FFIEC Compliance Case Study
Introduction
Financial institutions (FIs) are subject to a variety of compliance regulations, including those set forth by the Federal Financial Institutions Examinations Council (FFIEC). The FFIEC is a body of the United States government that is responsible for ensuring the safety and soundness of the financial system. One of the FFIEC's key objectives is to protect consumers from identity theft and fraud.
To comply with FFIEC regulations, FIs must implement a number of controls, including access management controls. Access management controls are designed to ensure that only authorized individuals have access to sensitive data. IDHub is an access management solution that can help FIs comply with FFIEC regulations.
Case Study
A large financial institution was facing a number of challenges in complying with FFIEC regulations. The FI had a complex IT environment with a large number of users and systems. The FI also had a manual access certification process that was time-consuming and error-prone.
Challenges
Financial institutions face a number of challenges in complying with FFIEC standards. These challenges include:
- The ever-evolving threat landscape
- The increasing complexity of financial institution systems and networks
- The need to comply with a multitude of regulations
- The lack of visibility into user access and activity
To address these challenges, the FI implemented IDHub. IDHub automated the FI's access certification process and provided the FI with a centralized view of all user access. IDHub also helped the FI to identify and remediate unauthorized access.
Benefits
Financial institutions can achieve a number of benefits by implementing IDHub, including:
- Reduced compliance costs: IDHub can help financial institutions to reduce compliance costs by automating the IAM process and providing visibility into user access and activity.
- Improved security: IDHub can help financial institutions to improve security by preventing unauthorized access to systems and data.
- Increased productivity: IDHub can help financial institutions to increase productivity by automating the IAM process and reducing the time it takes to provision and deprovision access.
Let’s take a deeper look into how the hospital was able to solve these challenges using IDHub.
Addressing the Challenges Faced
Automated access provisioning and de-provisioning
IDHub can automatically provision and de-provision access to systems and data based on user roles and entitlements. This helped the FI to ensure that only authorized users have access to the resources they need to do their jobs.
How does automated provisioning/de-provisioning works?
Once you on-board a connected application to IDHub you can run or schedule the Application Sync (recon) which will do the automated provisioning (or de-provisioning of the accounts). To do this you need to Go to Manage Catalog in the Admin Module of IDHub using the credentials of a user that has the role of System Administrator with them. Upon reaching the manage catalog click on any Application's more options and then click on the Application Sync menu
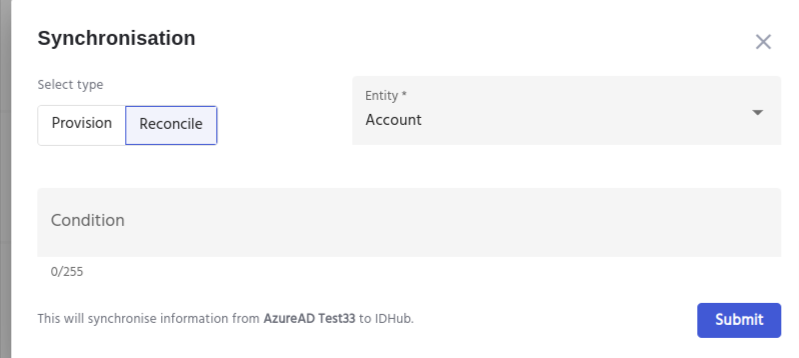
IDHub would show a confirmation window. Click on the Yes button and this will start the process of reconciliation. Once the Reconciliation is started, IDHub shows the Sync in Progress status in the application card.
