Google Workspace
The purpose of this guide is to provide detailed information regarding the Google Workspace connector. There are a number of things you can learn about this connector here, including information about its configuration and deployment.
About Google Workspace Connector
In IDHub, you can create and onboard Google Workspace applications using the Google Workspace connector.
Connector Version
Google Workspace connector is currently at Version 1.0. More Google Workspace operations and other capabilities will be supported in upcoming updates and releases of the Google Workspace connector.
| Component | Version |
|---|---|
| Google Workspace Connector | Ver 1.0 |
| Target System | Google Workspace |
| Connector Server | 11.1.2.1.0 |
| Connector Server JDK | JDK 1.6 or later |
Connector Operations
| Operation | Supported? |
|---|---|
| User Management | |
| Create user | Yes |
| Update user | Yes |
| Delete User | Yes |
| Enable user | Yes |
| Disable user | Yes |
| Change or Reset password | Yes |
| Entitlement Grant Management | |
| Add Groups | Yes |
| Update Groups | Yes |
| Remove Groups | Yes |
Connector Components
The components of the connector include Connector Application, Connector Application Configuration, Connector Service Provider Interface, Splice, and Splice configuration.
These connection components contain precise connectivity and setup information for your target system. The connector takes information from these files to allow you to quickly and efficiently onboard your applications using a single, streamlined UI.
Connector Architecture
The connector's architecture is constructed in accordance with the diagram below:
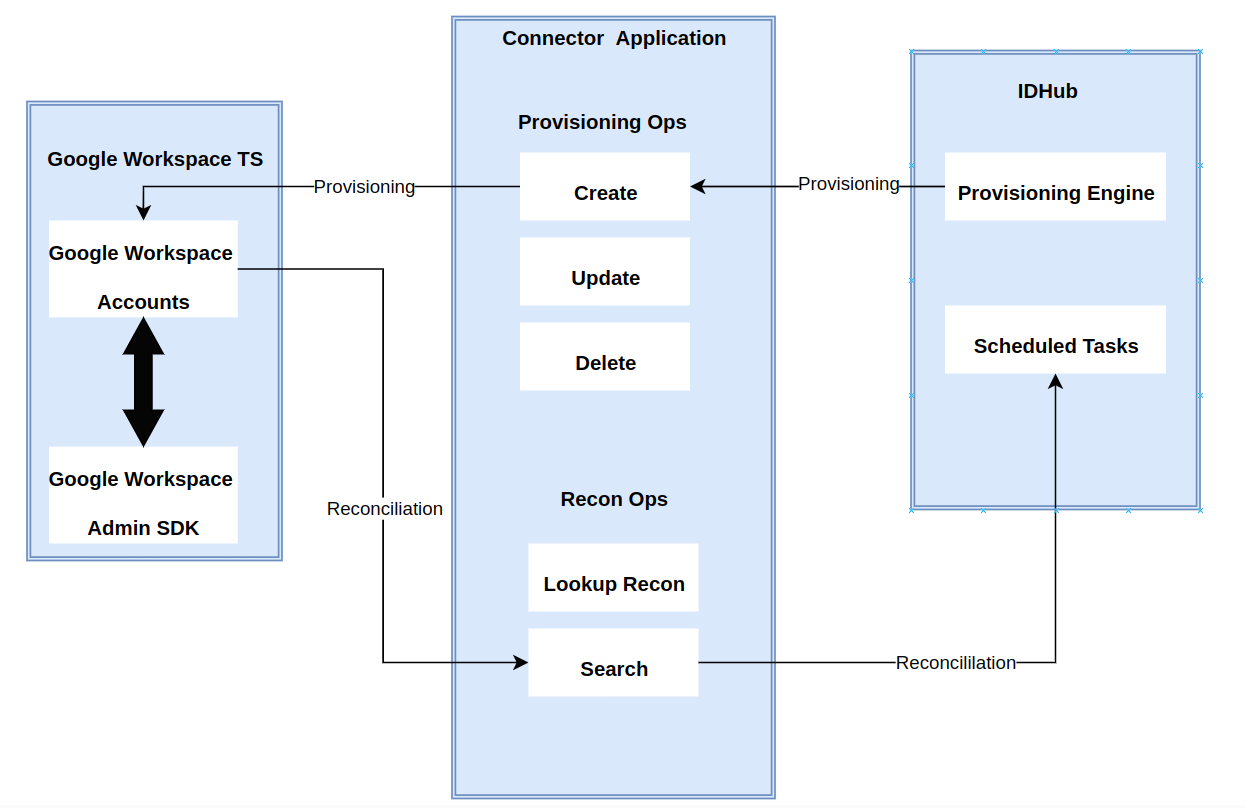
The connector architecture is basically composed of connector application, google workspace SDK controller and target system splice. The target system splice takes care of the native communication with the target system using the Google Workspace Specific connector SPI implementation. This architecture is followed and design as it enables for easy and rapid deployment of the connector as well as more precise versioning capabilities.
