HIPAA Case Study
Introduction
One healthcare provider that has used IDHub to improve its HIPAA compliance is a large hospital system. The hospital system had a number of challenges with its HIPAA compliance, including:
- The hospital system had a complex IT environment with a variety of different systems and applications.
- The hospital system had a large number of users, including staff, contractors, and volunteers.
- The hospital system had a number of different access policies that needed to be enforced.
- The hospital system had lack of visibility into who had access to PHI
- The hospital system had manual and inefficient access certification process
The hospital system implemented IDHub to help it to address these challenges. Let’s take a deeper look into how the hospital was able to solve these challenges using IDHub.
Single View of All Users & their Access Privileges
IDHub provided the hospital system with a single view of all users and their access privileges across all systems and applications. This visibility helped the hospital system to identify and remediate any access risks. IDHub also helped the hospital system to automate the process of requesting and approving access to systems and applications. This helped the hospital system to ensure that only authorized individuals have access to PHI.
How can you approve request for access to Applications in IDHub?
After onboarding applications, users can request for access. The access request goes through the applicable workflow of the application.
For example, As can be seen in the screenshot below, the access request for an application is assigned to the manager of the beneficiary as this is a manager approval workflow. You can review the details of the request by going to the Track Request menu and then clicking on the request card.
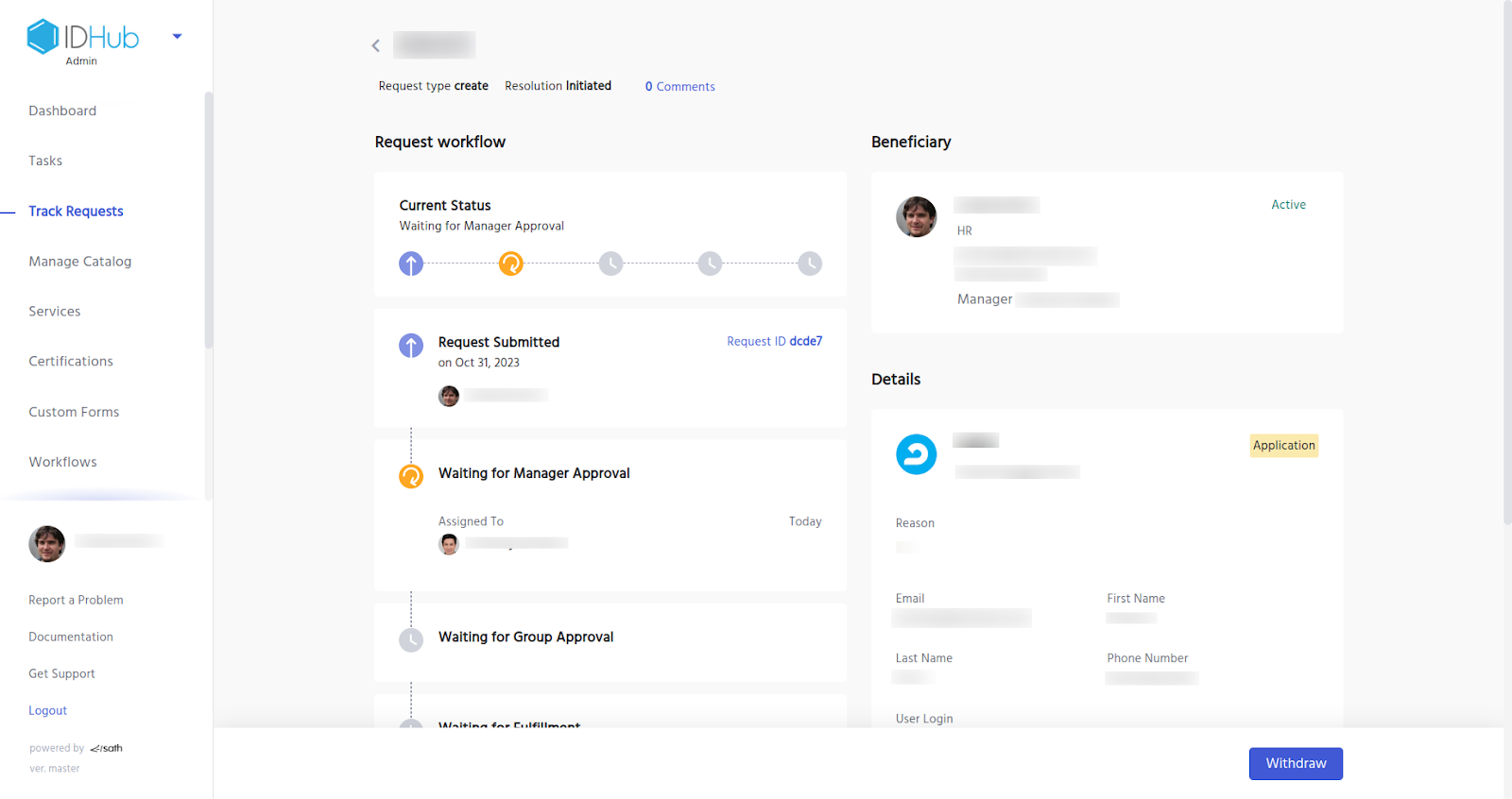
Now the manager will get a task which he can either approve or reject the request, as can be seen in the screenshot below.