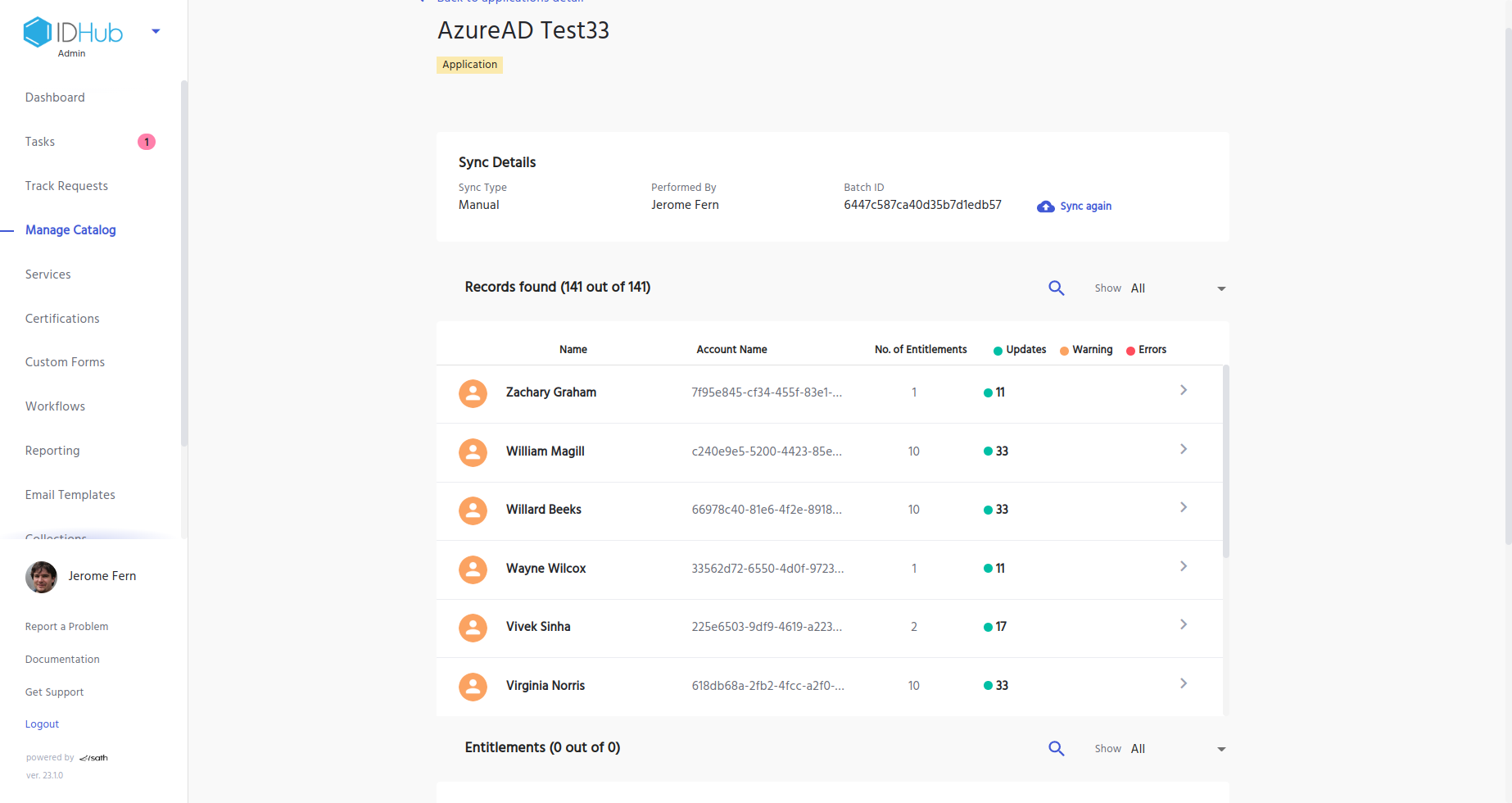
Viewing the details
Once the reconciliation process is completed, click View from the application's Reconciliation log tab. From there you would be able to see the Reconciliation details and the details of the records (Attributes/Entitlements) which have been updated. See below:
Access certification
IDHub helped the FI to certify access to systems and data on a regular basis. Therefore they were able to identify and remove unauthorized access.
How to run the certificate and review certification tasks?