The connector is configured to run in one of the following modes:
- Target Resource reconciliation
- Users are instantly created and changed on IDHub in this situation if you rely on the Google Workspace application as the trusted source. When user records match the reconciliation criteria, the Google Workspace SDK retrieves them and sends them to IDHub. Each user record retrieved from the target system is cross-checked against existing IDHub Users. If there is a match between the target system record and the IDHub User, the User attributes are changed to reflect the changes made to the target system record. If no matches are identified, the target system record is utilized to generate an IDHub User.
- Account management
- This entails using IDHub to add, modify, or remove users from the target system.
- During provisioning, the connector invokes the target system's Google Workspace SDK for provisioning tasks.
- The target system's SDK accepts provisioning data, does the necessary actions there, and then sends IDHub the result back from the target system. Applications can carry out create, read, update, and delete (CRUD) actions on the target system using the Google Workspace SDK.
- This entails using IDHub to add, modify, or remove users from the target system.
In developing the connector, we adhere to this fundamental architecture. The IDHub team will handle the connector modification section appropriately based on your unique business requirements if there are any improvements, extra specifications, or variations.
Connector Features
Full Reconciliation and Incremental Reconciliation
Full reconciliation can be performed to bring all existing user data from the target system to IDHub. If the target system has an attribute that stores the timestamp at which an item is created or modified, you can configure your connector for incremental reconciliation once the first full reconciliation operation has been completed.
The connector's future release version will incorporate incremental recon, which is not supported by the present version of the connector.
Limited Reconciliation
Records from the target system can be reconciled depending on a defined filter condition. You can define the subset of newly added or updated target system records that must be reconciled in order to restrict or filter the records that are fetched into IDHub during a reconciliation process. You can specify the conditions in which the reconciliation will take place.
Batched Reconciliation
You can break down a reconciliation run into batches by specifying the number of records that must be included in each batch.
The current version of the connector do not support incremental recon & batched recon and will be supported in the future release version of the connector.
Reconciliation of Deleted Account Data
The Reconciliation task can be used to fetch details of deleted target system users. This information is used to revoke the corresponding Google Apps resources from IDHub.
Transformation and Validation of Account Data
You can configure transformation and validation of account data that is brought into or sent from IDHub during reconciliation and provisioning operations by writing Groovy scripts while creating your application.
Support for Connector Server
The connector architecture enables your application to communicate with externally deployed bundles by utilizing one or more connector servers. As a result, you have the option to run the IDHub Java connector bundle on a different host for better performance if you do not wish to execute it in the same VM as the application.
Connection Pooling
A connection pool is a cache of objects that represent physical connections to the target. IDHub connectors can use these connections to communicate with target systems. At run time, the application requests a connection from the pool. If a connection is available, then the connector uses it and then returns it to the pool. A connection returned to the pool can again be requested for and used by the connector for another operation. By enabling the reuse of connections, the connection pool helps reduce connection creation overheads like network latency, memory allocation, and authentication.