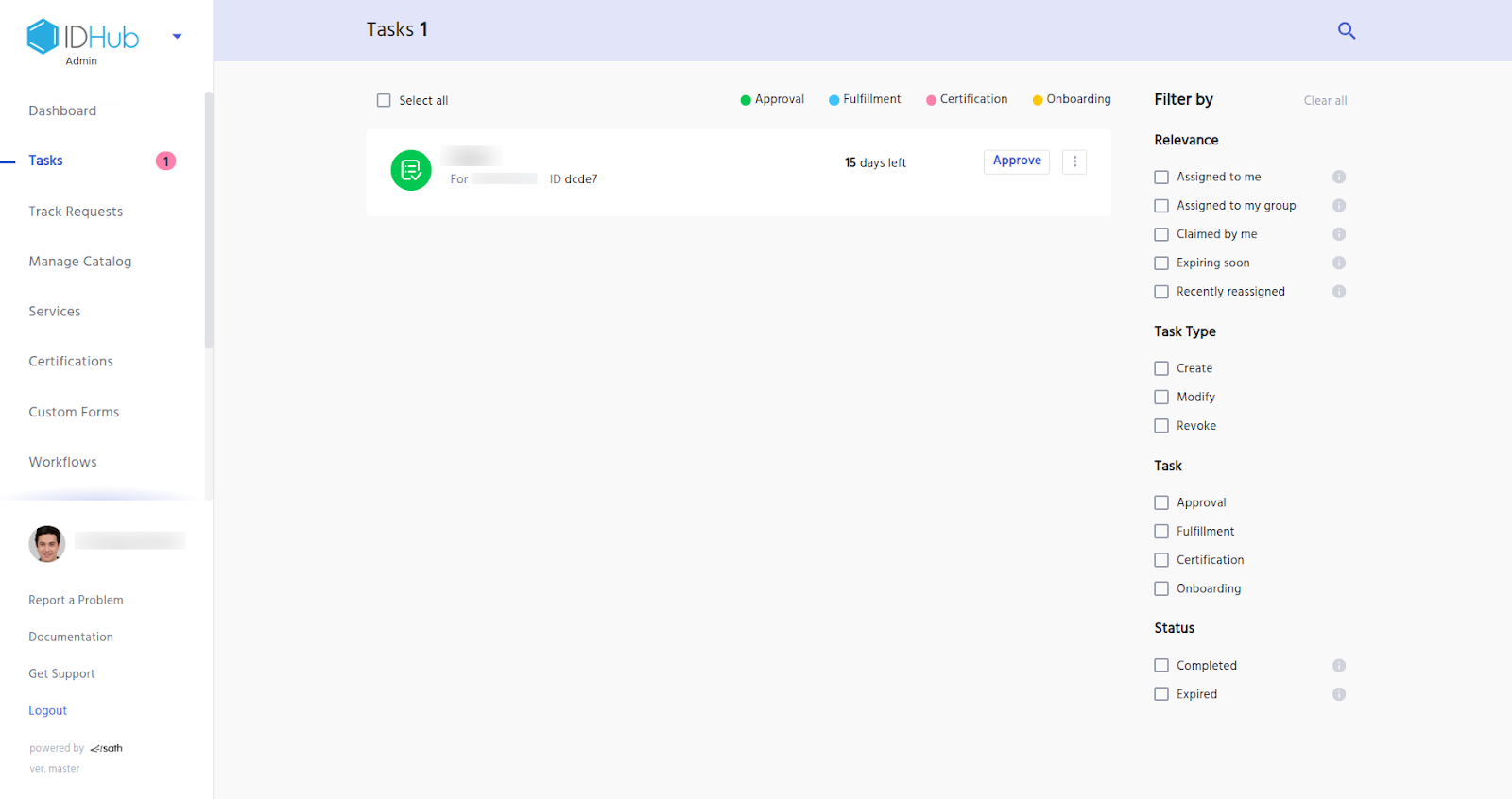
Once the request is completed, the account would be provisioned for the beneficiary.