Once you have created the certification task, you need to run the certificate. For that click on the certificates menu in the left hand side panel of IDHub admin app and then click on the 3 dots menu for the certificate that you want to run.
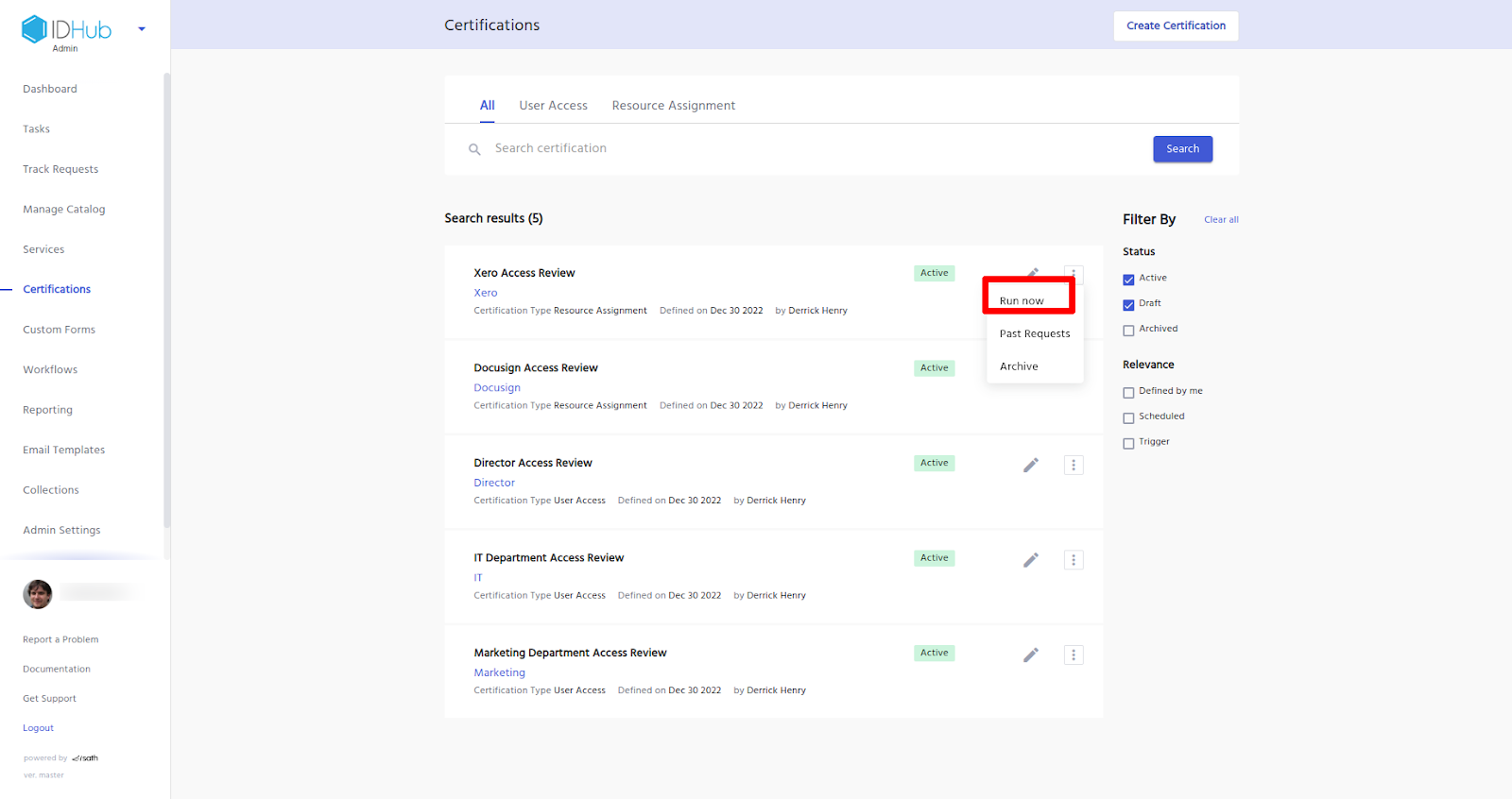
This will generate the certification tasks for the certifier, to review and approve as is shown below:
