioning experience.
Okta Group Management
IDHub's Okta connector establishes a secure connection with your organization's Active Directory. This connection acts as a conduit to synchronize directory group information with your Okta instance. This robust integration empowers you to:
Target Specific Directory Structures: Leverage Distinguished Names (DNs) to pinpoint and synchronize specific parent directories, child directories, or a combination of both.
Flexible Configuration Options: IDHub offers granular control over the directory synchronization process. You can customize the fetch behavior to target specific DNs or include entire directory hierarchies.
Multi-DN Targeting: The LDAP connector seamlessly handles targeting multiple DNs, enabling the efficient synchronization of a broader range of directory groups.
All synchronized directory groups are categorized as 'Entitlements' within IDHub. This user-centric approach allows your employees to submit access requests for specific directories through a streamlined interface.
Following a defined approval workflow, IDHub's automated fulfillment system grants access to the requested directory upon successful completion. This intelligent system leverages Active Directory's inheritance rules to automatically provision access to child directories within the approved hierarchy.
Configuring the Connector
Since IDHub leverages AD for establishing connection to Okta, therefore Basic & Advanced Configurations for the connector will be related to the AD Connector. Please click here for more details and information on the same.
Connector Splice Design
Account Schema
{
"id": "urn:sath:params:scim:schemas:ldap:2.0:Account",
"name": "Account",
"description": "User Account",
"schemas": [
"urn:sath:params:scim:schemas:core:2.0:Schema"
],
"meta": {
"resourceType": "Schema",
"location": "/v2/Schemas/Accounts"
},
"attributes": [
{
"name": "cn",
"multiValued": false,
"description": "The UserLogin / id of the user. REQUIRED.",
"returned": "always",
"uniqueness": "global",
"required": true
},
{
"name": "givenName",
"type": "string",
"multiValued": false,
"description": "The FirstName of the user. REQUIRED.",
"returned": "always",
"required": true
},
{
"name": "sn",
"type": "string",
"multiValued": false,
"description": "The LastName of the user. REQUIRED.",
"returned": "always",
"required": true
},
{
"name": "displayName",
"type": "string",
"multiValued": false,
"description": "The DisplayNameame of the user. REQUIRED.",
"returned": "always",
"required": false
},
{
"name": "telephoneNumber",
"type": "string",
"multiValued": false,
"description": "The phoneNumber of the user.",
"returned": "always",
"required": false
},
{
"name": "mail",
"type": "string",
"description": "The mail alias for the user.",
"required": true,
"returned": "always",
"multiValued": false
},
{
"name": "entityBaseDN",
"type": "string",
"description": "The user base DN",
"required": false,
"returned": "always",
"multiValued": false
},
{
"name": "password",
"description": "Account password, Required for Creation Only",
"required": false,
"returned": "never",
"multiValued": false
},
{
"name": "entitlements",
"description": "Assigned entitlement list",
"multiValued": true,
"required": true
}
],
"schemaConfiguration": {
"id": "cn",
"objectClass": [
"top",
"person",
"organizationalPerson",
"inetOrgPerson"
],
"otherDefaultAttributes": {
},
"relationshipAttribute": "memberOf",
"namingAttribute": "cn",
"defaultBaseContainerDN": "ou=People,dc=iamsath,dc=com"
}
}
Entitlement Schema
{
"schemas"``: ``"urn:sath:params:scim:schemas:core:1.0:Account"``,
"meta"``:{
"resourceType"``: ``"User"``,
"created"``:``"2011-08-01T18:29:49.793Z"``,
"lastModified"``:``"2011-08-01T18:29:49.793Z"``,
"location"``:``"https://example.com/v2/Users/2819c223..."``,
"version"``:``"W\/\"f250dd84f0671c3\""
},
"Fname"``:``"Aman"``,
"Lname"``: ``"Singh"``,
"userName"``:``"asingh"``,
"displayName"``:``"Amar Singh"``,
"phone"``: ``"+1 5555551111"``,
"email"``: ``"amansingh@sath.com"``,
"title"``:``"System Engineer"``,
"addresses"``:{
"region"``:``"Kolkata"``,
"locality"``:``"west-bengal"``,
"postalCode"``:``"700064"``,
"countryCode"``:``"IN"``,
"country"``:``"India"``,
"streetAddress"``:``"Street 31"
},
"department"``:``"Research"``,
"userType"``:``"EMP"``,
"organization"``:``"Exelon"``,
"employeeNumber"``:``"132356456"``,
"manager"``:``"Alexa"
}
Deploying the Okta Connector
Click Here to know the pre-requisites, detailed steps and process for onboarding & deploying the Okta connector.
Onboard the Application in IDHub
Click here for the detailed steps for onboarding the application to IDHub