Role Based Access Control
IDHub helped the hospital in implementing their HIPPA compliance using RBAC. This helped the hospital to identify and mitigate risks to PHI. Therefore, hospital was able to:
- Identify high-risk users and systems
- Prioritize access reviews for high-risk users and systems
- Automate the process of performing role based control to data.
These approaches helped the hospital to focus their resources on the areas where they are most needed and therefore conforming and implementing one of the critical conditions of HIPAA conformance postures.
How to Request for Role?
You can Request for role, same way you can request access to applications / entitlements. Some roles are given to the users by birth-right due to the conditions defined in the role. For example: You can define a role for Claims processing such that all the users who are in your department of claims processing will automatically get the related applications or entitlements defined in the role.
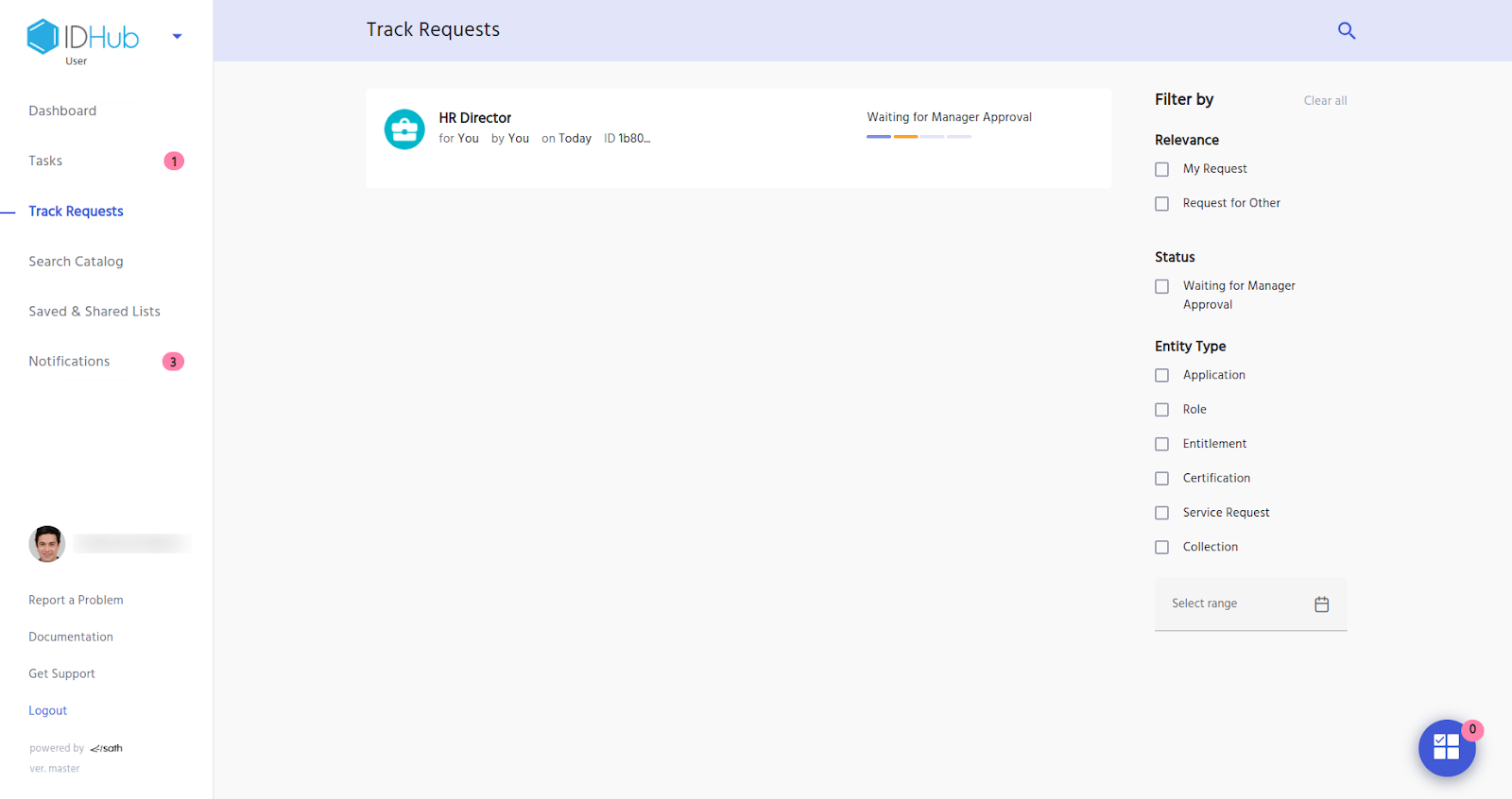
For example: As can be seen in the screenshot below, this shows a request for a role and is currently waiting for the manager approval. Once the request is completed, then the role would be provisioned for the beneficiary.