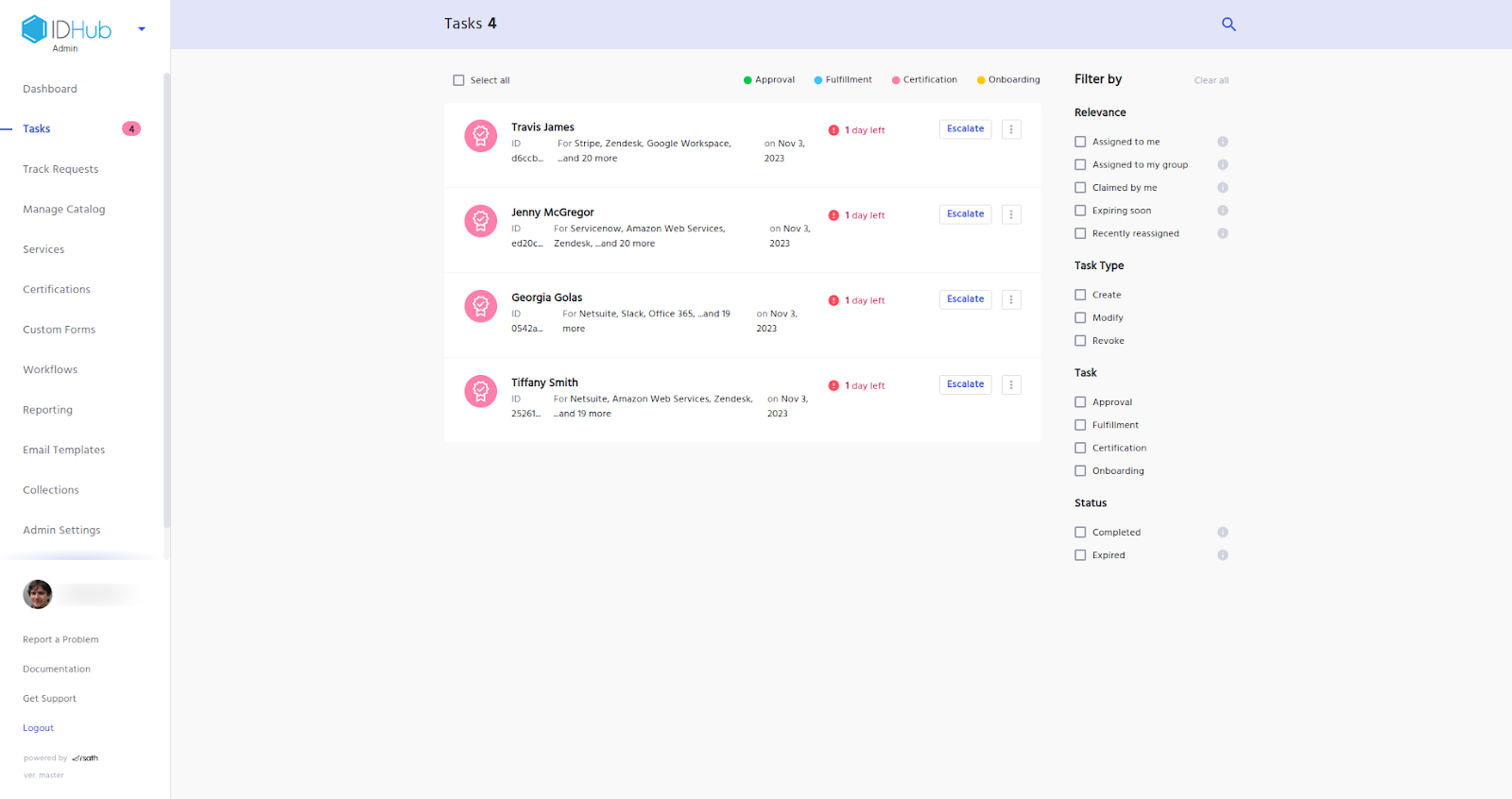
For each certification task the certifier can either certify or revoke access to the resources, as is shown below:
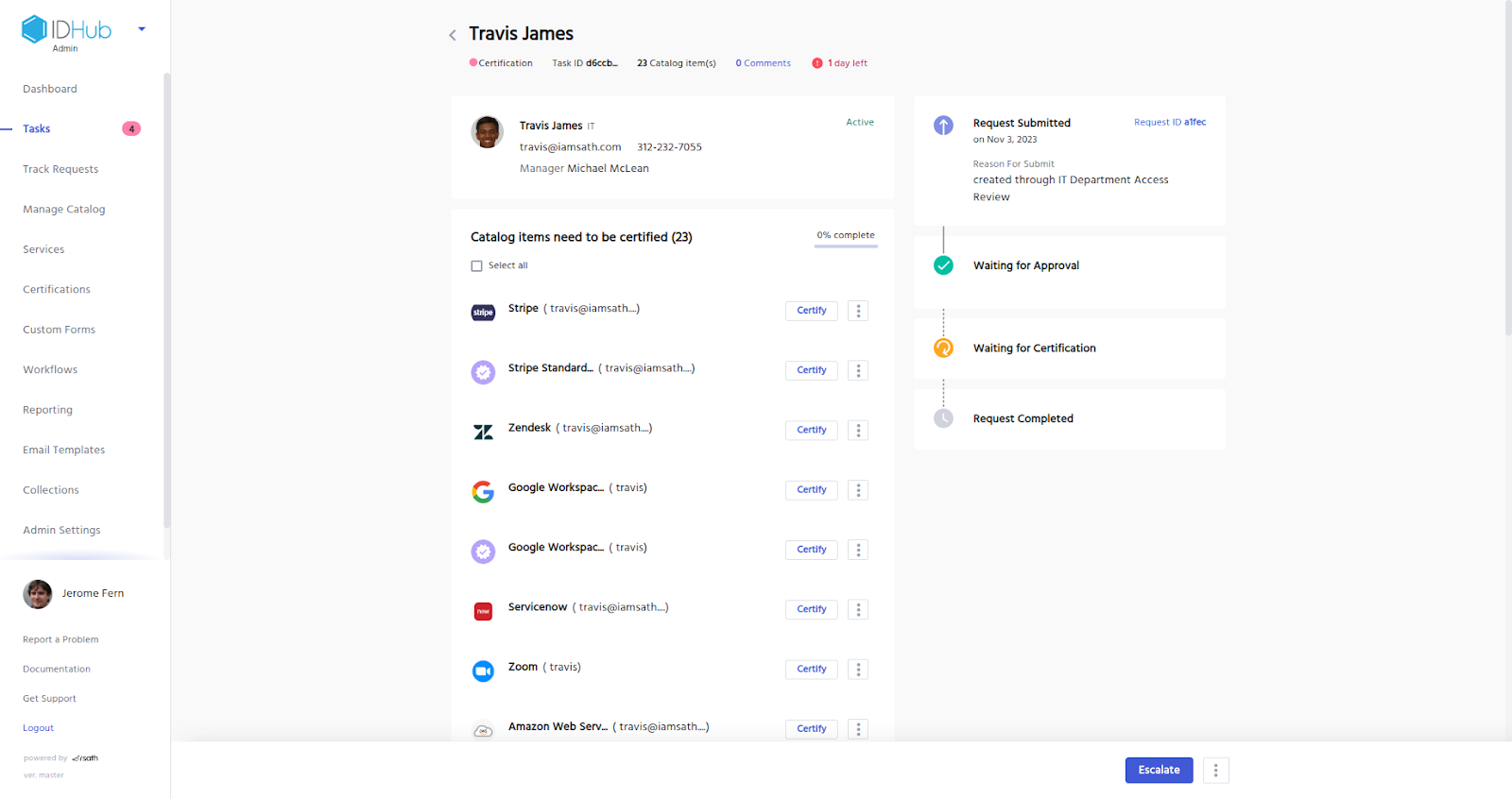
Once the certifier finishes certifying (or revoke) access to the catalog items, the certification task is completed, the certifier can click on the submit button and the task would be completed accordingly. If the certifier decides to do the revocation for one or more of the catalog items, then in that case, the de-provisioning of the account for those catalog items would be triggered. The de-provisioning would be processed as per the workflow of the item.