One connection pool is created for each set basic configuration parameters that you provide while creating an application. For example, if you have three applications for three installations of the target system, then three connection pools will be created, one for each target system installation.
Support for Connector Operations in Multiple Domains
The connector supports reconciliation and provisioning operations in multiple domains. By default, this connector supports reconciliation and provisioning operations within a single domain. However, you can configure the connector for performing connector operations in more than one domain by specifying a value for the supportMultipleDomain parameter in Advanced Settings.
Support for Reconciliation of Account Status
Support for reconciliation of account status is one of the features where the connector fetches the status information during a reconciliation operation. During a reconciliation run, the connector can fetch status information along with the rest of the account data.
How do you get the secrets from your GCP instance?
- You need to have access to Google API developer console and project- to create the service account, create necessary keys and provide domain wide delegation to service account.
- You would need Admin email address
- The Admin users personal Drives might show up in IDHub. It is recommended that the admin user provided in application.properties not have any personal drive or files.
- The google admin account should not be an day to day user.
- Navigate to https://drive.google.com/drive/my-drive and login with the Admin Email address and verify there are no folders or files in admin drive that you do not want to show up in IDHub.
Google API configuration
This step covers creating service account, certificate and providing domain wide permission for service account.
Enable APIs on Google Workspace
To enable an API for your project:
- Go to the API Console.
- From the projects list, select a project or create a new one.
- If the APIs & services page isn't already open, open the console left side menu and select APIs & services.
- Then select Library.
- Click the Admin SDK API . If you need help finding the API, use the search field. Click ENABLE
- Perform the above steps on Google Drive API
Ensure API Enabled check box is selected next to ‘TRY THIS API’ button
Create service account
Service account keys could pose a security risk if compromised. Delete and Create new keys (.p12 certificate) for service account every month to mitigate this risk.
- Navigate to https://console.developers.google.com/apis/credentials .
- Login with Admin credentials
- Select the correct project from the drop down menu next to (Google Cloud Platform)
- Click on
'+ CREATE CREDENTIALS'
- select 'Service Account' from the drop down menu.
- Provide a name (e.g: idhub-scim) and description to your Service Account
- Note the complete Email address.
- Click on
'DONE'
- Refresh the page if your newly created service account does not show up instantly on the credentials page.
- Click on the pencil icon next to the Service Account to edit it.
- Now Click on
'SHOW DOMAIN-WIDE DELEGATION' - Check the box for
'Enable Google Workspace Domain-wide Delegation' - Click
'Save'. - A Client ID will show up. Copy this
- Navigate to Permissions tab and add the admin user as Owner
Generate service account private key
- Click on Keys tab in the service account.
- Click on
‘ADD KEY', then'Create new key’ - Select P12 format
- Click
'CREATE' - When the pop up for file opens up, select
'Save File'and save it to a location on you computer. - Note the private key password
- Rename the downloaded p12 file as desired and store the secret in a secure store.
Configure Domain wide delegation for service account
- Navigate to https://admin.google.com on a new tab/window
- Go to Main menu > Security > API Controls.
- In the Domain wide delegation pane, select Manage Domain Wide Delegation.
Click Add new.
In the Client ID field, enter the service account's Client ID.
In the OAuth scopes (comma-delimited) field, enter the below list of scopes. (6 scopes)
https://www.googleapis.com/auth/admin.directory.user,https://www.googleapis.com/auth/admin.directory.group,https://www.googleapis.com/auth/drive,https://www.googleapis.com/auth/admin.directory.user.readonly,https://www.googleapis.com/auth/admin.directory.group.readonly,https://www.googleapis.com/auth/drive.readonlyClick
Authorize.Click on
View Detailsand verify the scopes are added.
Creating an Application by using the Connector
Onboard the Application in IDHub
Click here for the detailed steps for onboarding the application to IDHub
Configuring the Connector
Connectors use connection-related parameters to connect to IDhub with your target system and perform connector operations when creating a connected application. IDHub requires the following connection-related parameters in order to connect to a Google Workspace application.
