Right Access for Right People to Right Systems
Simply powerful identity management
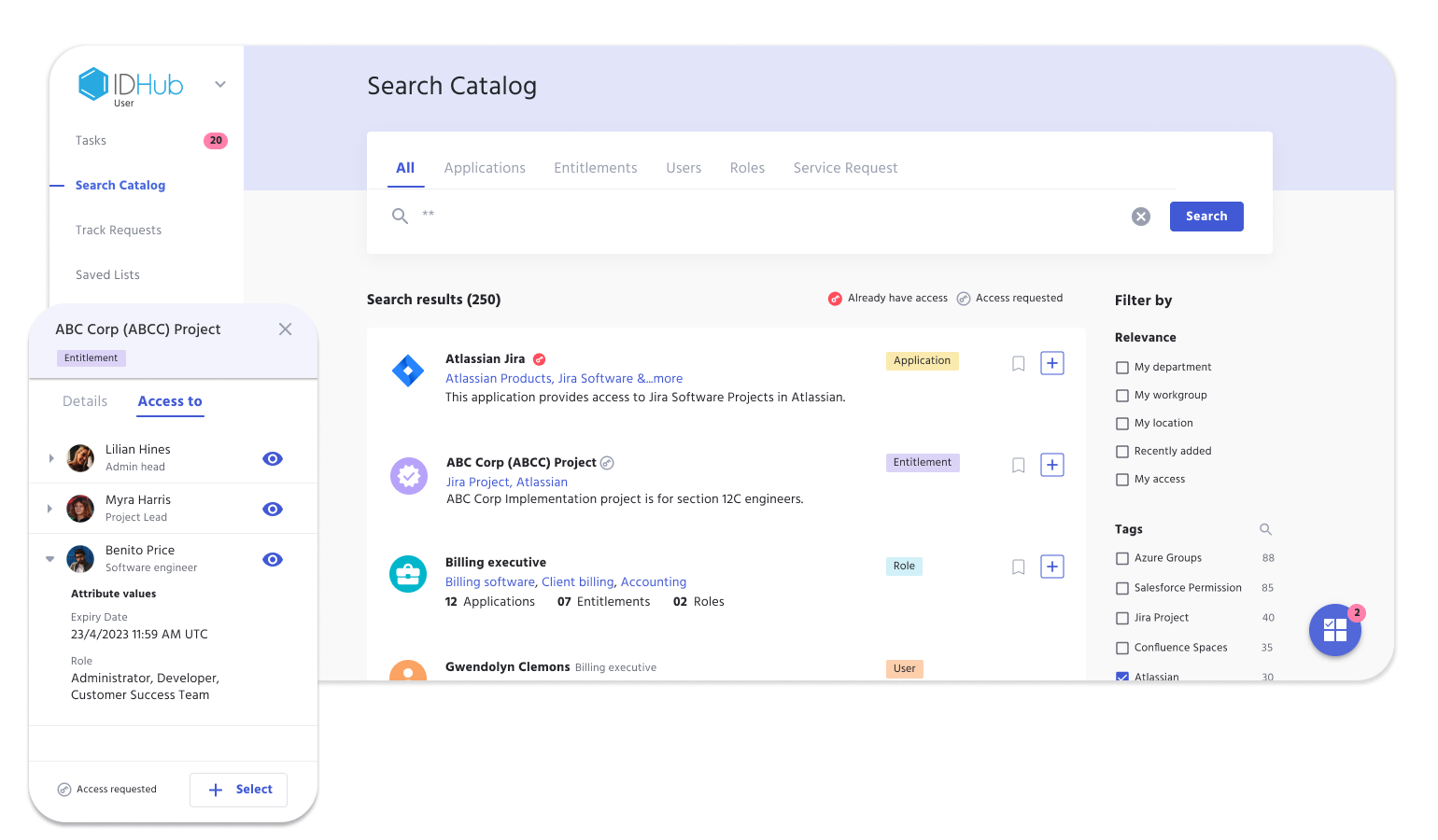
Sath's flagship product IDHub is an Identity and Access Management solution that safeguards sensitive data, prevents unauthorized access, and maintains regulatory compliance by managing and controlling user identities and access privileges.
IAM Solution
Identity and Access Management
Identity and Access Management (IAM) is a comprehensive framework that ensures the right access, to the right people, to the right systems and resources, while maintaining security, compliance, and operational efficiency.
IAM involves managing user identities, controlling access permissions, and enforcing policies to protect sensitive information throughout the entire user lifecycle.
IDHub is full Identity Access Management IAM solution providing businesses with the tools they need for user access management success, while enabling direct-to-work capabilities with advanced Identity Governance features.
Administer
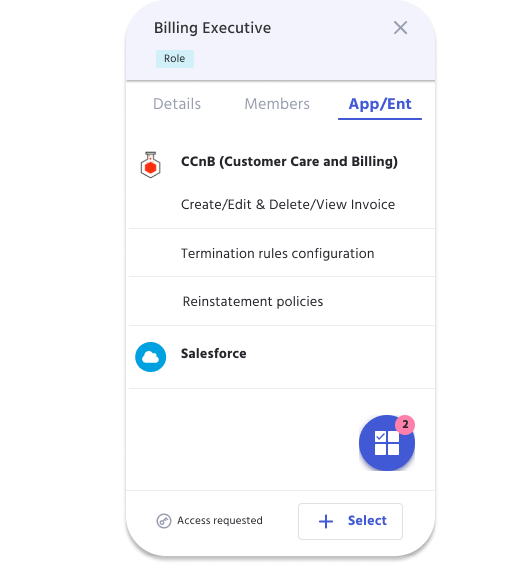
Application Management
Organizations must ensure every stakeholder has the correct type of system access. IDHub makes onboarding and managing applications, permissions, and entitlements a breeze.
Provision
Automated Provisioning
Automatically create, modify, or disable user accounts and associated access rights and permissions based on predefined rules, policies, or event within your organization.
IGA Solution
Identity Governance and Administration
User Access Review
Streamline your process for reviewing user permissions and entitlements, to ensure they only have the access they need. See how IDHub audits user access instantly or scheduled, with customizable Certification Access Reviews.
Role Based Access Control
Managing user access with Role Based Access empowers organizations to provide their employees with job specific permissions from day 1, and quickly deprovision and provision access when job requirements change.
Compliance Management
Auditing user access in highly regulated industries always seems to be a challenge. IDHub simplifies that process with Reporting, as it has capabilities to customize organizational compliance needs, regardless of the sector.
IDHub Advanced IGA Features
Identity Governance
Simple Setup and Use
No-Code Setup
Get up and running with no technical expertise. Get user access management and meet compliance with our no-code solution.

Low-Code Customizations
IDHub empowers admins to create the perfect solution, tailored to accommodate the exact Approval Workflows they need.

IDHub by Sath
Why choose us?

Ease Of Use
Simplicity of implementation, strengthens user adoption and security governance.

Customizable
Rule-based configuration enables solution tailoring, to fit any company's needs.

Save Time
Seamless application integrations provide maximum control, in minimal time.

Save Money
Automate provisioning to save money in IT costs and personnel needs.
Our Portfolio
Trusted by Fortune 500 Companies
We built our business with quality communication and strong relationships. Listed below are a few companies in our portfolio.