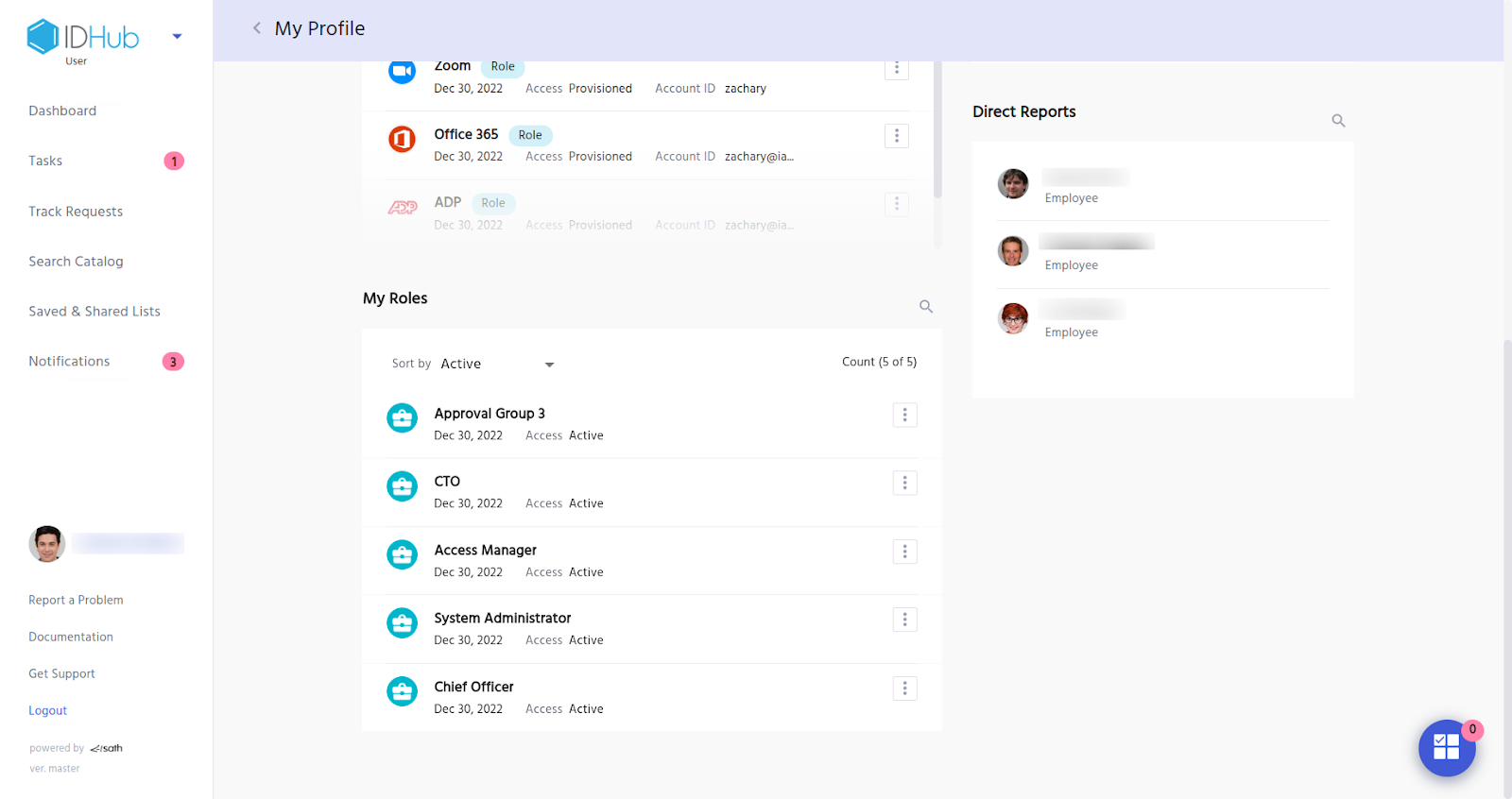
The screenshot below shows the profile of the user who has different roles assigned to him.