Basic Configuration of the Connector
| Parameter | Mandatory? | Description |
|---|---|---|
| Service Account ID | Yes | Enter the email address of the service account created. |
| Service Account User | Yes | Enter the user name of account that you created to log in to the client application. Sample value: admin@mydomain.com |
| Service Account Private Key | Yes | Enter the name and complete path to the directory containing the private key. Sample value: /scratch/34567890sdfghjk.p12 |
| Google Application Name | Yes | Enter the name of the project that was created as part of registering the client application. |
| Google Domain Name | Yes | Enter the name of your Google Apps domain. Sample value: mydomain.com |
| Scope | Yes | Enter the scope of your client application. |
| Connector Server Name | No | If you are using the Google Workspace Connector together with a Java Connector Server, then enter the name of Connector Server IT resource. |
| Proxy Host | No | Enter the proxy host name. This is useful when a connector must be used in the network protected by the web proxy. Check with your network administrator for more information about proxy configuration. |
| Proxy Password | No | Enter the proxy password. This is useful when a connector must be used in the network protected by the web proxy. Check with your network administrator for more information about proxy configuration. |
| Proxy Port | No | Enter the proxy port number. This is useful when a connector must be used in the network protected by the web proxy. Check with your network administrator for more information about proxy configuration. |
| Proxy Username | No | Enter the proxy user name. This is useful when a connector is to be used in the network protected by the web proxy. Check with your network administrator for more information about proxy configuration. |
Advanced Settings Parameters
There are some advanced settings that you can configure in the connector.
In the current version of the connector, these advanced settings cannot be configured; however, they will be available in future releases.
| Parameter | Mandatory? | Description |
|---|---|---|
| Connector Name | Yes | This parameter holds the name of the connector class. |
| Connector Package Name | Yes | This parameter holds the name of the connector bundle package. |
| Connector Package Version | Yes | This parameter hods the version of the connector bundle class. |
| Pool Max Idle | No | Maximum number of idle objects in a pool. Sample value: 10 |
| Pool Max Size | No | Maximum number of connections that the pool can create. Sample value: 10 |
| Pool Max Wait | No | Maximum time, in milliseconds, the pool must wait for a free object to make itself available to be consumed for an operation. Sample value: 150000 |
| Pool Min Evict Idle Time | No | Minimum time, in milliseconds, the connector must wait before evicting an idle object. Sample value: 120000 |
| Pool Min Idle | No | Minimum number of idle objects in a pool. Sample value: 1 |
| supportMultipleDomain | No | This entry specifies whether the connector can perform connector operations in a single or multiple domain. By default, the connector performs connector operations only on the domain specified as the value of the Google Domain Name basic configuration parameter. Set the value of this entry to true if you want the connector to perform connector operations in all the domains present in Google Apps. Default value: false |
Attribute Mappings for the Connector
| Google Workspace Schema | User Schema in IDHub | Sync Direction | IsVisible | Example | Type of Attribute |
|---|---|---|---|---|---|
| country | officeAddressCountry | Bi-Directional | Visible | UK | |
| displayName | displayName | Bi-Directional | Visible | John_Depp | |
| externalId | Hidden | ||||
| familyName | lastName | Bi-Directional | Visible | Depp | |
| givenName | firstName | Bi-Directional | Visible | John | |