Click here to learn more about how to create a certificate.
User activity monitoring:
IDHub can monitor user activity in real time. This helped the FI TO detect and prevent unauthorized access and data breaches.
Therefore, the FI were able to use IDHub to generate a report of all users who have accessed a particular financial record.
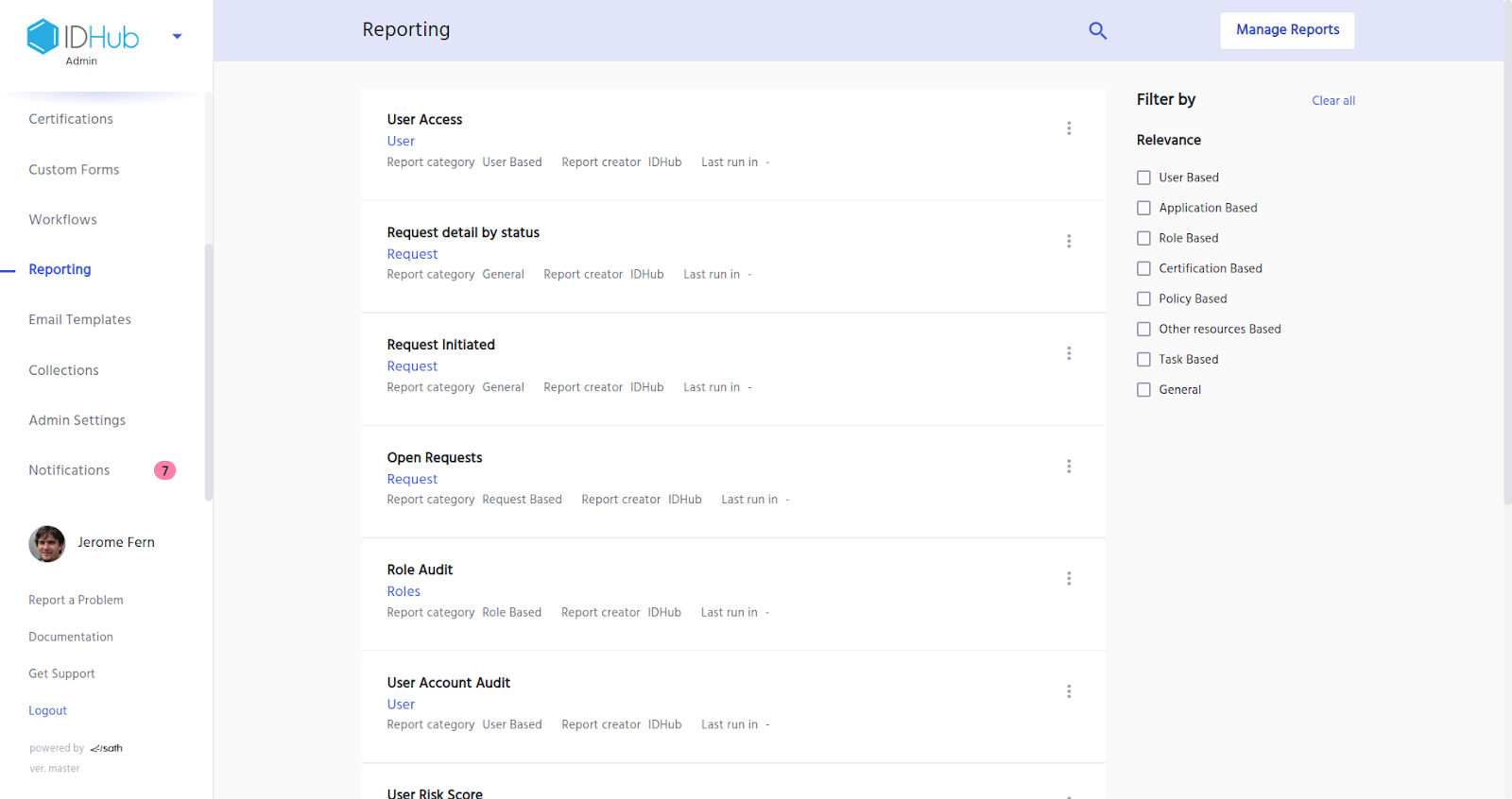
For accessing these reports click on reporting under the IDHub admin app as is shown below:
Time Based Access Request
IDHub helped the FI to quickly revoke access to certain high risk applications after a certain time. The FI