Automated access certifications
IDHub helped the hospital to automate the process of access certifications. This helped them to ensure that users only have the access to PHI that they need to do their job. Therefore, the hospital was able to:
- Automate the process of sending out access certification requests
- Automate the process of collecting and reviewing access certification responses
- Identify all the systems and applications that contain PHI
- Identify all the users who have access to PHI
- Understand what type of access each user has to PHI
This automation can help healthcare providers to save time and resources, while also improving their HIPAA compliance posture.
How to run the certificate and review certification tasks?
Once you have created the certification task, you need to run the certificate. For that click on the certificates menu in the left hand side panel of IDHub admin app and then click on the 3 dots menu for the certificate that you want to run.
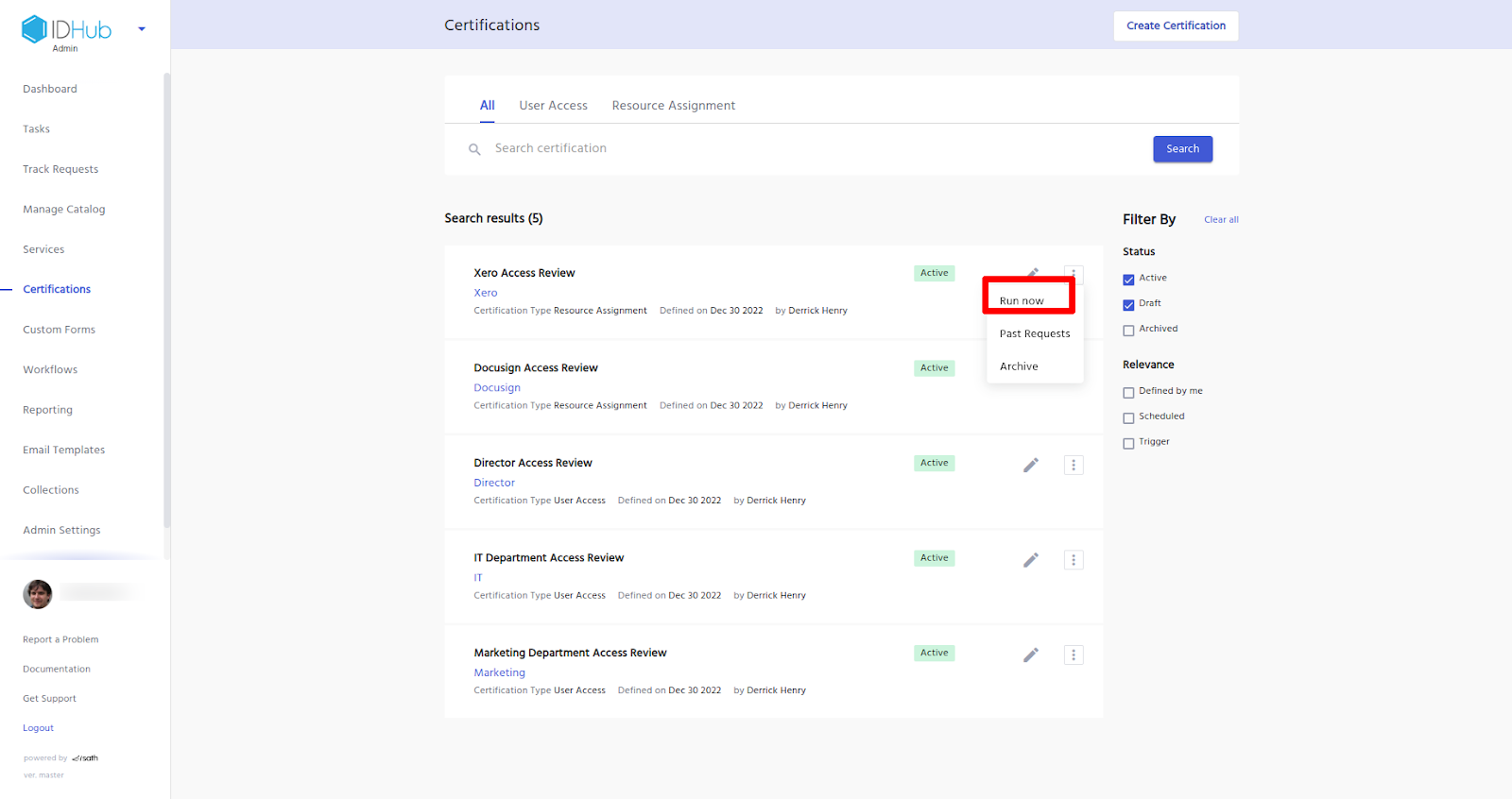
This will generate the certification tasks for the certifier, to review and approve as is shown below:
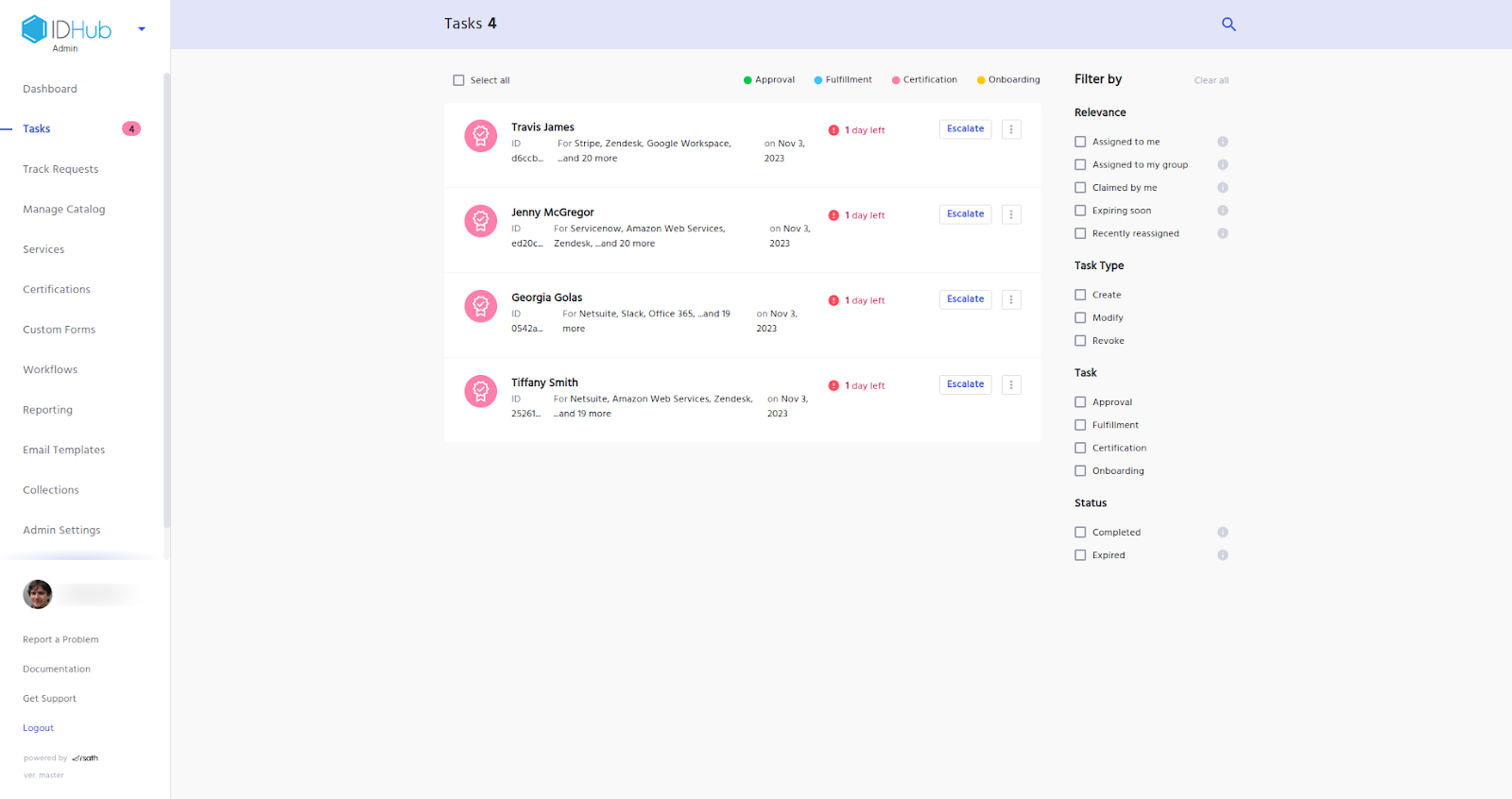
For each certification task the certifier can either certify or revoke access to the resources, as is shown below:
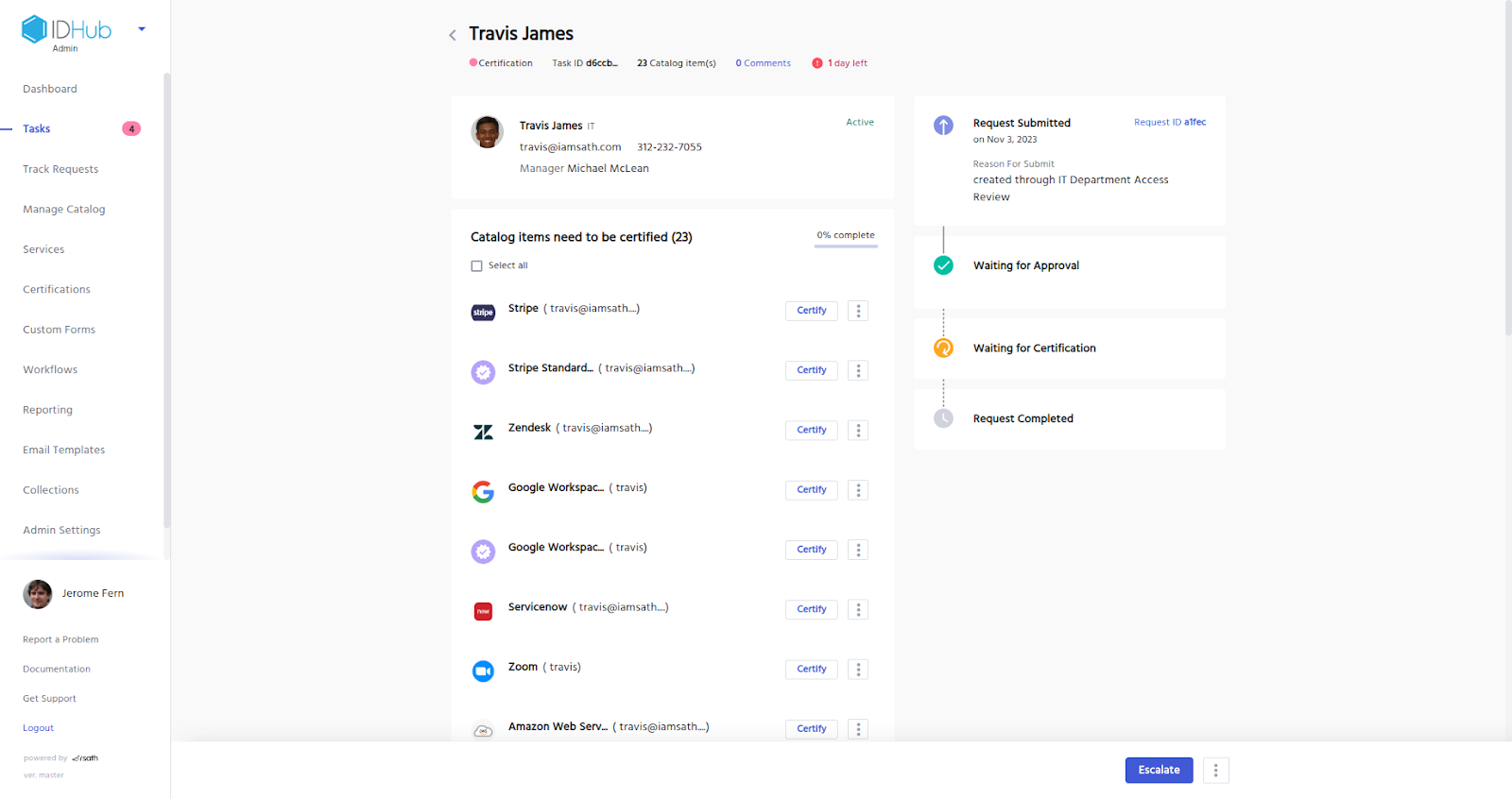
Once the certifier finishes certifying (or revoke) access to the catalog items, the certification task is completed, the certifier can click on the submit button and the task would be completed accordingly. If the certifier decides to do the revocation for one or more of the catalog items, then in that case, the de-provisioning of the account for those catalog items would be triggered. The de-provisioning would be processed as per the workflow of the item.
Enforcing access policies using workflow
IDHub helped the hospital to enforce their access policies by creating and defining their own workflow. This ensures that users can only access the PHI that they are authorized to access. Therefore, IDHub helped the hospital to:
- Define and enforce access policies using IDHub workflow for all of their systems and applications
- Monitor user activity to ensure that users are complying with access policies
This enforcement of access policies can help healthcare providers to prevent unauthorized access to PHI and protect their patients' privacy.
How to create your own workflow?
In order to create and define your own workflow,Click on the workflows section in the IDHub admin panel and then click on the create workflow button.