| id | login | Bi-Directional | Visible | John33 | Unique Key (auto generated) Account Name Field |
| locality | officeAddressCity | Bi-Directional | Visible | London | |
| meta | GoogleMeta | Bi-Directional | Visible | ||
| orgUnitPath | Hidden | ||||
| phoneNumber | phoneNumber | Bi-Directional | Visible | 8847-487-8874 | |
| poBox | Hidden | ||||
| postalCode | officeAddressPostal | Bi-Directional | Visible | 99478757 | |
| primaryEmail | Bi-Directional | Visible | John@sath.com | Reconciliation Key | |
| recoveryEmail | Hidden | ||||
| recoveryPhone | Hidden | ||||
| schemas | Hidden | ||||
| secondaryEmail | Hidden | ||||
| streetAddress | officeAddressLine1 | Bi-Directional | Visible | Boulevard St. | |
| temporaryPassword | Hidden | ||||
| thumbnailPhotoUrl | Hidden | ||||
| department | department | Bi-Directional | Visible | IT | |
| jobTitle | jobTitle | Bi-Directional | Visible | Manager | |
| managerLogin | managerLogin | Bi-Directional | Visible | Mang234 | |
| managerDisplayName | managerDisplayName | Bi-Directional | Visible | Depp | |
| Status | Status | Bi-Directional | Visible | Active | |
| location | location | Bi-Directional | Visible | London | |
| homeAddressLine1 | homeAddressLine1 | Bi-Directional | Visible | Bl. St. | |
| homeAddressCity | homeAddressCity | Bi-Directional | Visible | London | |
| homeAddressState | homeAddressState | Bi-Directional | Visible | London | |
| homeAddressZipcode | homeAddressZipcode | Bi-Directional | Visible | 4454 | |
| officeAddressZipcode | officeAddressZipcode | Bi-Directional | Visible | 3555 | |
| officeAddressState | officeAddressState | Bi-Directional | Visible | London | |
| userType | userType | Bi-Directional | Visible | Employee | |
| organizationName | organizationName | Bi-Directional | Visible | Sath | |
| employeeNumber | employeeNumber | Bi-Directional | Visible | John8678 | |
| provisionedDate | provisionedDate | Bi-Directional | Visible | 05/06/23 | |
| createDate | createDate | Bi-Directional | Visible | 05/06/22 | |
| homeAddressLine2 | homeAddressLine2 | Bi-Directional | Visible | Bl. St. | |
| officeAddressLine2 | officeAddressLine2 | Bi-Directional | Visible | Bl. St. | |
| homeAddressCountry | homeAddressCountry | Bi-Directional | Visible | UK |
- GoogleMeta is a custom IDHub field
- In order to create this field, click on the
Add New Fieldfrom the IDHub Field schema and then enter the name of the custom field in the dropdown and click onsave. Make sure that you select the Multi-Value toggle for the field.
- In order to create this field, click on the
- Sync Direction of the Attributes depends on whether you regard Google Workspace as your Trusted Source.
- You should only synchronize from IDHub to Google Workspace and not the reverse if Google Workspace is not a trusted system in your case.
Possible Recon Keys and Values
| Possible Recon Key | Possible Recon Key Values |
|---|---|
| primaryEmail | John@sath.com |
| id | John33 |
| managerLogin | Mang234 |
| employeeNumber | John8678 |
Connector Application Configuration
Connector application is designed such that it works as the wrapper application to the different scim adapters. This majorly consists of the following:
Authentication
- Basic Authentication is required
- The encrypted values of username and password will be stored in the properties file
Resource Type
These are the two resource types available for the IDHUB connector. The "resourceName" attribute value in rest api calls will have one of these values.
- Account - user account in the target system - this will include entitlement membership
- Entitlement -available entitlements in the target system
Google Workspace Connector Splice configuration
In order to provision, modify, and revoke two main resources, Accounts and Entitlements, the Google Workspace Connector Splice integrates with the IDHub Connector Application. IDHub's Account translates into a User in SCIM and Google Workspace, whereas IDHub's Entitlements translate into a Group in Google Workspace.