had the requirement that some employees needed temporary access to an AWS group for doing some tasks for a limited period of time. IDHub catered to this requirement by providing the time-based access feature.
For requesting access to the AWS group, go to the search catalog and search for the entitlement for which you want to request access.
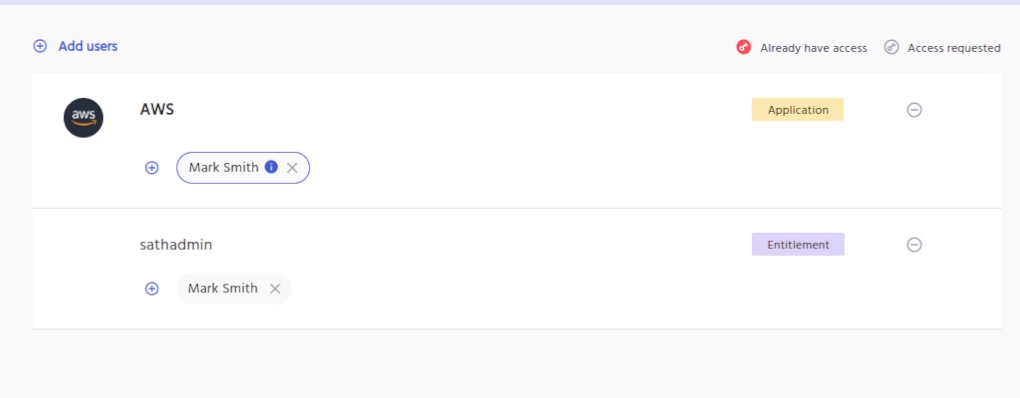
As shown in the screenshot above, the access request to an AWS group is added. Once you click on the continue button it would show a RHS. The RHS would have an access revoke field as is shown in the screenshot below.