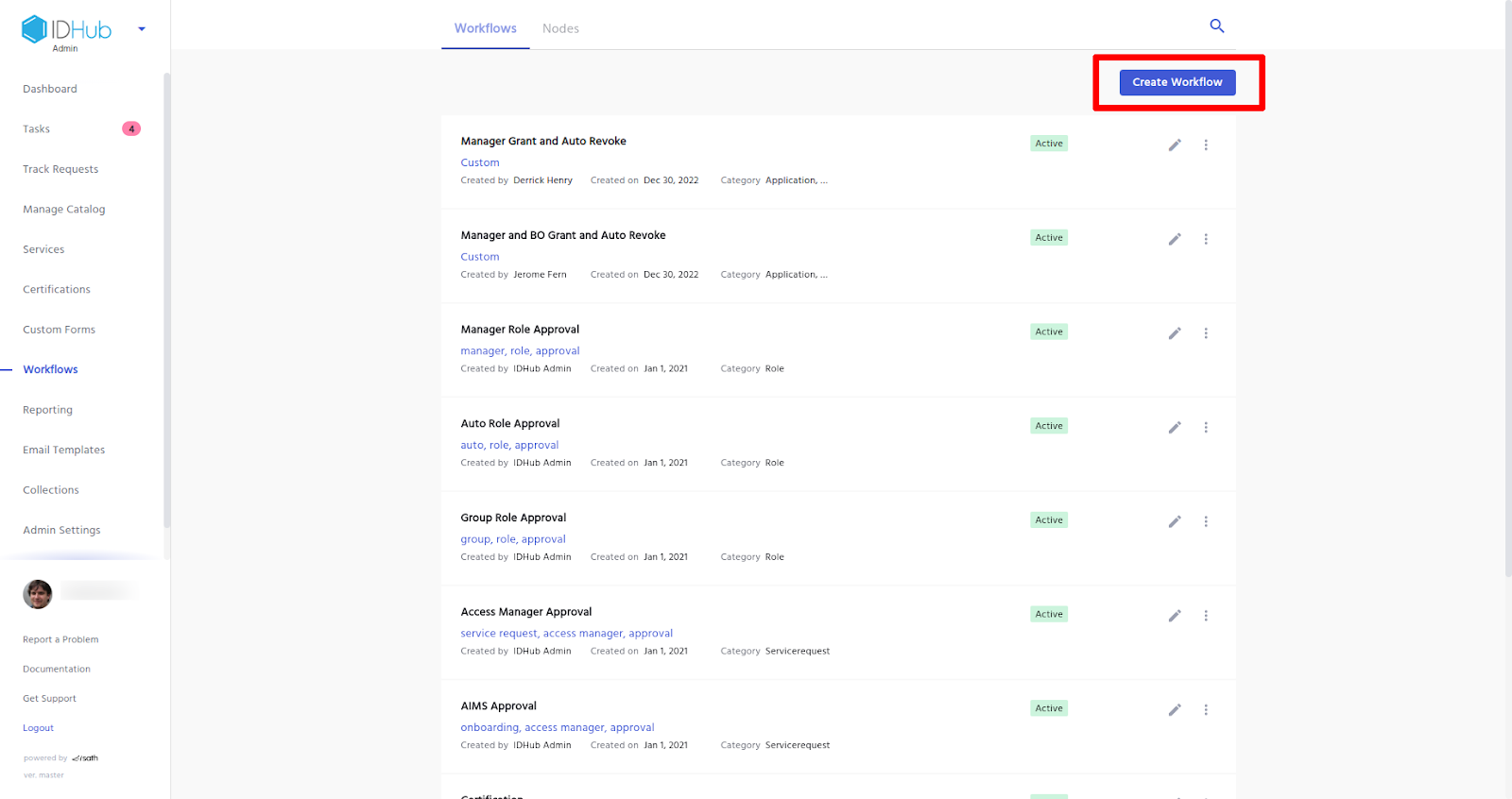
After that you can create and define your own workflow and then use that workflow in your on-boarded applications. Click here to learn more about how to create a workflow.
Auditing
IDHub helped the hospital to audit and track their compliance with HIPAA. This helped them to identify and address any gaps in their compliance posture. Therefore, the hospital was essentially able to:
- Generate audit reports on user activity
- Generate reports on access certifications
- Generate reports on access policy compliance
These reports can help healthcare providers to demonstrate their compliance with HIPAA to auditors and regulators.
Conclusion
IDHub is a powerful and top of the line IAM solution that helped the hospital to be HIPAA-compliant. As a result of implementing IDHub, the hospital system was able to significantly improve its HIPAA compliance. The hospital is able to enforce its access policies and monitor and audit access to PHI to ensure that it is only accessed in a compliant manner. The hospital system now has a clear understanding of who has access to what, and it is able to ensure that only authorized individuals have access to PHI.