| IDHUB | SCIM | Google Workspace | Operation |
|---|---|---|---|
| Account | Account | User | List, Create, Modify, Delete, Add Entitlement (PATCH Only), Revoke Entitlement (PATCH Only) |
| Entitlements | Entitlement | Groups, Shared Drive | List, Create, Modify, Delete |
Connector Splice Design
Account Schema
The Account Schema configuration of the Google Workspace connector Splice is as follows:
{
"attributes": [
{
"name": "country",
"multiValued": false,
"description": "The country in which the user is located.",
"idhubFieldName": "officeAddressCountry"
}, {
"name": "displayName",
"multiValued": false,
"description": "The fullName/displayName of the user. REQUIRED.",
"mutability": "readOnly",
"returned": "always",
"required": true,
"idhubFieldName": "displayName"
}, {
"name": "externalId",
"multiValued": false,
"description": "A String that is an identifier for the resource as defined by the provisioning client.",
"mutability": "readOnly",
"returned": "always",
"caseExact": true
}, {
"name": "familyName",
"multiValued": false,
"description": "The lastName/familyName of the user. REQUIRED.",
"returned": "always",
"required": true,
"idhubFieldName": "lastName"
}, {
"name": "givenName",
"multiValued": false,
"description": "The firstName/givenName of the user. REQUIRED.",
"returned": "always",
"required": true,
"idhubFieldName": "firstName"
}, {
"name": "id",
"multiValued": false,
"description": "The unique ID for the user.",
"mutability": "readOnly",
"returned": "always",
"required": true,
"idhubFieldName": "login"
}, {
"name": "locality",
"multiValued": false,
"description": "The town or city in which the user is located.",
"idhubFieldName": "officeAddressCity"
}, {
"name": "meta",
"multiValued": false,
"description": "A complex attribute containing resource metadata.",
"mutability": "readOnly",
"subAttributes": [
{
"name": "resourceType",
"multiValued": false,
"description": "The name of the resource type of the resource.",
"mutability": "readOnly",
"caseExact": true
}, {
"name": "created",
"multiValued": false,
"type": "dateTime",
"description": "The DateTime that the resource was added to the service provider."
}, {
"name": "lastModified",
"multiValued": false,
"type": "dateTime",
"description": "The most recent DateTime that the details of this resource were updated at the service provider."
}, {
"name": "location",
"multiValued": false,
"description": "The name of the resource type of the resource.",
"mutability": "readOnly",
"caseExact": true
}, {
"name": "version",
"multiValued": false,
"description": "The version of the resource being returned.",
"mutability": "readOnly",
"caseExact": true
}
]
}, {
"name": "orgUnitPath",
"multiValued": false,
"description": "The full path of the parent organization associated with the user. If the parent organization is the top-level, it is represented as a forward slash (/).",
"mutability": "readOnly"
}, {
"name": "phoneNumber",
"multiValued": false,
"description": "A list of phone numbers of user. The maximum allowed data size is 1Kb.",
"returned": "request",
"canonicalValues": [
"$REGEX ^.{1,64}$"
],
"idhubFieldName": "phoneNumber"
}, {
"name": "poBox",
"multiValued": false,
"description": "The post office box in which the user is located, if present."