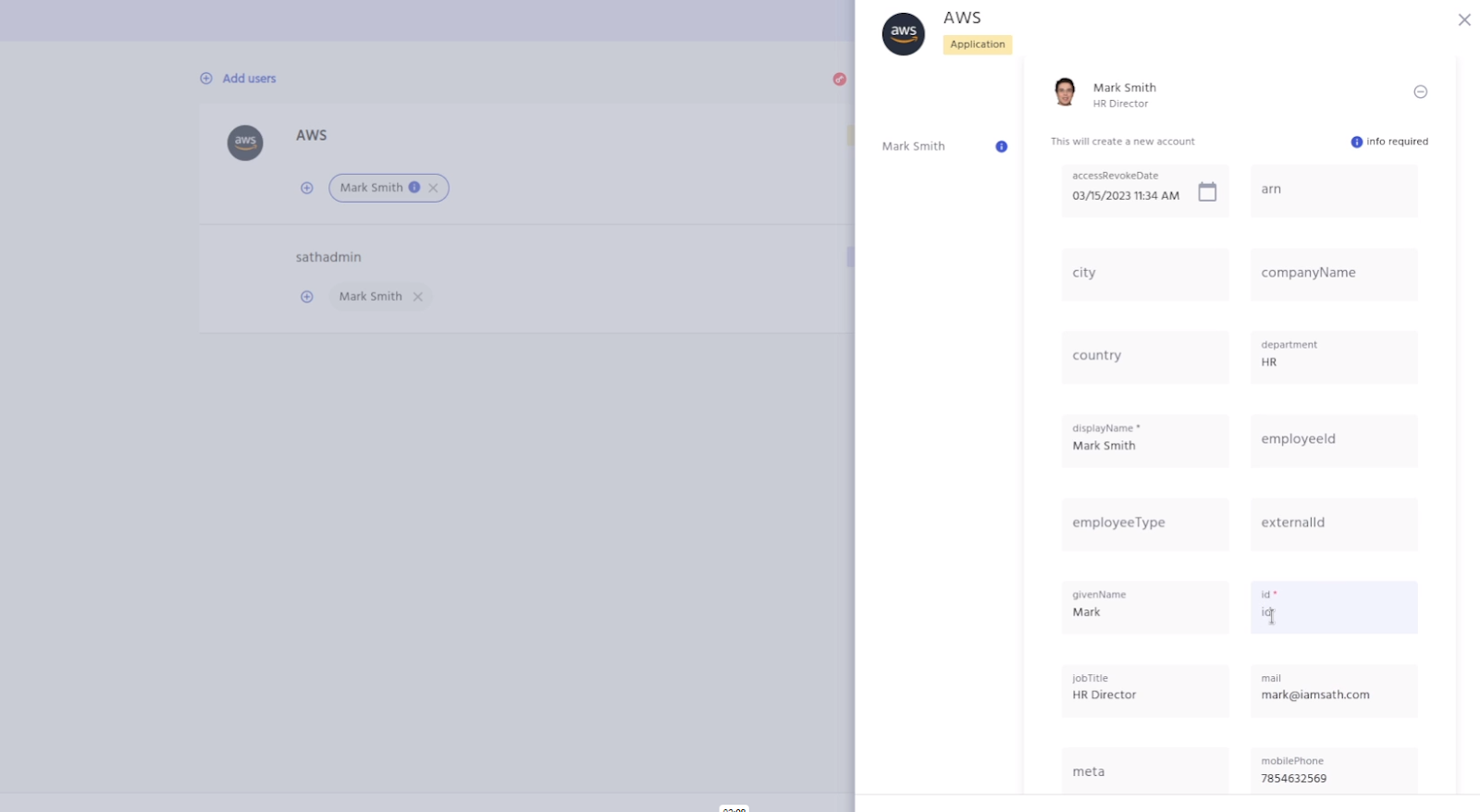
Now click on the access revoke field and it will show the date and time. Select the time from the dropdown (in this case you can select 1 hour, if you want to request access for 1 hour). And then go ahead and complete the form and submit the request for access. Once the request for access is completed, IDHub would automatically provision the entitlement (AWS group) for the user for 1 hour. Once the 1 hour time has elapsed, IDHub would automatically de-provision (revoke) the entitlement from the user. This helped the FI in meeting the FFIEC compliance requirement, which basically ensured that only authorized users are given access to sensitive target system resources and permissions and that too for a limited period of time.
Conclusion
By implementing IDHub the FI was able to confirm to the FFIEC compliance requirements. Leveraging various features of IDHub including access requests, certifications, time-based access requests, reporting etc. The FI was able to significantly reduce the data theft risks, therefore reducing their compliance costs, increased productivity and improving their overall security posture of their entire IT infrastructure.