}, {
"name": "postalCode",
"multiValued": false,
"description": "The ZIP or postal code in which the user is located, if applicable.",
"idhubFieldName": "officeAddressPostal"
}, {
"name": "primaryEmail",
"multiValued": false,
"description": "Primary email address of user.",
"returned": "always",
"uniqueness": "global",
"required": true,
"idhubFieldName": "email"
}, {
"name": "recoveryEmail",
"multiValued": false,
"description": "Recovery email of the user.",
"returned": "request"
}, {
"name": "recoveryPhone",
"multiValued": false,
"description": "Recovery phone of the user.",
"returned": "request",
"canonicalValues": [
"$REGEX ^.{1,64}$"
]
}, {
"name": "schemas",
"multiValued": true,
"description": "The schemas attribute is a REQUIRED attribute and is an array of Strings containing URIs that are used to indicate the namespaces of the SCIM schemas that define the attributes present in the current JSON structure.",
"mutability": "readOnly",
"returned": "always",
"caseExact": true,
"required": true
}, {
"name": "secondaryEmail",
"multiValued": false,
"description": "Secondary email address of user. OPTIONAL.",
"returned": "request"
}, {
"name": "streetAddress",
"multiValued": false,
"description": "The street address in which the user is located.",
"idhubFieldName": "officeAddressLine1"
}, {
"name": "temporaryPassword",
"multiValued": false,
"description": "The temporaryPassword of the user. Returned for Creation Only.",
"mutability": "readOnly",
"caseExact": true
}, {
"name": "thumbnailPhotoUrl",
"multiValued": false,
"description": "Photo Url of the user",
"mutability": "readOnly",
"returned": "request"
}
]
}
Entitlement Schema
{
"attributes": [
{
"name": "displayName",
"multiValued": false,
"description": "The displayName of the Entitlement.",
"required": true
}, {
"name": "email",
"multiValued": false,
"description": "The email address of the Group Entitlement",
"returned": "always",
"caseExact": true,
"required": true
}, {
"name": "externalId",
"multiValued": false,
"description": "A String that is an identifier for the resource as defined by the provisioning client.",
"mutability": "readOnly",
"returned": "always",
"caseExact": true
}, {
"name": "id",
"multiValued": false,
"description": "The complex id of the Entitlement.",
"returned": "always",
"caseExact": true,
"required": true
}, {
"name": "meta",
"multiValued": false,
"description": "A complex attribute containing resource metadata.",
"mutability": "readOnly",
"subAttributes": [
{
"name": "resourceType",
"multiValued": false,
"description": "The name of the resource type of the resource.",
"mutability": "readOnly",
"caseExact": true
}, {
"name": "created",
"multiValued": false,
"type": "dateTime",
"description": "The DateTime that the resource was added to the service provider."
}, {
"name": "lastModified",
"multiValued": false,
"type": "dateTime",
"description": "The most recent DateTime that the details of this resource were updated at the service provider. If this resource has never been modified since its initial creation, the value MUST be the same as the value of created."
}, {
"name": "location",
"multiValued": false,
"description": "The name of the resource type of the resource.",
"mutability": "readOnly",
"caseExact": true
}, {
"name": "version",
"multiValued": false,
"description": "The version of the resource being returned.",
"mutability": "readOnly",
"caseExact": true
}
]
}, {
"name": "permissionId",
"multiValued": false,
"description": "Permission ID when an Entitlement is granted to user. This will be used to revoke memberships. It will be returned only during membership creation. Client should save this information and send it to Splice during revocation. This is only applicable when an account is assigned an entitlement. OPTIONAL.",
"caseExact": true
}, {
"name": "requestId",
"multiValued": false,
"description": "A unique ID related to user request. This will be used to avoid duplicate resources created for same request when creating Shared Drive. It is highly recommended that this is populated during shared drive creation. A random UUID will be created if this value is not provided. OPTIONAL.",
"returned": "never",
"caseExact": true
}, {
"name": "schemas",
"multiValued": true,
"description": "The schemas attribute is a REQUIRED attribute and is an array of Strings containing URIs that are used to indicate the namespaces of the SCIM schemas that define the attributes present in the current JSON structure.",
"mutability": "readOnly",
"returned": "always",
"caseExact": true,
"required": true
}
]
}
Deploying the Google Workspace Connector
Deploying using IDHub Connector Onboarding Wizard
Click Here to view more details about how to use IDHub's Cloud Connector Onboarding wizard to deploy the connector.
Deploy on your own
Deploy on Cloud
The documentation for deploying the connector on your own Cloud Platform is coming soon
Deploy on your Server
Prerequisites
- IDHub web hostname.
- An IDHub Tenant.
- A Google Workspace server and its IP address and Port.
- A Google Workspace user account with password which has Read and Write permissions on all user objects of the required OU(s).
- An Ubuntu/Debian Linux VM with Docker engine, Compose plugin, cURL, jq and unzip.
- A service URL with valid certificate which points to port 7001 on the above VM.
Step 1 — Creating Connector OAuth Client (ID)
From IDHub Dashboard, go to Admin Settings > Sign-On > Keycloak Administration and do the following steps.
- Go to Clients menu.
- Create client and set Client ID to ‘Google Workspace-connector’ and Save.
- Set Valid Redirect URIs to '*' and Save.
Step 2 — Create service account user and password in Keycloak in tenant realm
In your Keycloak realm, do the following.
- Go to Users menu.
- Add user.
- Set Username to ‘Google Workspace-service-account’ and Save.
- Go to its Credentials menu and set a password. (Note: For this tutorial, we have used ‘sapassword1’. We highly recommend using a different one for your service account).
Step 3 — Generate Access token and Refresh token
curl --location --request POST 'https://IDHUB_HOSTNAME/auth/realms/TENANT_NAME/protocol/openid-connect/token' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--data-urlencode 'client_id=OAUTH_CLIENT_ID' \
--data-urlencode 'username=SERVICE_ACCOUNT_USER' \
--data-urlencode 'password=SERVICE_ACCOUNT_PASSWORD' \
--data-urlencode 'scope=offline_access' \
--data-urlencode 'grant_type=password' \
--data-urlencode 'request_token_type=urn:ietf:params:oauth:token-type:access_token' \
| jq
Replace the following:
IDHUB_HOSTNAME: The IDHub web hostname. A prerequisite. eg. test.sath.comTENANT_NAME: Tenant that you created in test.sath.com. A prerequisite. eg. alphaOAUTH_CLIENT_ID: OAuth Client ID you created in Step 1.SERVICE_ACCOUNT_USER: Service account username you created in Step 2.SERVICE_ACCOUNT_PASSWORD: Service account password you created in Step 2.
We now have our tokens. Let’s deploy the connector.
Step 4 — Prepare the .env file
- Clone the IDHub’s AD Connector repository and edit the .env file.
wget https://storage.googleapis.com/sath-public-binaries/connectors/idhub-google-workspace-connector.zip
unzip idhub-google-workspace-connector.zip
cd idhub-google-workspace
nano .env
BUSINESS_OWNER=ADMIN_EMAIL
IT_OWNER=ADMIN_EMAIL
DOMAIN_URL=GOOGLE_DOMAIN_URL
ADMIN_EMAIL=ADMIN_EMAIL
SERVICE_ACCOUNT=SERVICE_ACCOUNT_EMAIL
CONNECTOR_DEBUG_LEVEL=DEBUG
IDHUB_HOSTNAME=example.iamsath.com
KEYCLOAK_ACCESS_TOKEN=ACCESS_TOKEN
KEYCLOAK_CLIENT_ID=Entra ID-connector
KEYCLOAK_REFRESH_TOKEN=REFRESH_TOKEN
KEYCLOAK_REALM=TENANT_NAME
SPLICE_DEBUG_LEVEL=DEBUG
PORT=CONNECTOR_PORT
GOOGLE_CERT=GOOGLE_CERT_PATH
GOOGLE_CERTIFICATE=GOOGLE_CERT_VARIABLES
Replace the following:
IDHUB_HOSTNAME: IDHub web hostname. From prerequisites. eg. test.sath.comACCESS_TOKEN: From Step 3 output. Put it WITHOUT the quotes.REFRESH_TOKEN: From Step 3 output. Put it WITHOUT the quotes.KEYCLOAK_CLIENT_ID: From Step 1.TENANT_NAME: Tenant created in IDHub. From prerequisites. eg. alphaGOOGLE_WORKSPACE_SERVER_IP_ADDRESS: From prerequisites. eg. 10.128.6.87GOOGLE_WORKSPACE_SERVER_PORT: From prerequisites. eg. 389 or 636CONNECTOR_PORT: Google Workspace connector port which you are planning to run on. The Service URL points to this port.GOOGLE_CERT: Add the Google certificate path here.GOOGLE_CERTIFICATE: Add the Google Certificate variables here.
Step 5 — Run the container
- In the connector directory, run the following command.
docker compose up -d